AWS Certified Security – Specialty An overview Simon Whittaker Cyber Security Director - Vertical Structure Ltd
Slide 1

Slide 2
Prepare, Protect, Persist ® • Prepare • We help you and your partners to understand how to identify and resolve potential security issues at the earliest stages with hands on 'hack yourself first', threat modelling and GDPR compliance workshops as well as security training for non-technical colleagues. • Protect • Using automated and manual penetration testing techniques, we provide a comprehensive security report for your Web and mobile applications, including API testing, and networks. The report highlights potential issues and their resolutions. • Persist • We ensure that your organisation benefits from continual improvements in security levels through information assurance processes, auditing and certification including ISO27001:2013 and Cyber Essentials. © Vertical Structure Ltd where applicable [email protected]
Slide 3
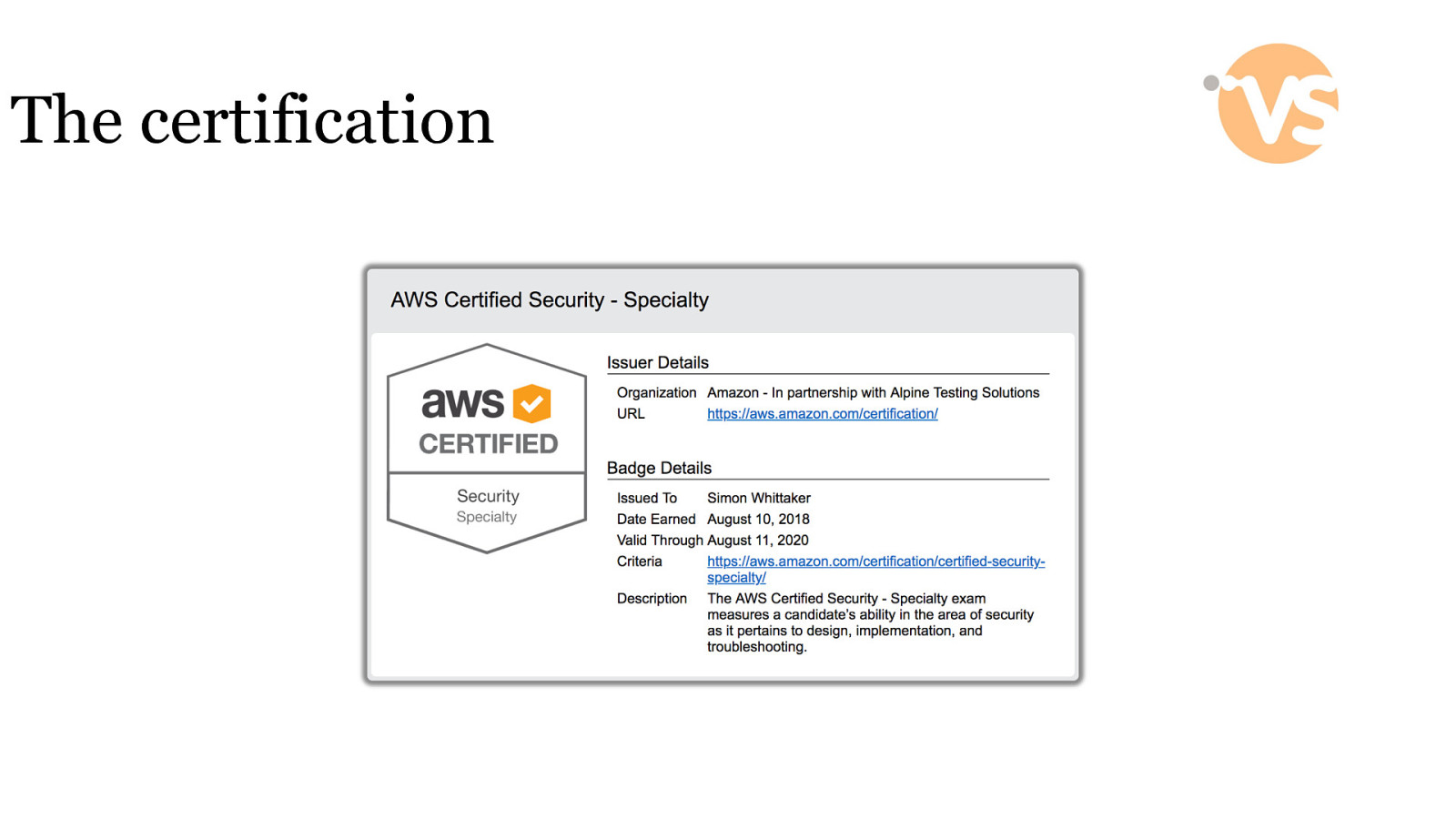
The certification
Slide 4
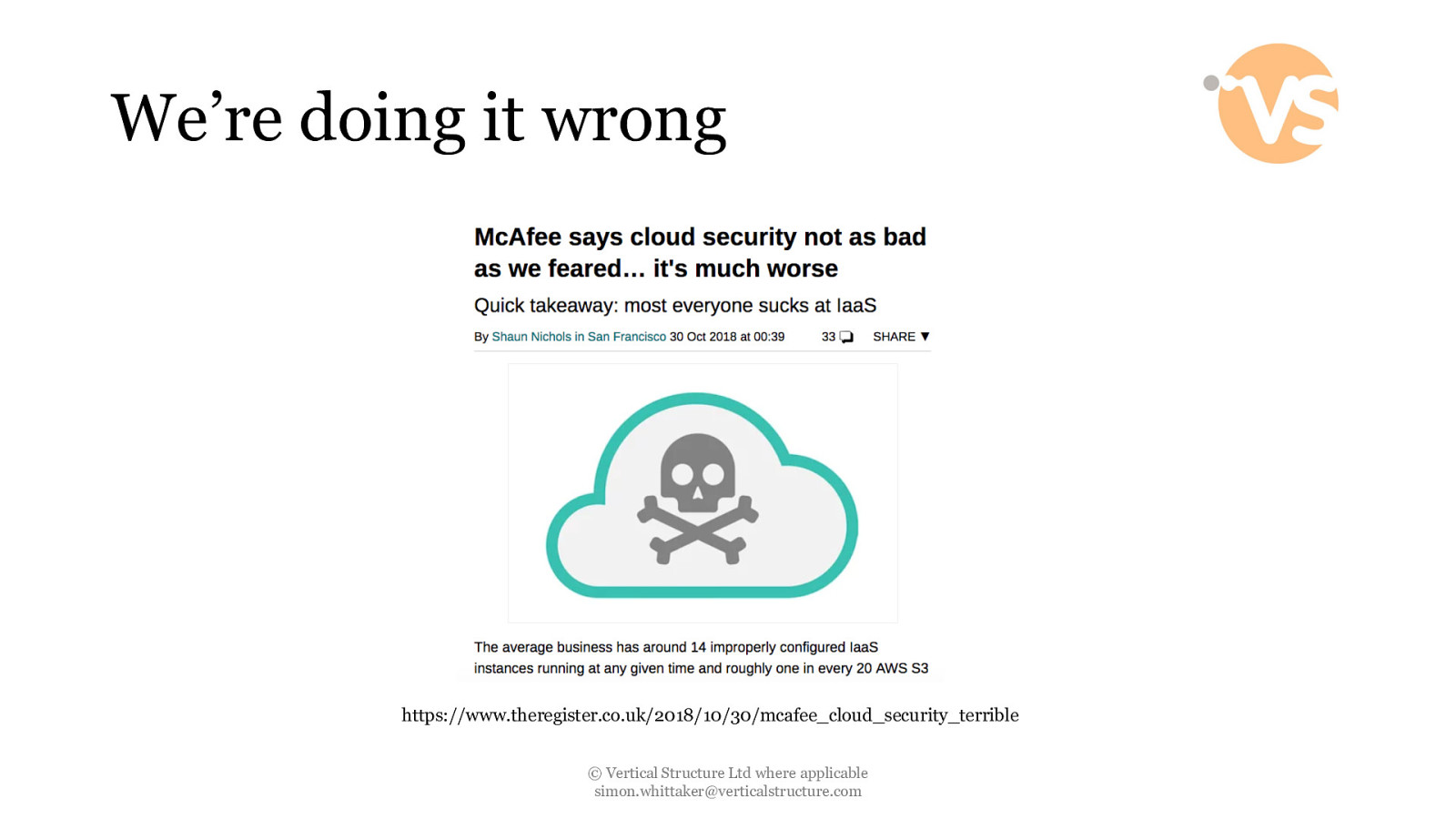
We’re doing it wrong https://www.theregister.co.uk/2018/10/30/mcafee_cloud_security_terrible © Vertical Structure Ltd where applicable [email protected]
Slide 5

Lies, damn lies and statistics • 14 improperly configured IaaS instances running at any given time • Roughly one in every 20 AWS S3 buckets are left wide open to the public internet • The average business uses around 1,900 cloud instances, but most of the companies they surveyed only thought they used around 30 We’re doing it wrong https://www.theregister.co.uk/2018/10/30/mcafee_cloud_security_terrible © Vertical Structure Ltd where applicable [email protected]
Slide 6
Example Elasticsearch is a search engine based on Lucene. It provides a distributed, multitenant-capable full-text search engine with an HTTP web interface and schema-free JSON documents. https://en.wikipedia.org/wiki/Elasticsearch © Vertical Structure Ltd where applicable [email protected]
Slide 7

Elasticsearch in AWS © Vertical Structure Ltd where applicable [email protected]
Slide 8

Access Restrictions • Resource based • Assigned access to a account, user or role to a domain in AWS • Identity based • Assigned access to a account, user or role to a domain in AWS • Tend to be more generic • IP based • Anyone from the right IP can access anything © Vertical Structure Ltd where applicable [email protected]
Slide 9
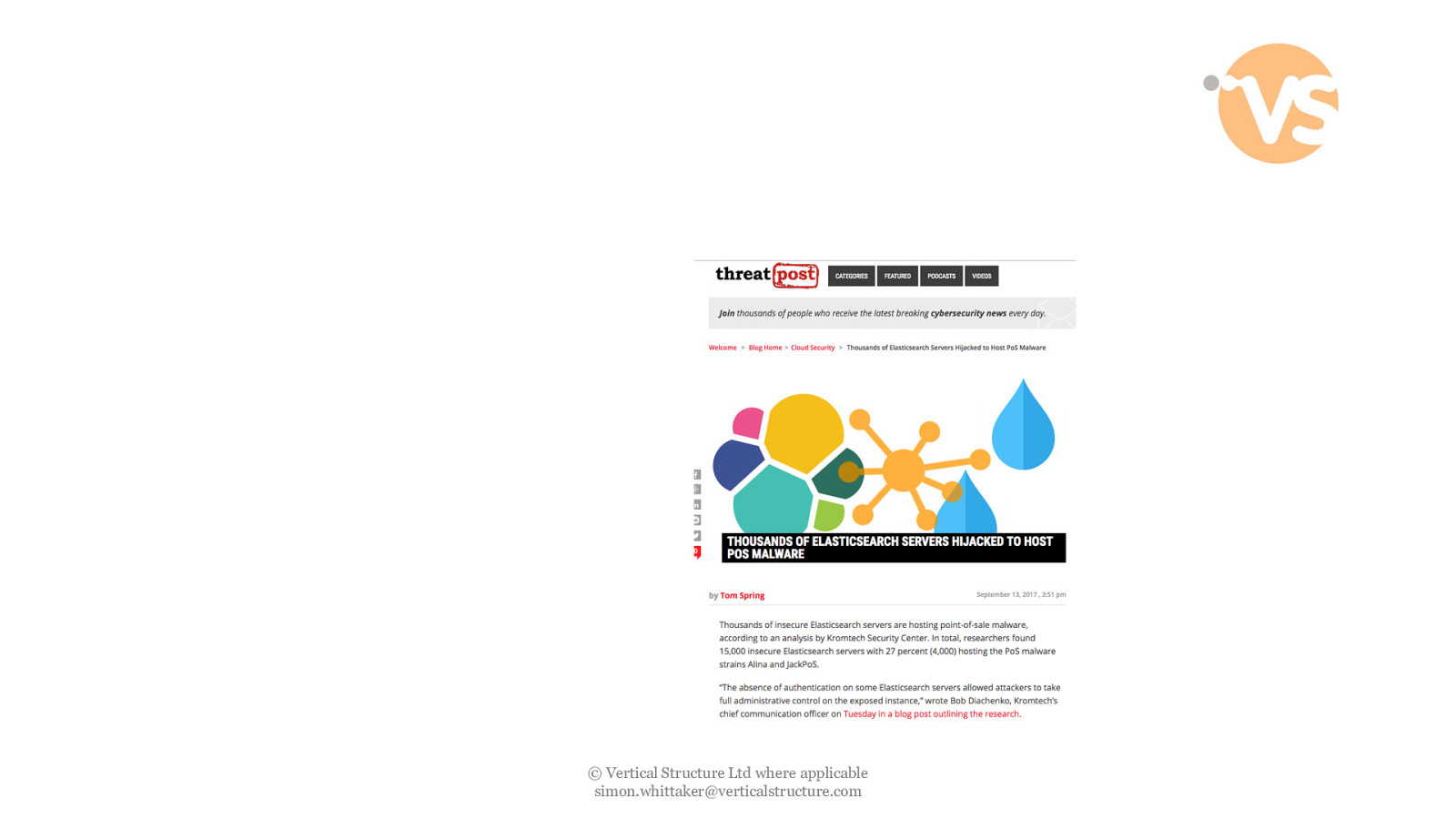
© Vertical Structure Ltd where applicable [email protected]
Slide 10

Methodology • Shodan for understanding initial numbers • Basic interrogation of top 1000 instances in export to understand: • • • • • • Cluster Name Health Number of documents Size of data Index Names Key names within index • Regex to understand key name and rate “interesting-ness” © Vertical Structure Ltd where applicable [email protected]
Slide 11
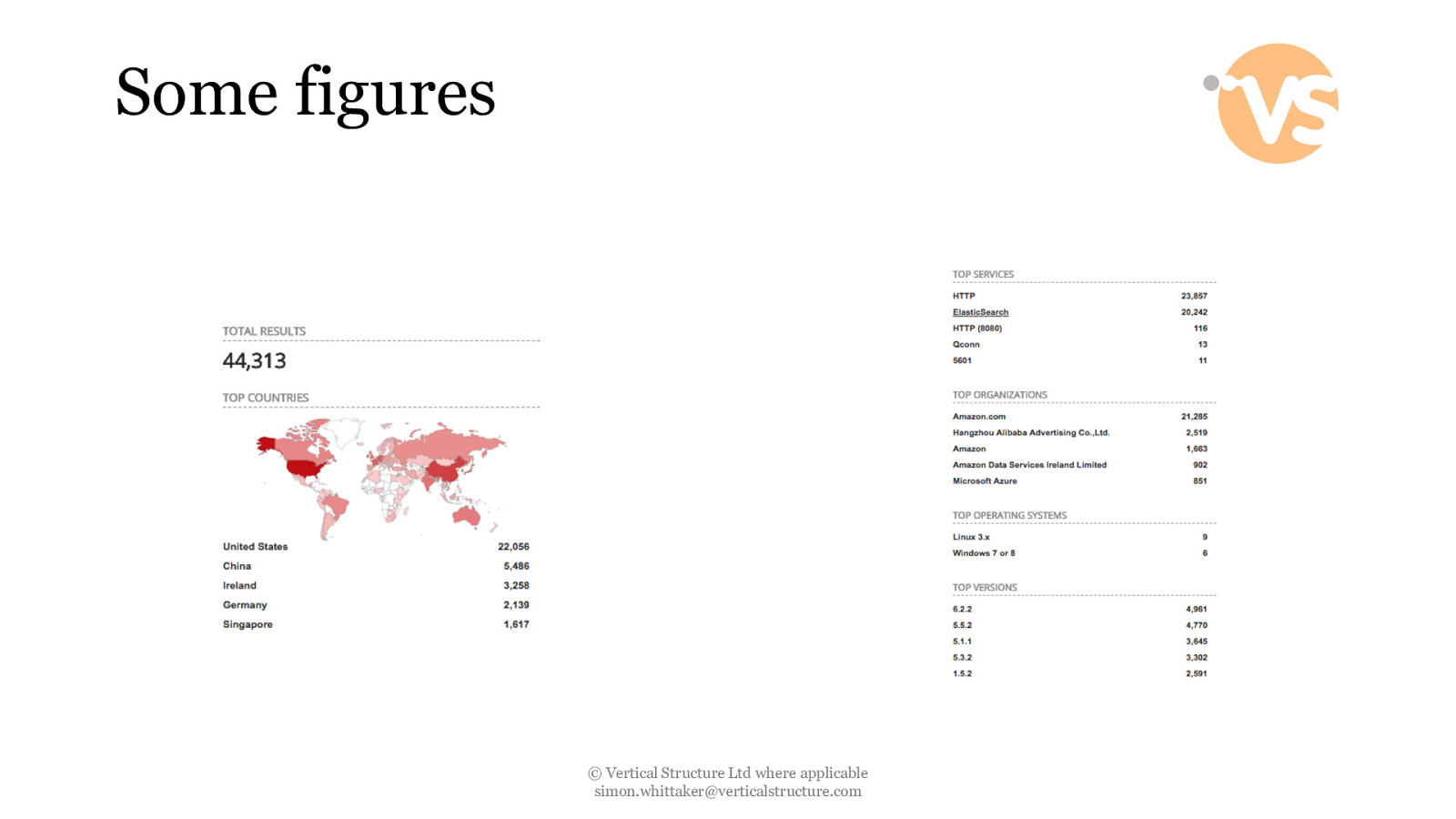
Some figures © Vertical Structure Ltd where applicable [email protected]
Slide 12
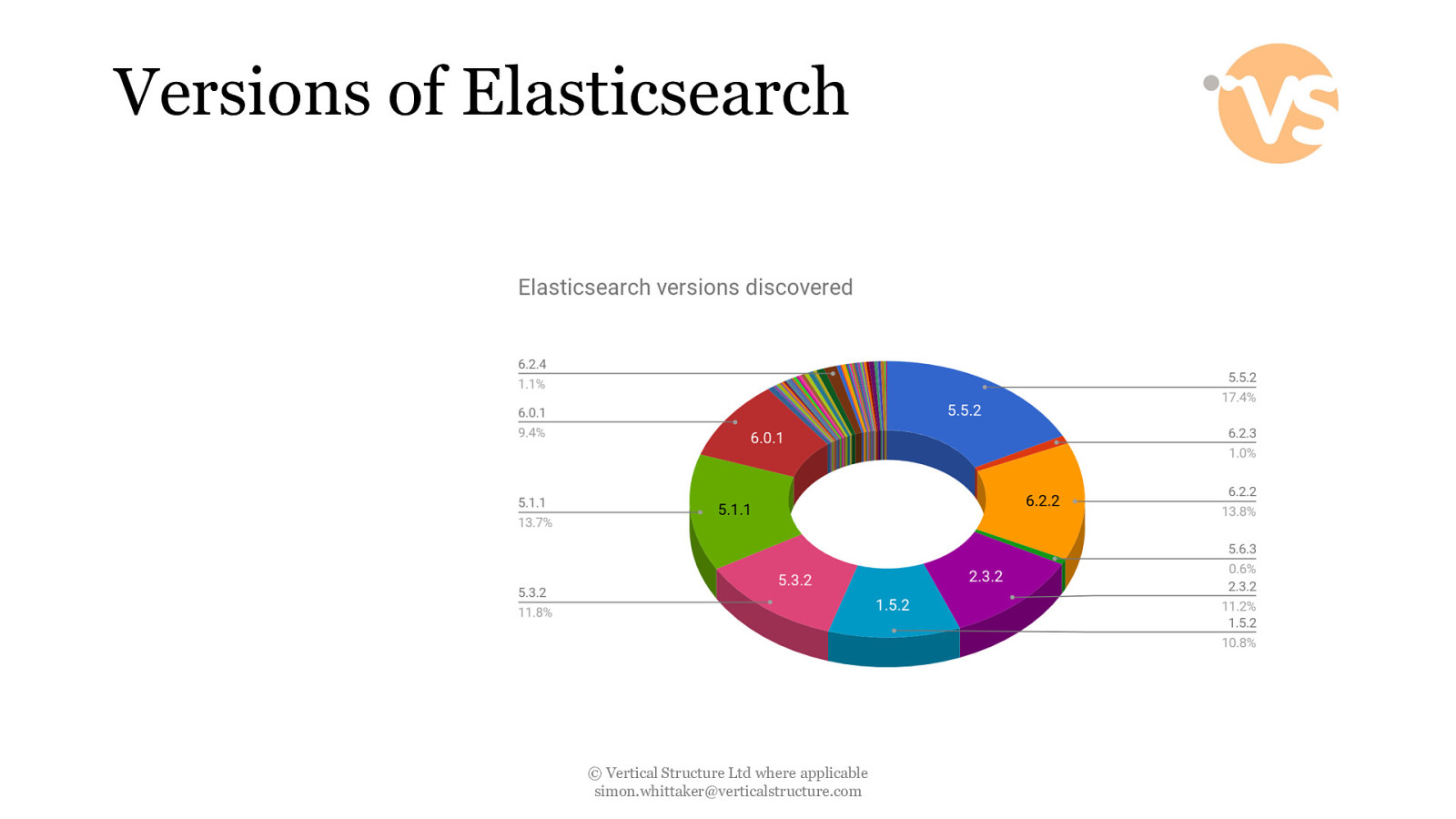
Versions of Elasticsearch © Vertical Structure Ltd where applicable [email protected]
Slide 13
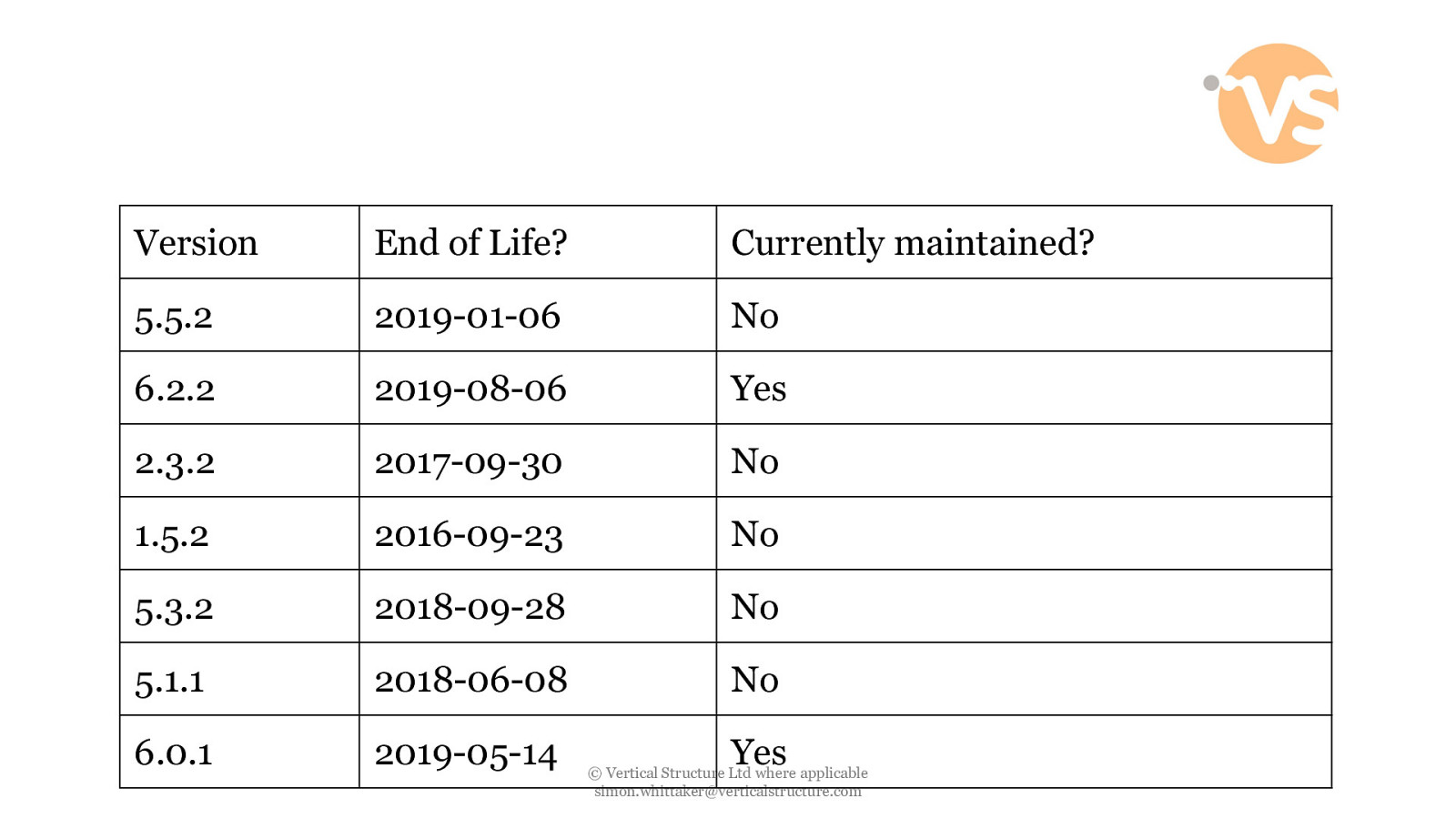
Version End of Life? Currently maintained? 5.5.2 2019-01-06 No 6.2.2 2019-08-06 Yes 2.3.2 2017-09-30 No 1.5.2 2016-09-23 No 5.3.2 2018-09-28 No 5.1.1 2018-06-08 No 6.0.1 2019-05-14 Yes © Vertical Structure Ltd where applicable [email protected]
Slide 14
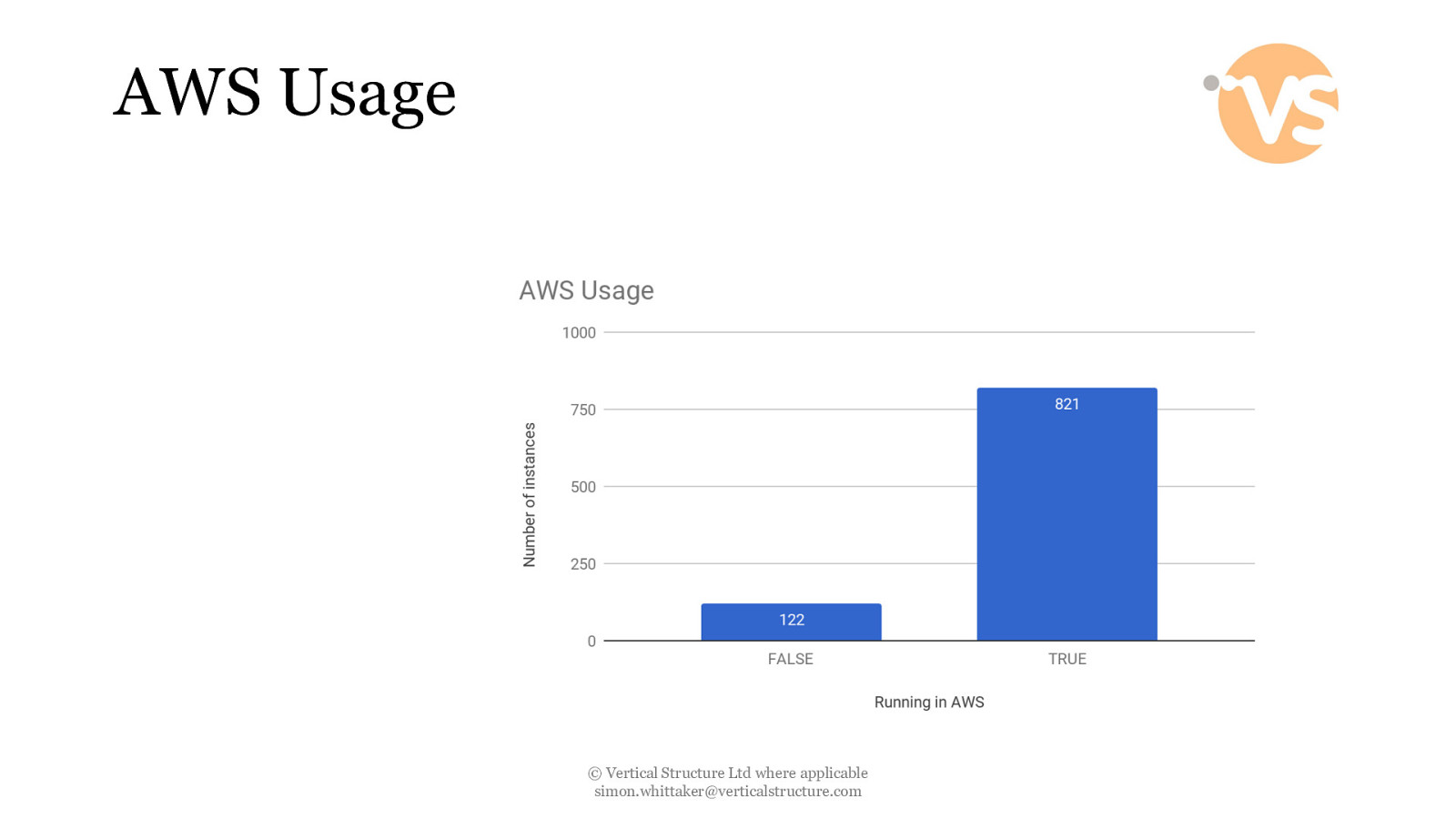
AWS Usage © Vertical Structure Ltd where applicable [email protected]
Slide 15
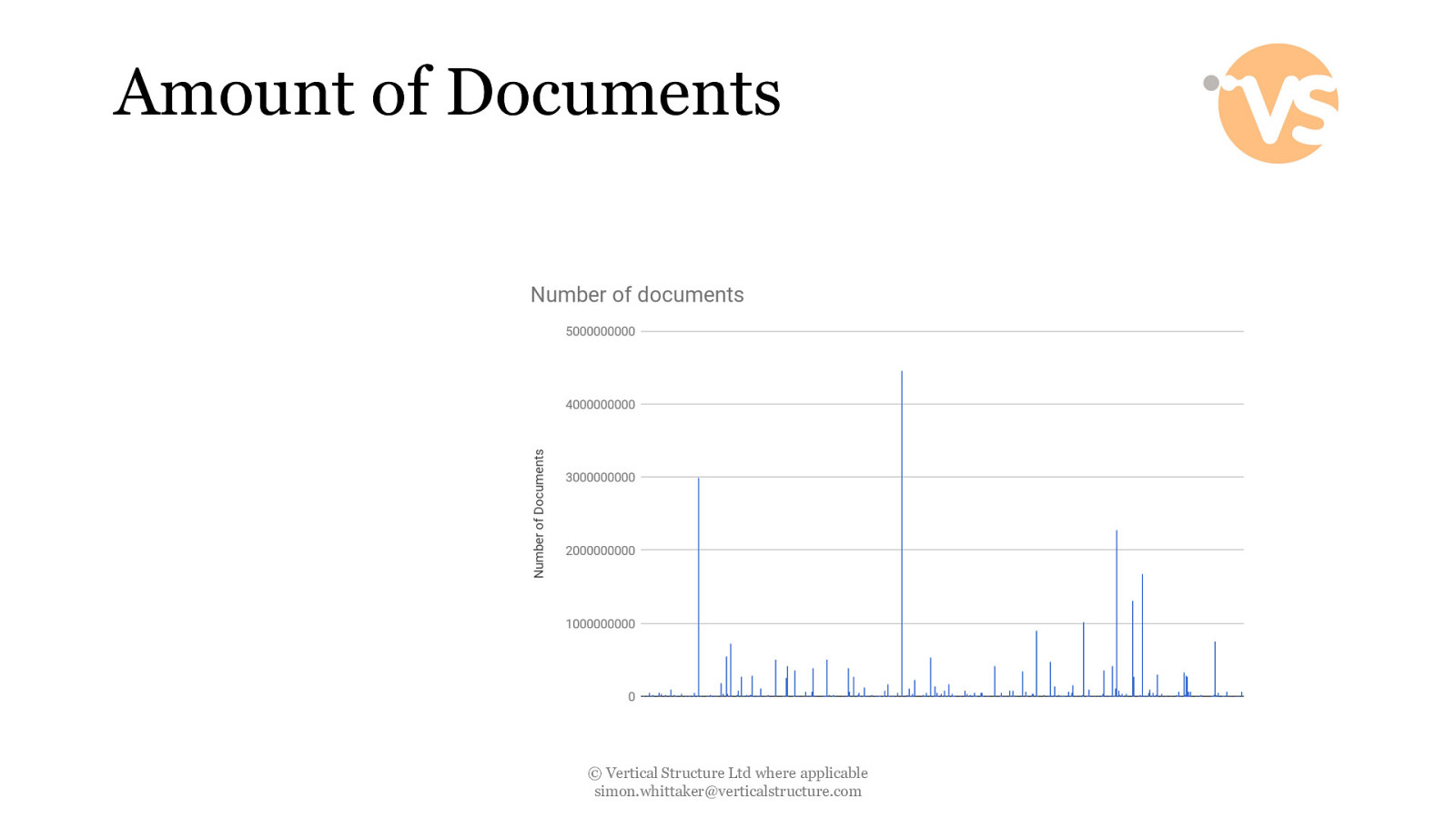
Amount of Documents © Vertical Structure Ltd where applicable [email protected]
Slide 16
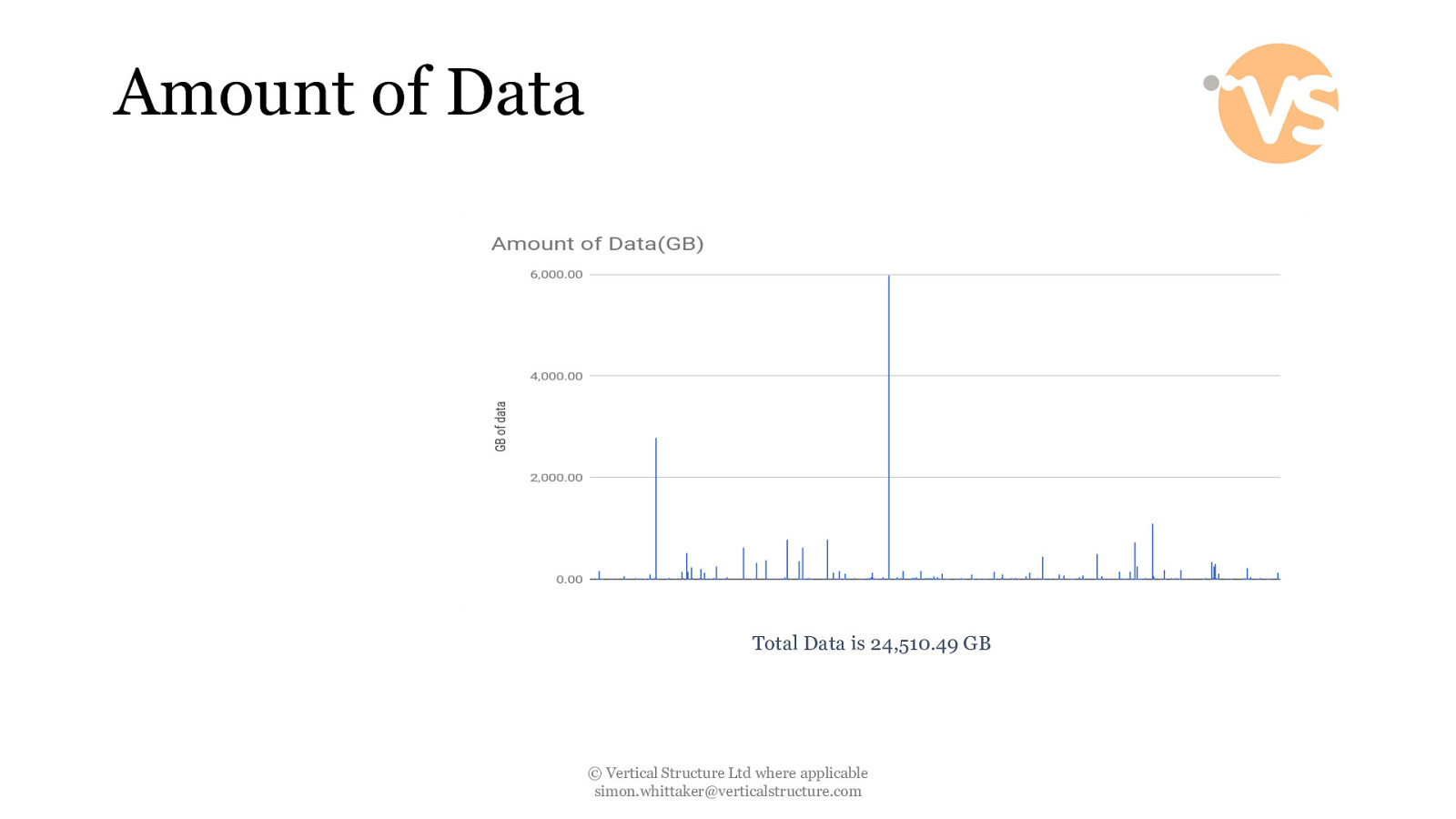
Amount of Data Total Data is 24,510.49 GB © Vertical Structure Ltd where applicable [email protected]
Slide 17
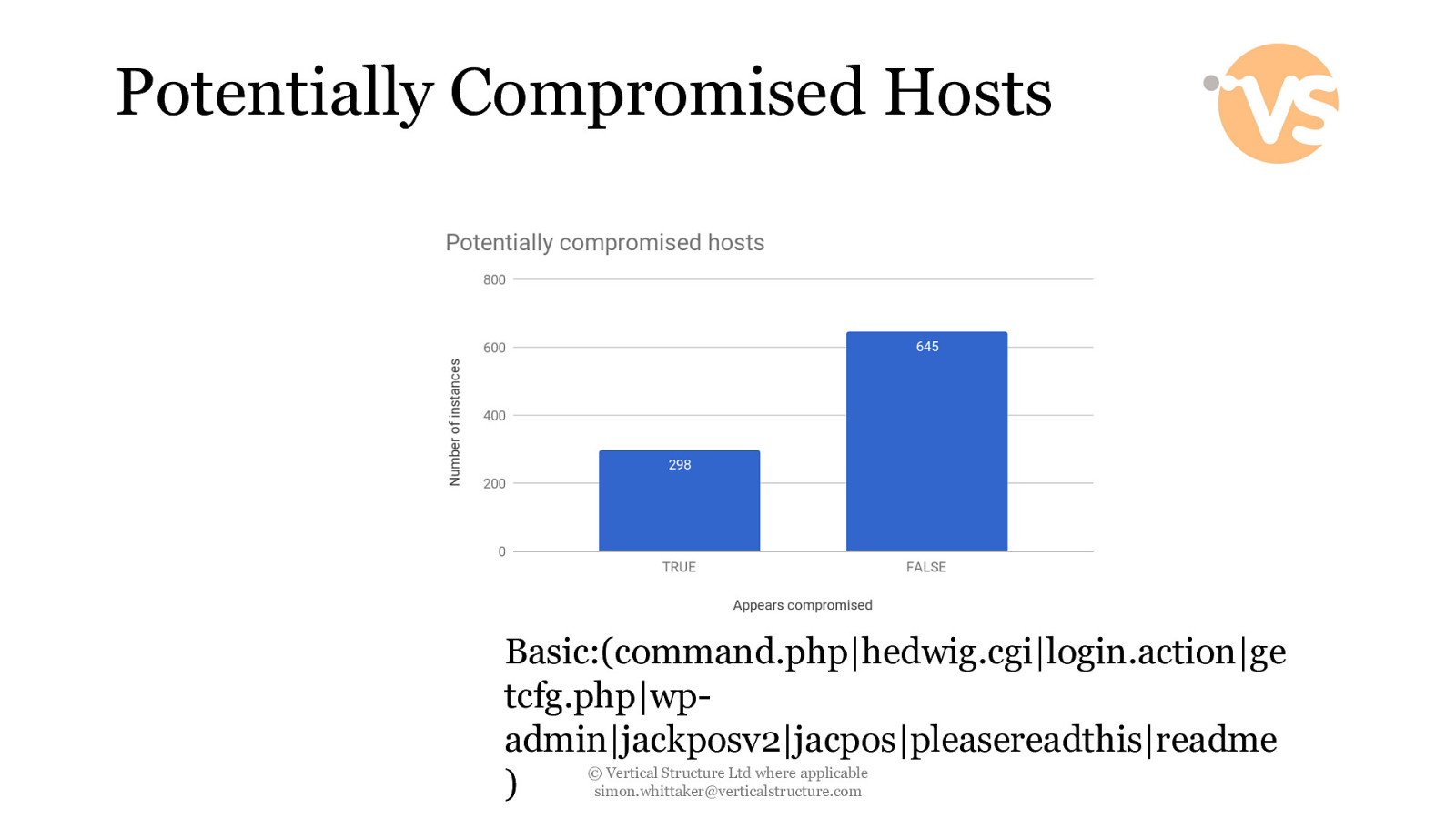
Potentially Compromised Hosts Basic:(command.php|hedwig.cgi|login.action|ge tcfg.php|wpadmin|jackposv2|jacpos|pleasereadthis|readme © Vertical Structure Ltd where applicable ) [email protected]
Slide 18

Who doesn’t love a wordcloud? © Vertical Structure Ltd where applicable [email protected]
Slide 19
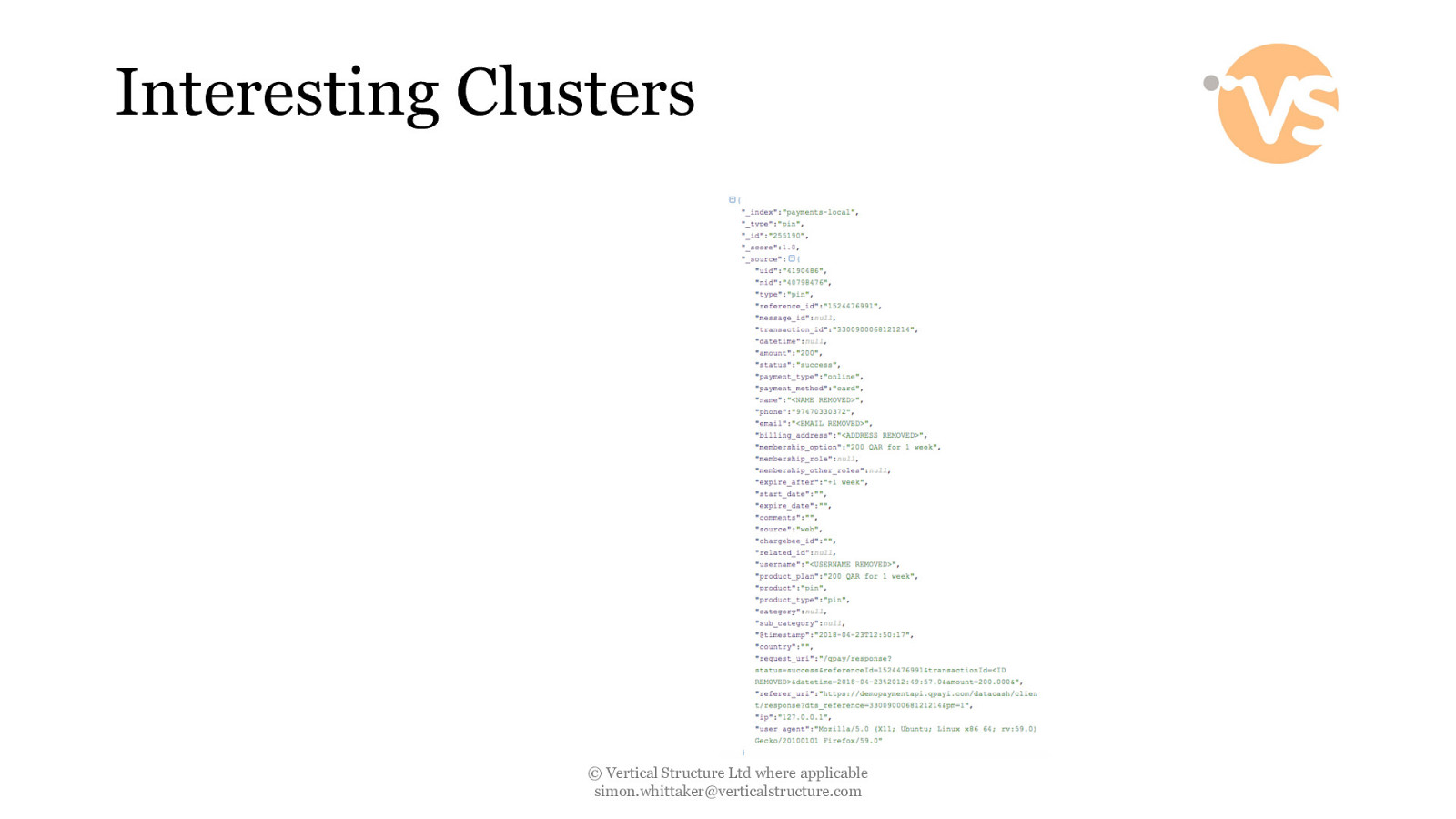
Interesting Clusters © Vertical Structure Ltd where applicable [email protected]
Slide 20
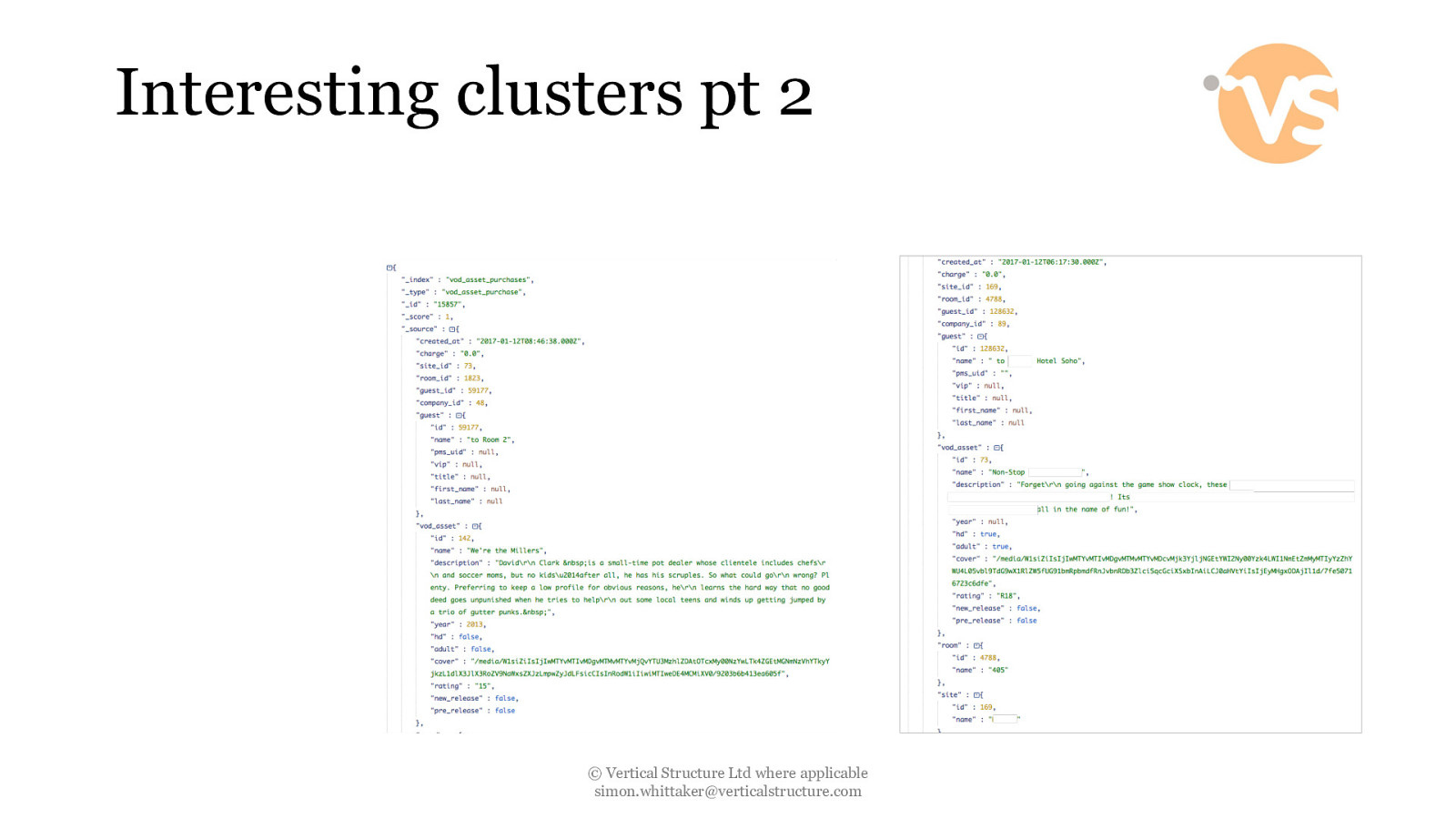
Interesting clusters pt 2 © Vertical Structure Ltd where applicable [email protected]
Slide 21
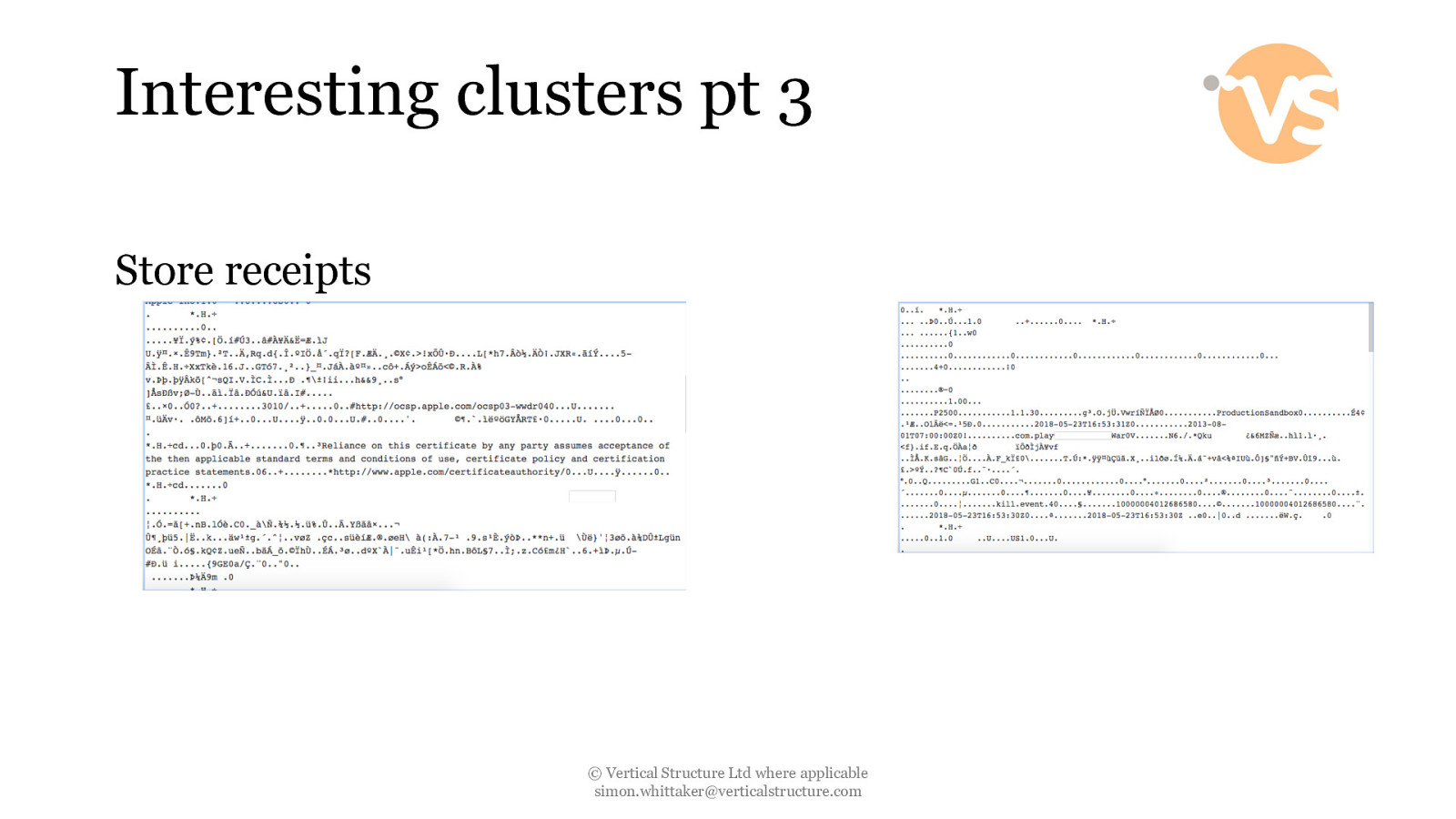
Interesting clusters pt 3 Store receipts © Vertical Structure Ltd where applicable [email protected]
Slide 22
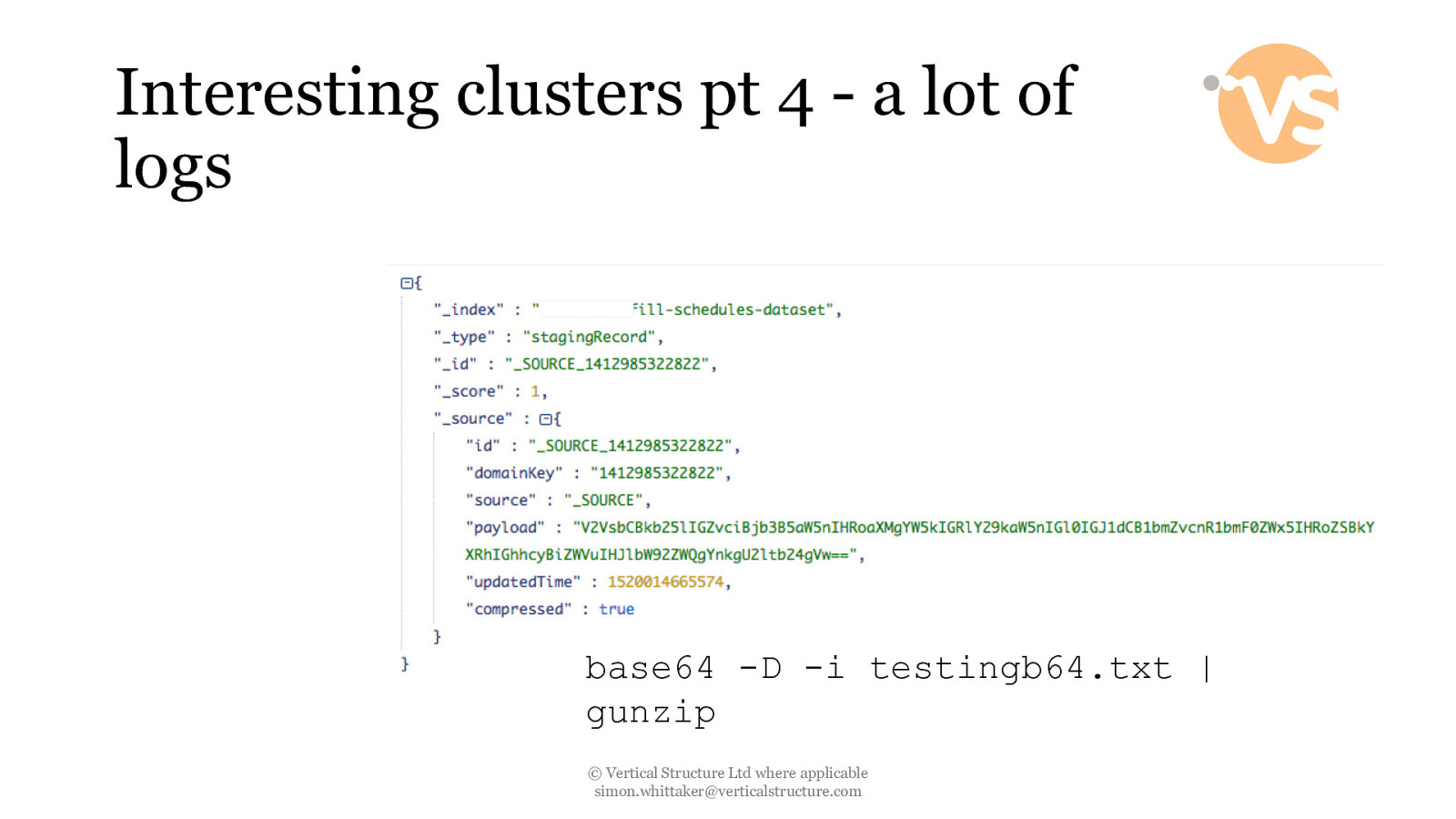
Interesting clusters pt 4 - a lot of logs base64 -D -i testingb64.txt | gunzip © Vertical Structure Ltd where applicable [email protected]
Slide 23
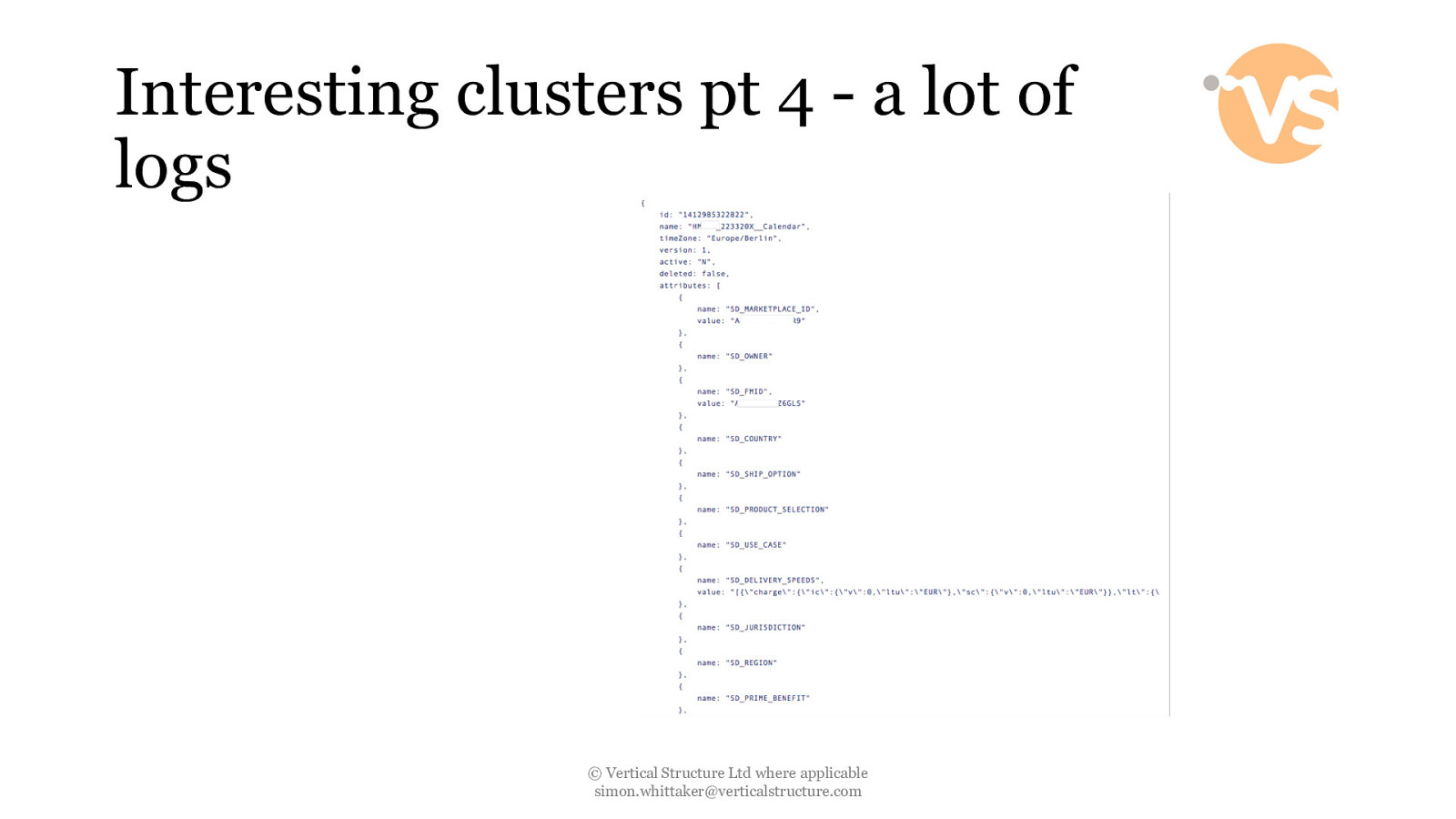
Interesting clusters pt 4 - a lot of logs © Vertical Structure Ltd where applicable [email protected]
Slide 24

Interesting clusters pt 4 - a lot of logs © Vertical Structure Ltd where applicable [email protected]
Slide 25

Interesting clusters pt 5 • Major brand names • Broadcaster • Online services • Games providers • Interesting index names • • • • Inventory-gdpr-dev kicsps-staging Storeapp-prod-logs Gisapi-prod © Vertical Structure Ltd where applicable [email protected]
Slide 26

We’re doing it wrong © Vertical Structure Ltd where applicable [email protected]
Slide 27
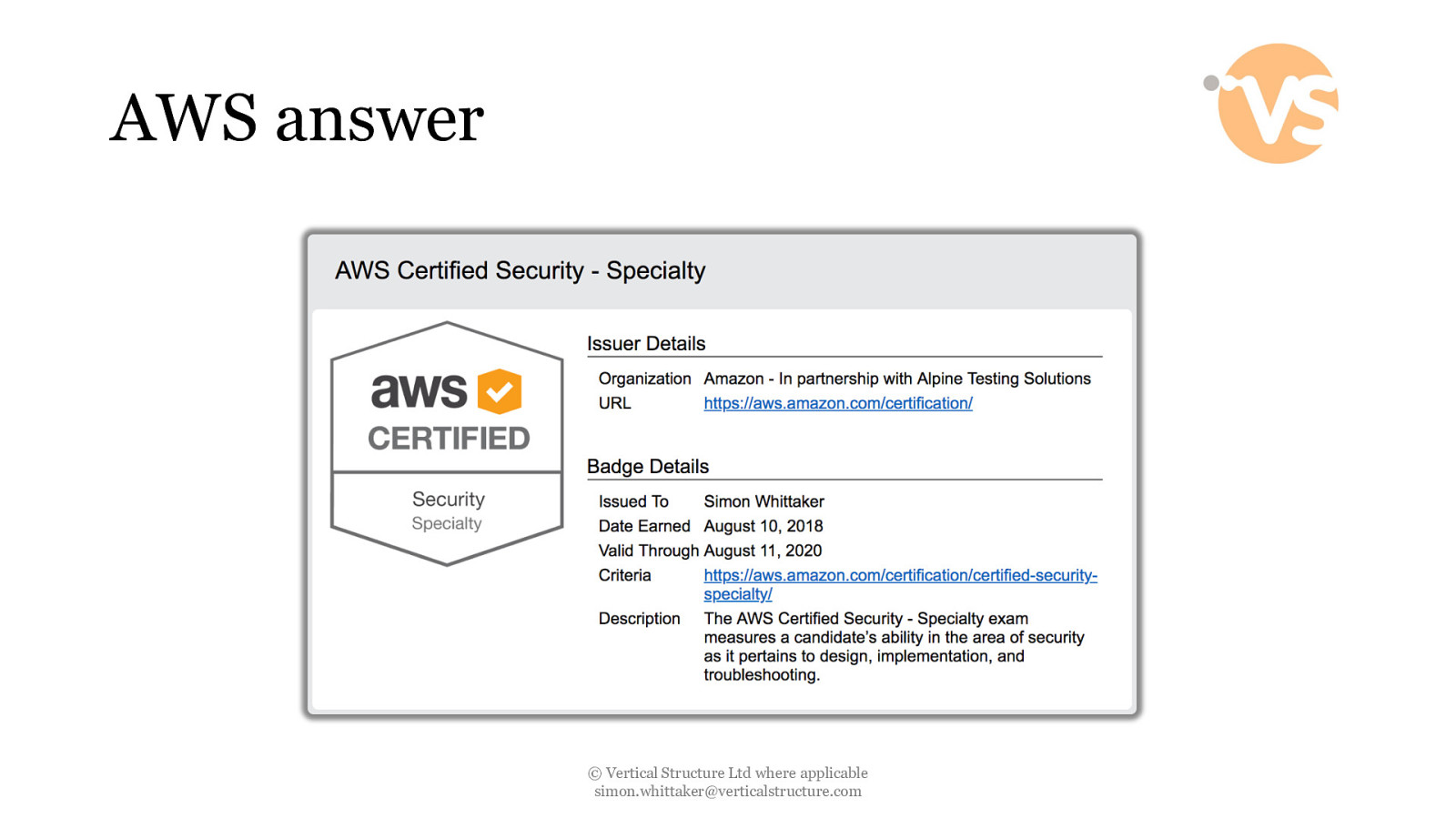
AWS answer © Vertical Structure Ltd where applicable [email protected]
Slide 28

What do you have to demonstrate? • An understanding of specialized data classifications and AWS data protection mechanisms. • An understanding of data encryption methods and AWS mechanisms to implement them. • An understanding of secure Internet protocols and AWS mechanisms to implement them. • A working knowledge of AWS security services and features of services to provide a secure production environment. • Competency gained from two or more years of production deployment experience using AWS security services and features. • Ability to make tradeoff decisions with regard to cost, security, and deployment complexity given a set of application requirements. • An understanding of security operations and risk. © Vertical Structure Ltd where applicable [email protected]
Slide 29

Recommended knowledge • A minimum of five years of IT security experience designing and implementing security solutions. • At least two years of hands-on experience securing AWS workloads. • Security controls for workloads on AWS. © Vertical Structure Ltd where applicable [email protected]
Slide 30
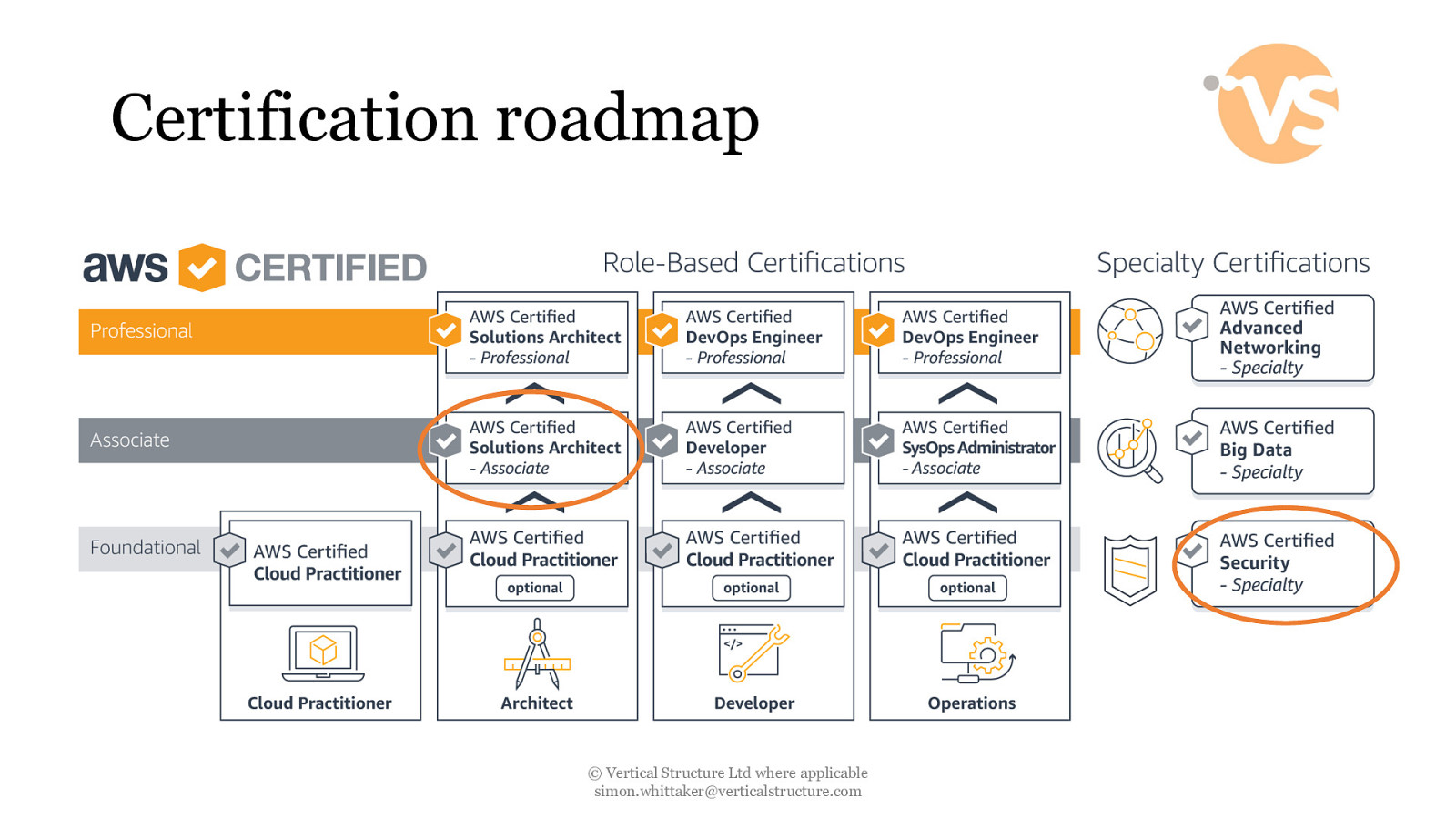
Certification roadmap © Vertical Structure Ltd where applicable [email protected]
Slide 31

Exam format • Format: Multiple choice, multiple answer • Length: 170 minutes, 65 questions • Registration Fee: 300 USD © Vertical Structure Ltd where applicable [email protected]
Slide 32
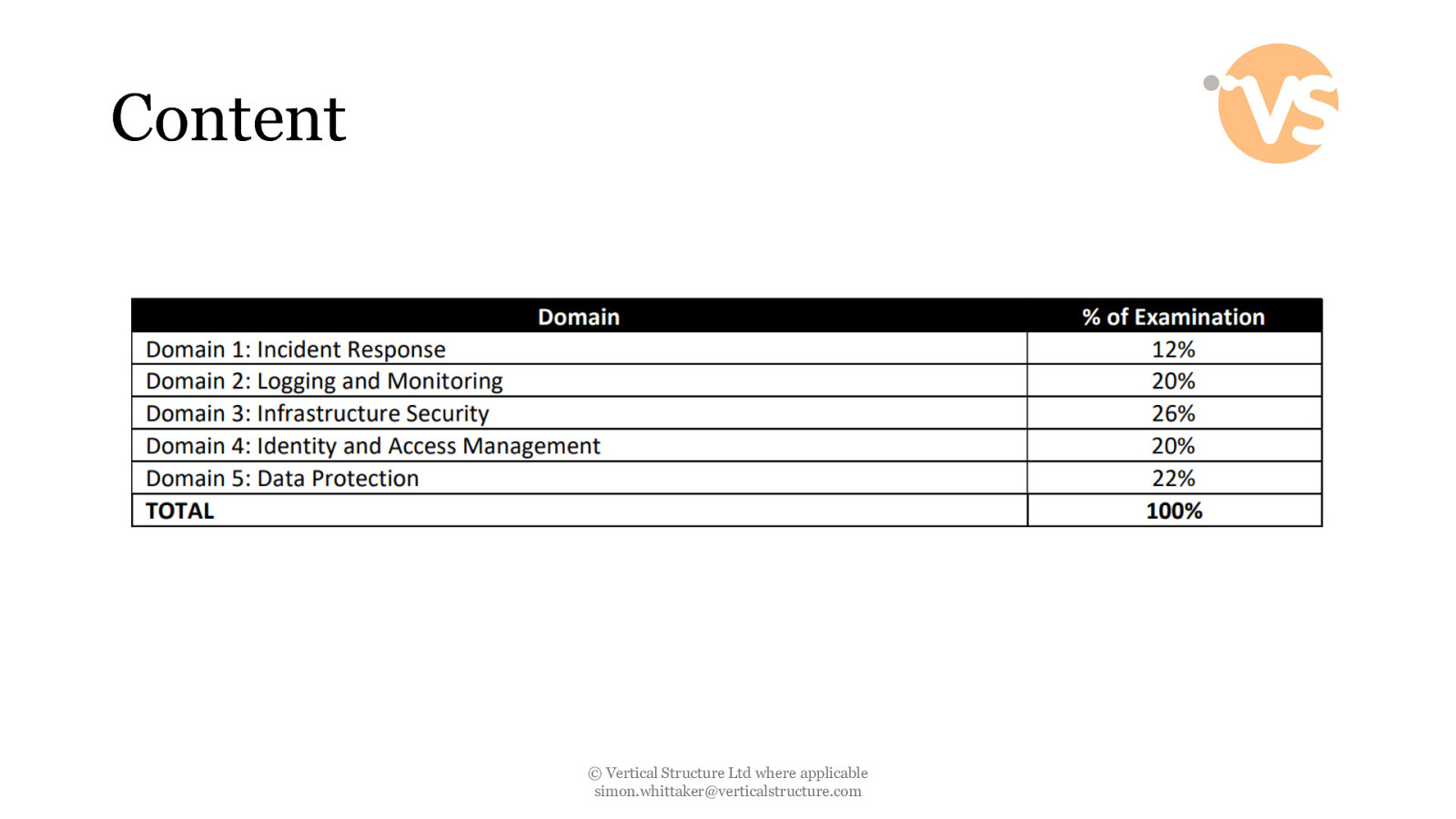
Content © Vertical Structure Ltd where applicable [email protected]
Slide 33

Domain 1 - Incident Response • 1.1 Given an AWS abuse notice, evaluate the suspected compromised instance or exposed access keys. • 1.2 Verify that the Incident Response plan includes relevant AWS services. • 1.3 Evaluate the configuration of automated alerting, and execute possible remediation of security-related incidents and emerging issues. © Vertical Structure Ltd where applicable [email protected]
Slide 34

Domain 2 – Logging and Monitoring • 2.1 Design and implement security monitoring and alerting. • 2.2 Troubleshoot security monitoring and alerting. • 2.3 Design and implement a logging solution. • 2.4 Troubleshoot logging solutions. © Vertical Structure Ltd where applicable [email protected]
Slide 35
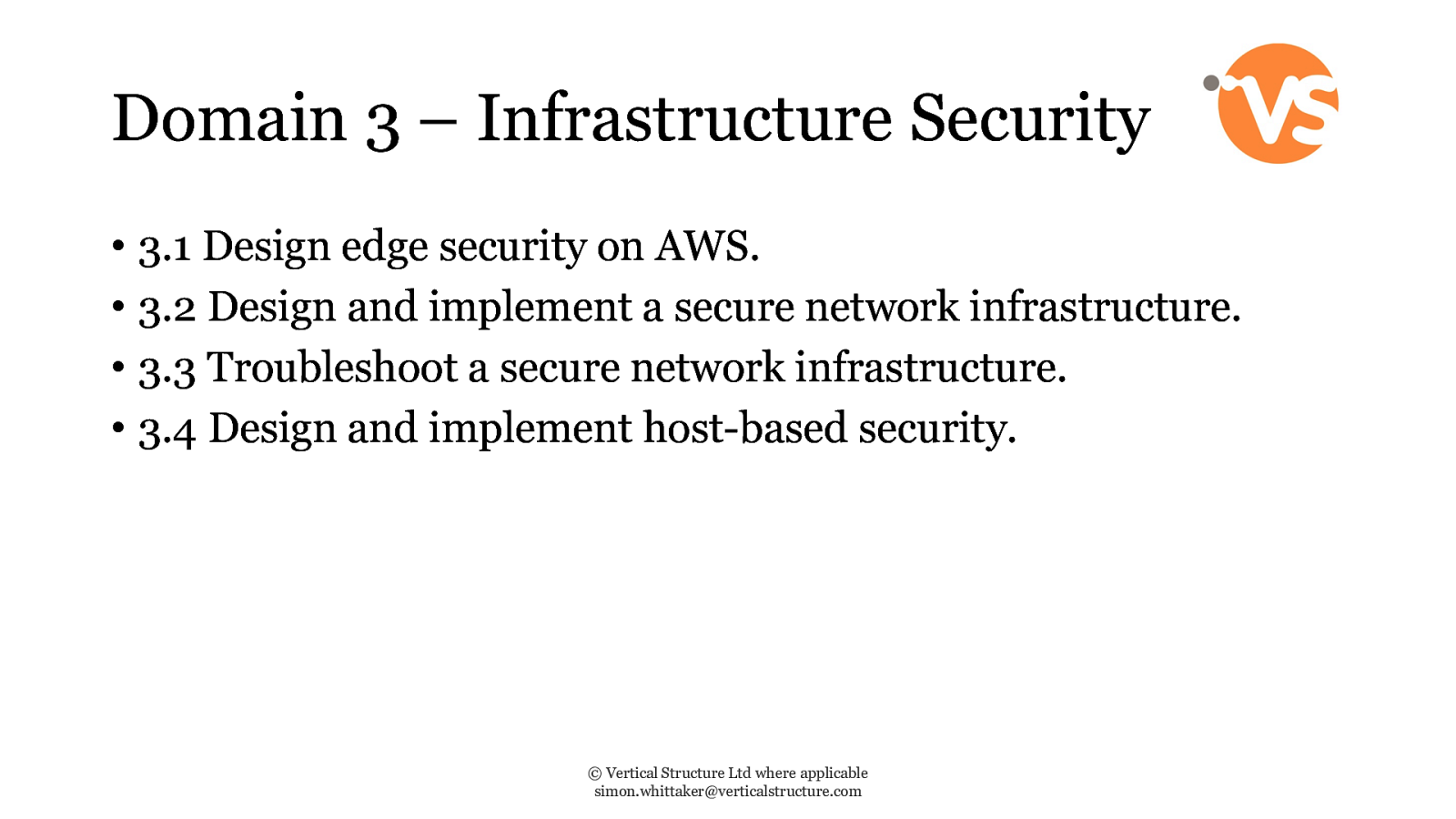
Domain 3 – Infrastructure Security • 3.1 Design edge security on AWS. • 3.2 Design and implement a secure network infrastructure. • 3.3 Troubleshoot a secure network infrastructure. • 3.4 Design and implement host-based security. © Vertical Structure Ltd where applicable [email protected]
Slide 36

Domain 4 – Identity and Access Management • 4.1 Design and implement a scalable authorization and authentication system to access AWS resources. • 4.2 Troubleshoot an authorization and authentication system to access AWS resources. © Vertical Structure Ltd where applicable [email protected]
Slide 37

Domain 5 – Data Protection • 5.1 Design and implement key management and use. • 5.2 Troubleshoot key management. • 5.3 Design and implement a data encryption solution for data at rest and data in transit. © Vertical Structure Ltd where applicable [email protected]
Slide 38

The big stuff – from my experience © Vertical Structure Ltd where applicable [email protected]
Slide 39

The big stuff – from my experience © Vertical Structure Ltd where applicable [email protected]
Slide 40
The big stuff – from my experience © Vertical Structure Ltd where applicable [email protected]
Slide 41

Regulatory requirements • Really important but a bit of a snoozefest • FIPS and EAL compliance are possible with CloudHSM • Logging © Vertical Structure Ltd where applicable [email protected]
Slide 42
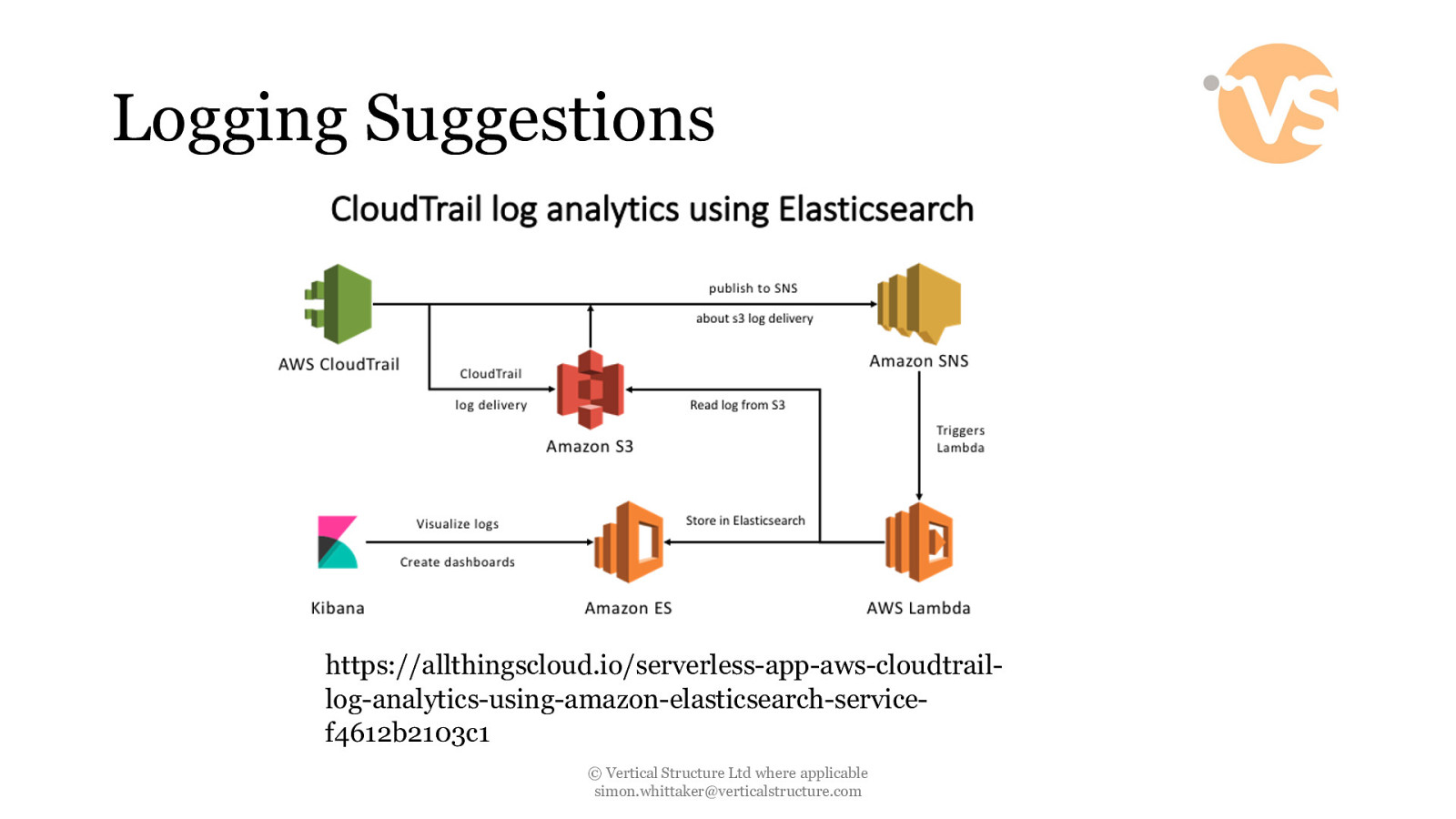
Logging Suggestions https://allthingscloud.io/serverless-app-aws-cloudtraillog-analytics-using-amazon-elasticsearch-servicef4612b2103c1 © Vertical Structure Ltd where applicable [email protected]
Slide 43

Things I wasn’t asked much about (but you may be…) • Hypervisor security • NAT instances vs gateways • VPC endpoints • API gateway © Vertical Structure Ltd where applicable [email protected]
Slide 44

API gateway © Vertical Structure Ltd where applicable [email protected]
Slide 45
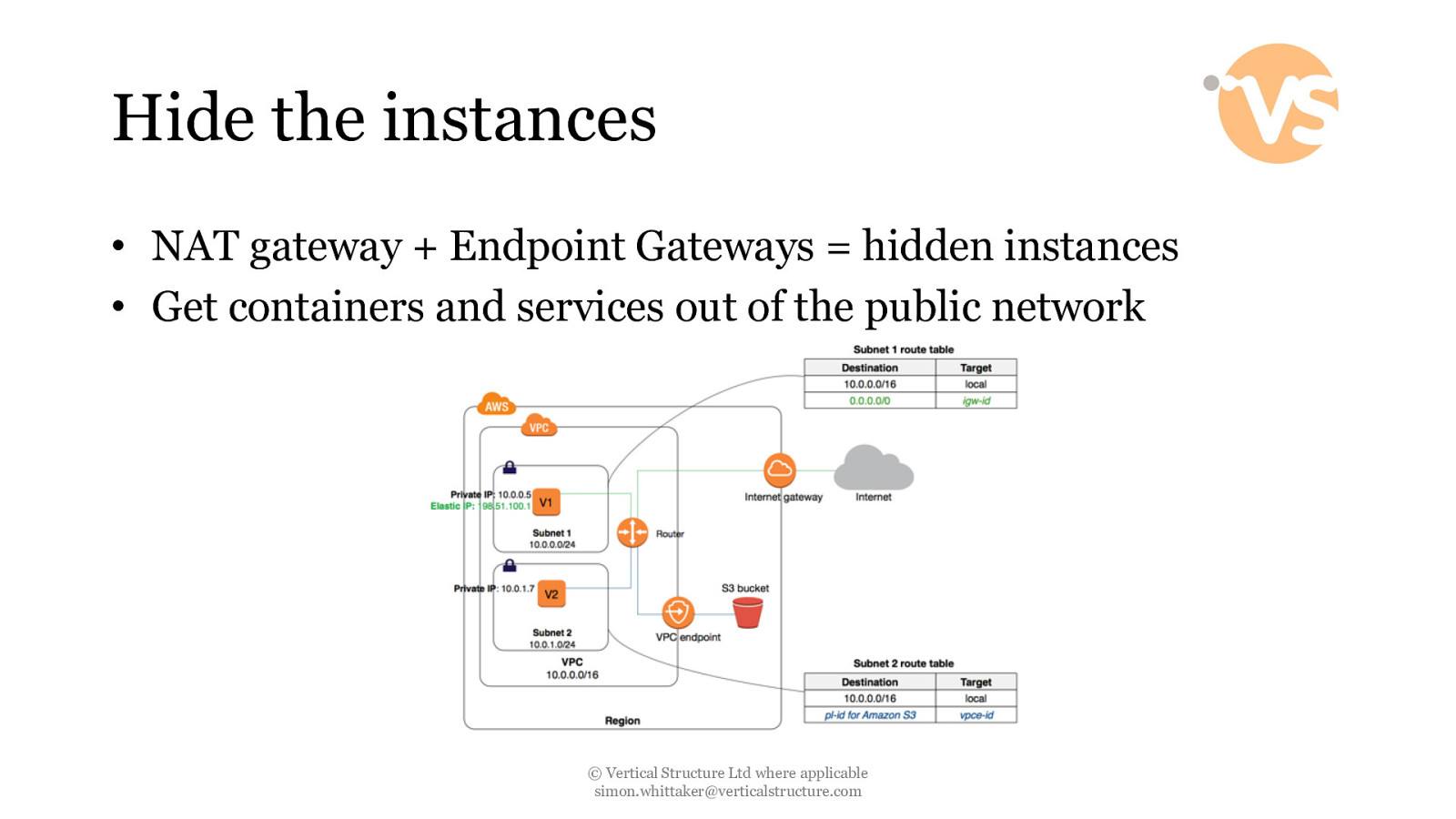
Hide the instances • NAT gateway + Endpoint Gateways = hidden instances • Get containers and services out of the public network © Vertical Structure Ltd where applicable [email protected]
Slide 46

Other useful items to help prepare • Use CIS images if you would like a level of security pre-rolled • Questions about Amazon services vs self-rolled • Encrypting root EBS volumes © Vertical Structure Ltd where applicable [email protected]
Slide 47

Tools Useful tools © Vertical Structure Ltd where applicable [email protected]
Slide 48
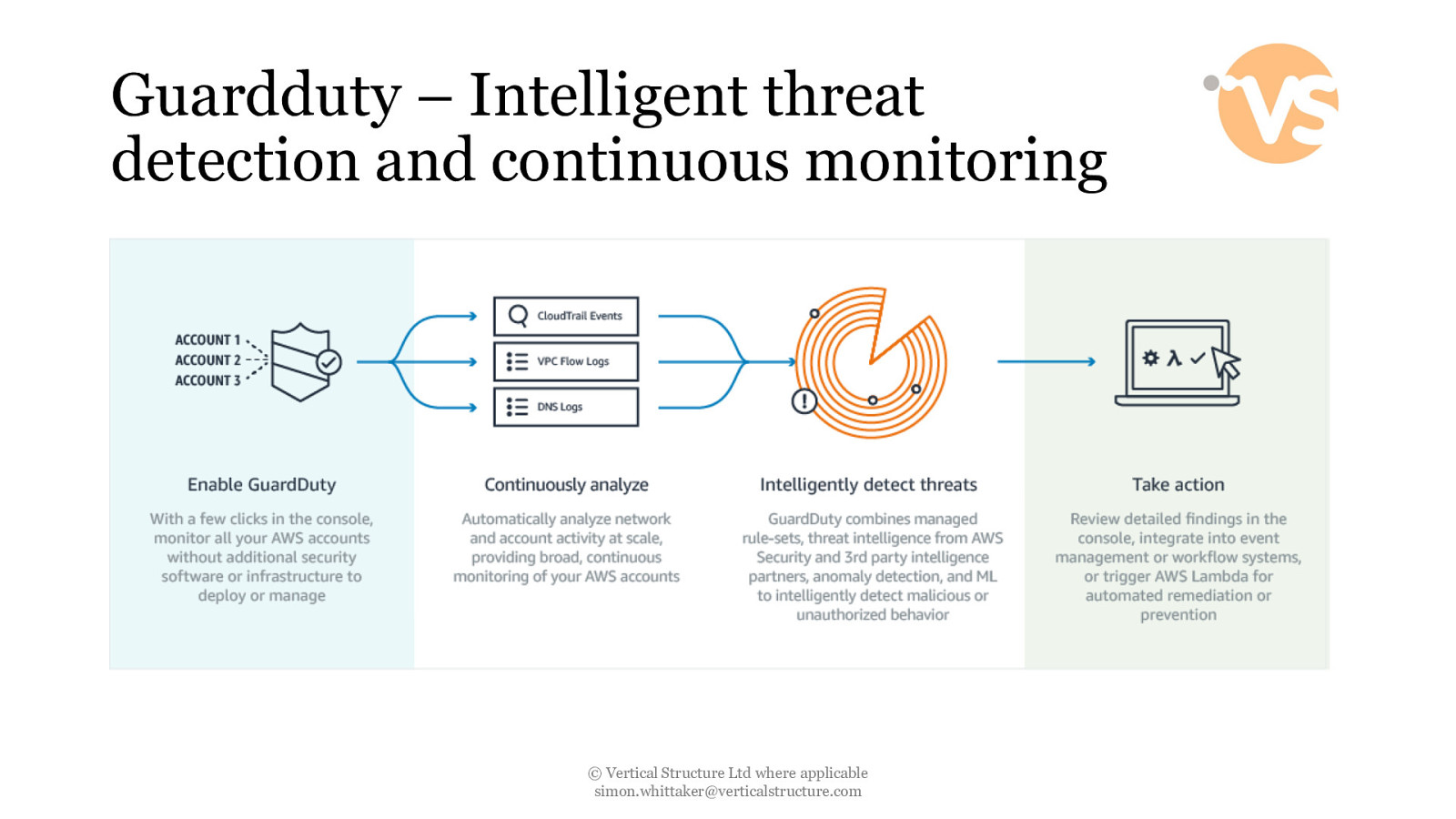
Guardduty – Intelligent threat detection and continuous monitoring © Vertical Structure Ltd where applicable [email protected]
Slide 49
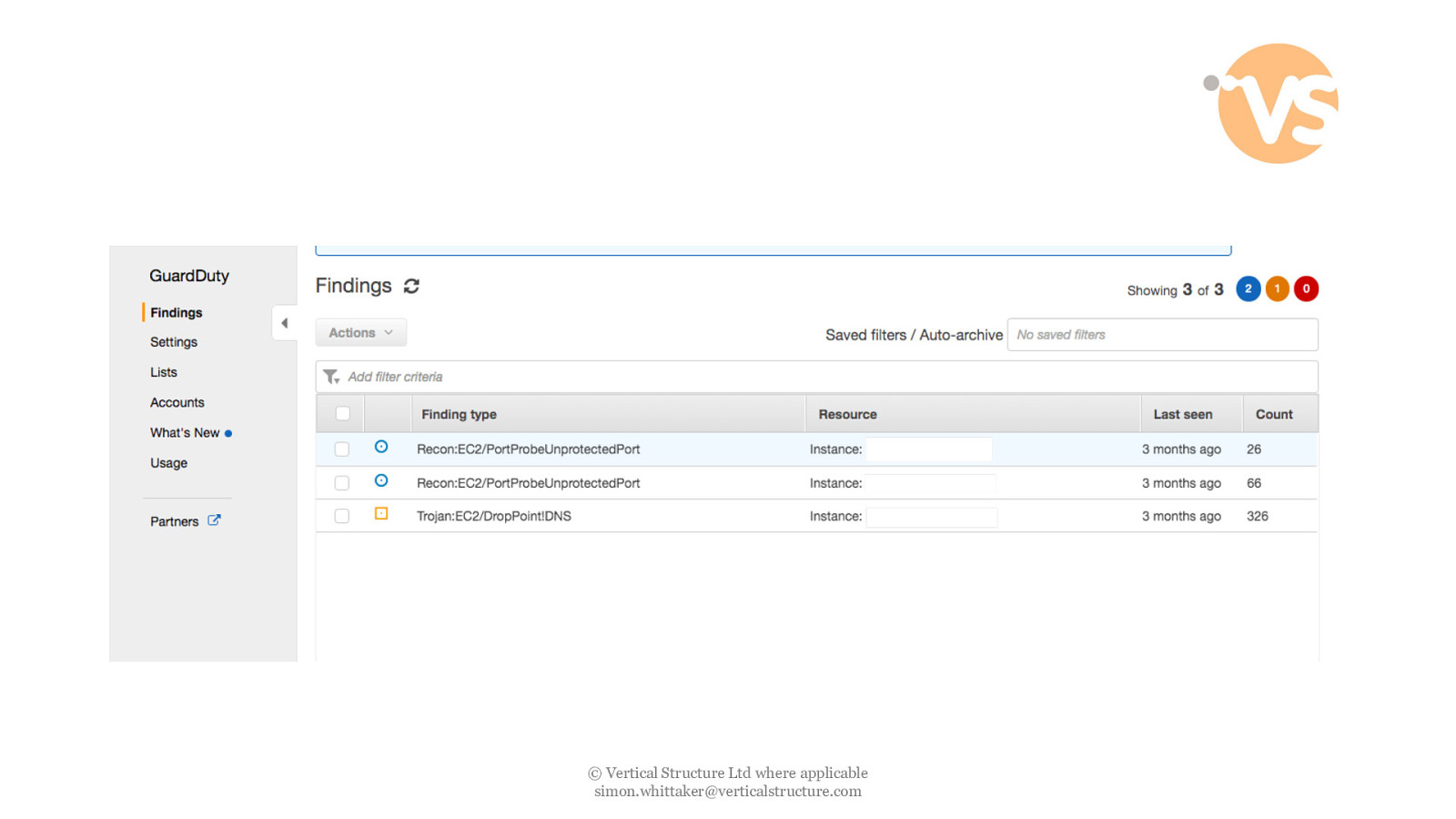
© Vertical Structure Ltd where applicable [email protected]
Slide 50
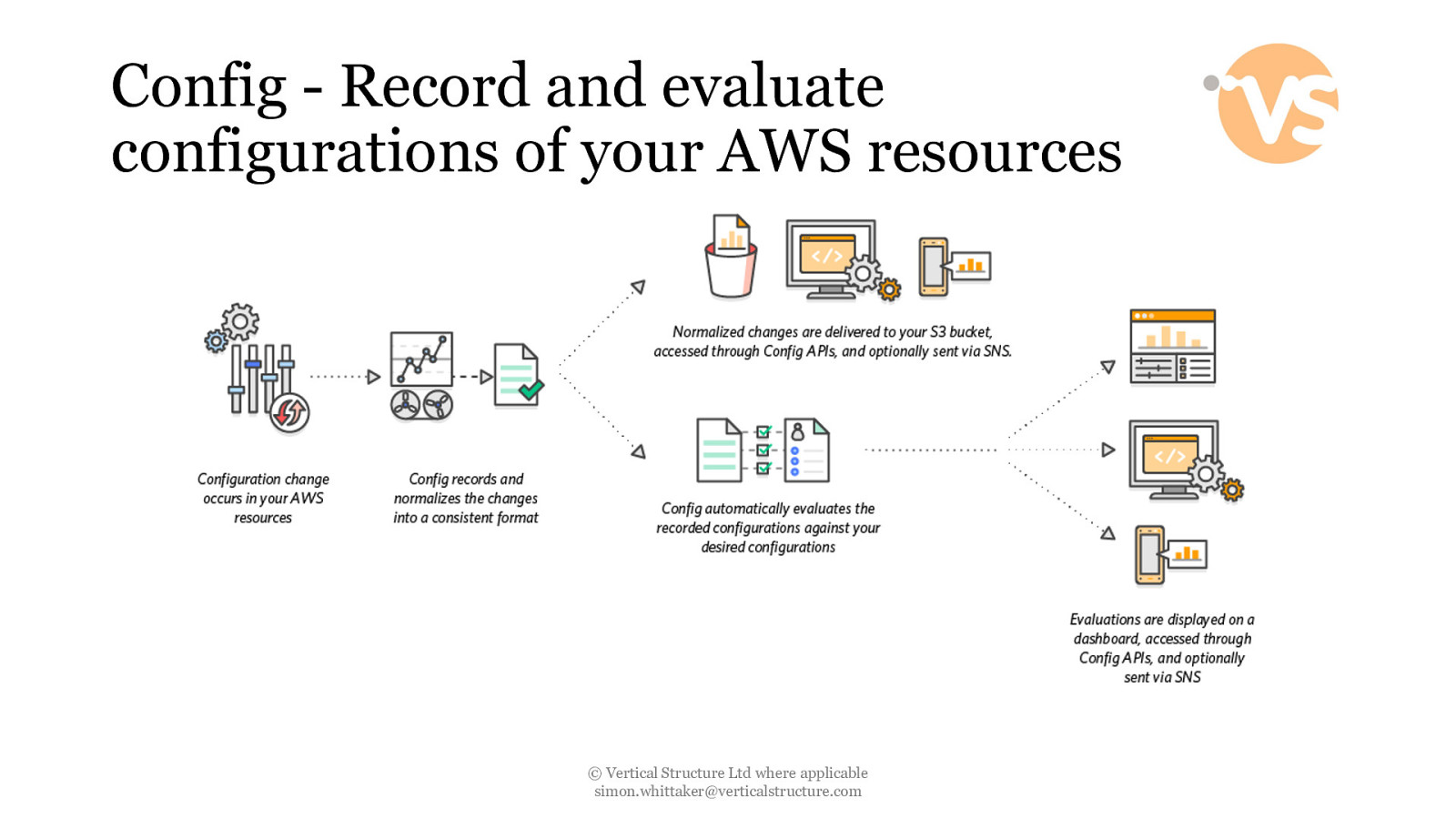
Config - Record and evaluate configurations of your AWS resources © Vertical Structure Ltd where applicable [email protected]
Slide 51
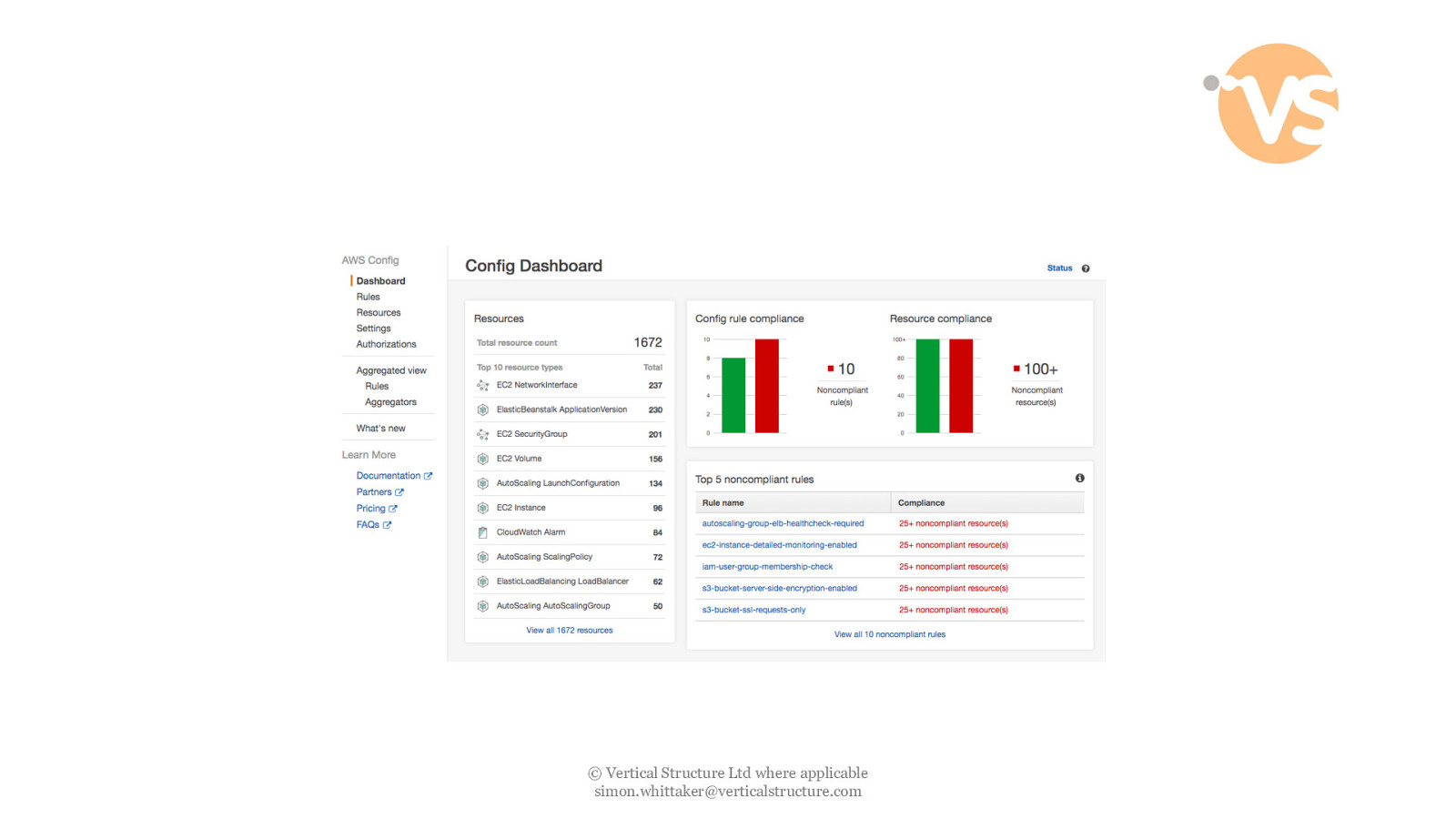
© Vertical Structure Ltd where applicable [email protected]
Slide 52
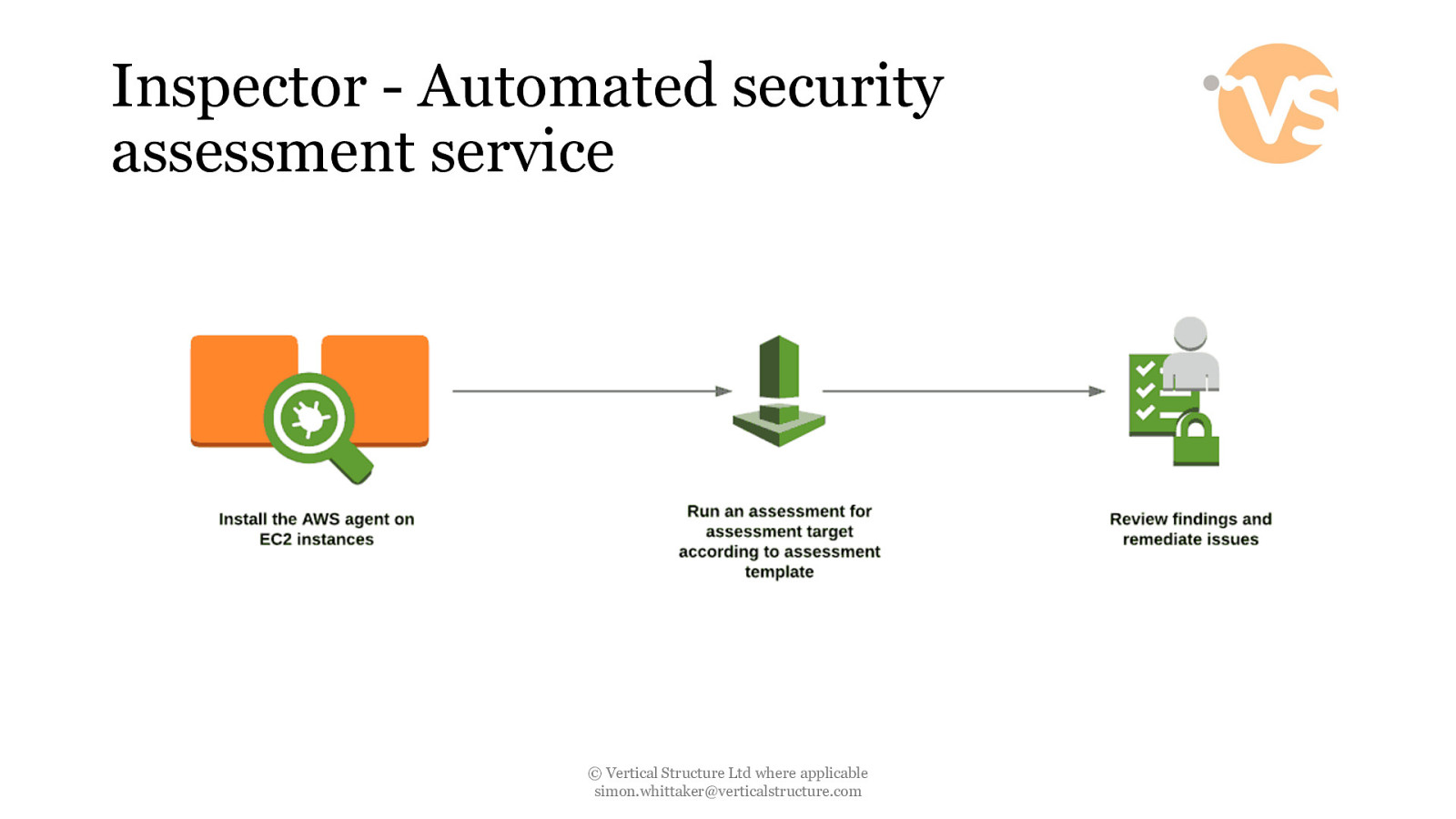
Inspector - Automated security assessment service © Vertical Structure Ltd where applicable [email protected]
Slide 53
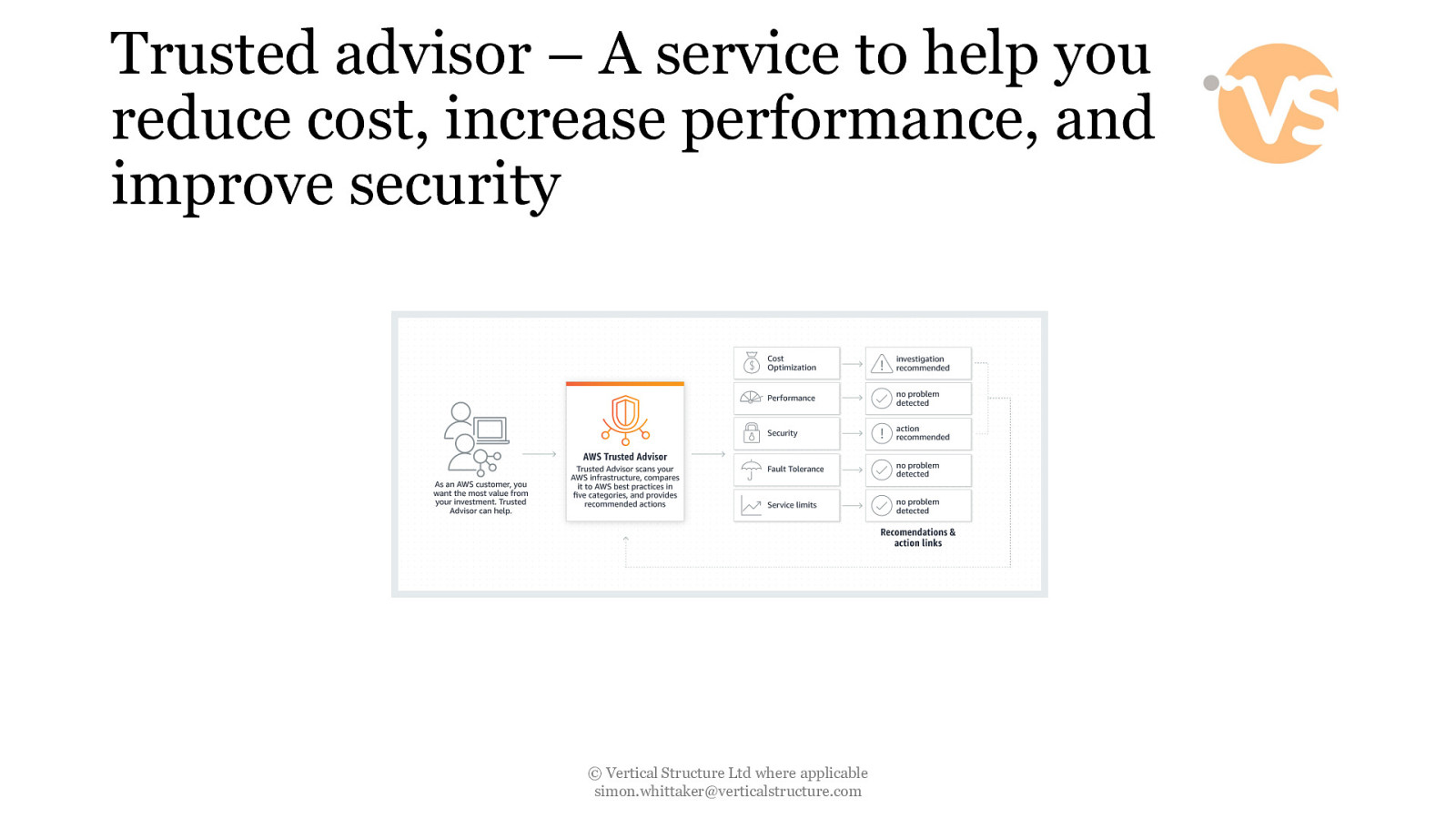
Trusted advisor – A service to help you reduce cost, increase performance, and improve security © Vertical Structure Ltd where applicable [email protected]
Slide 54
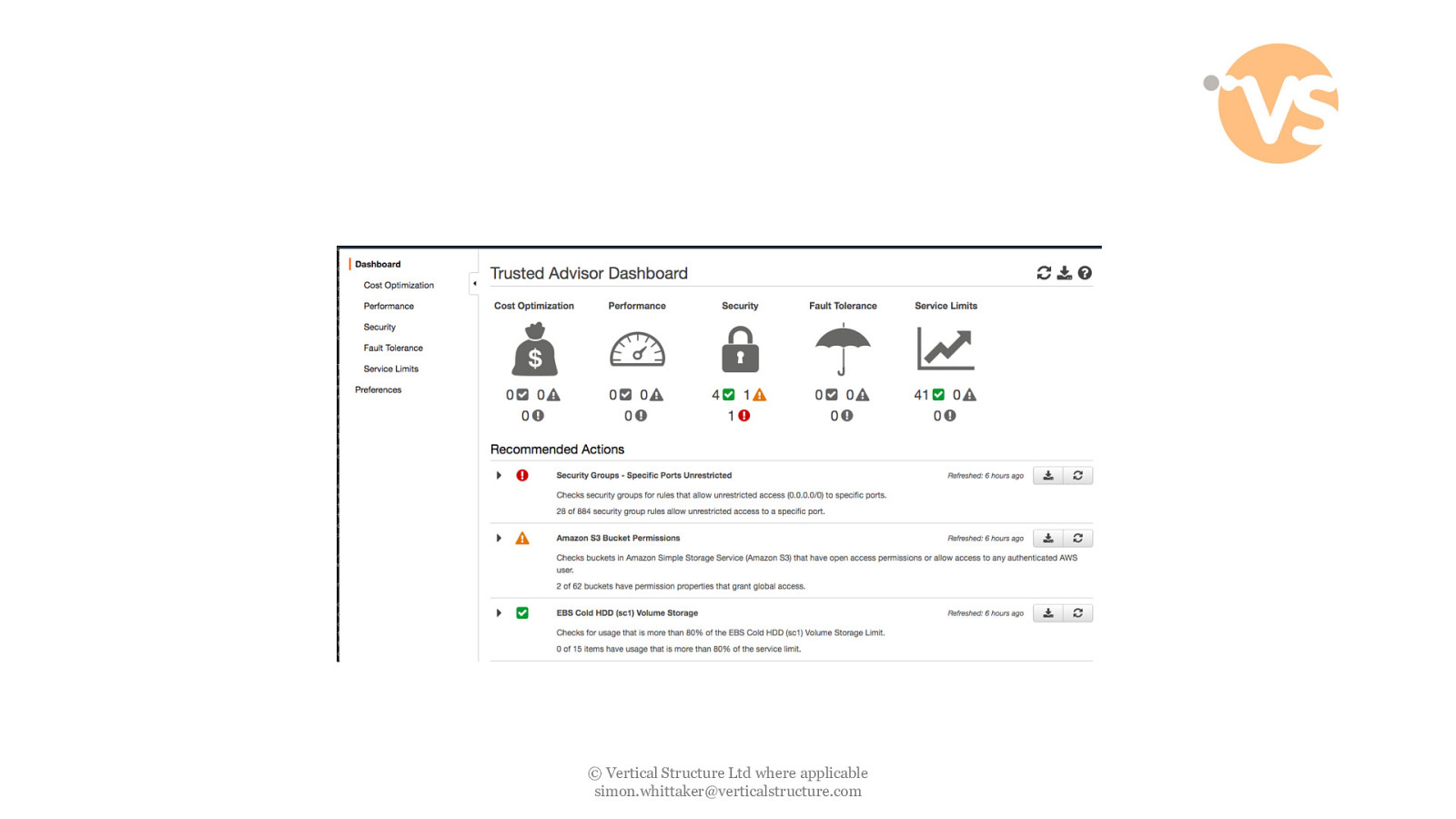
© Vertical Structure Ltd where applicable [email protected]
Slide 55
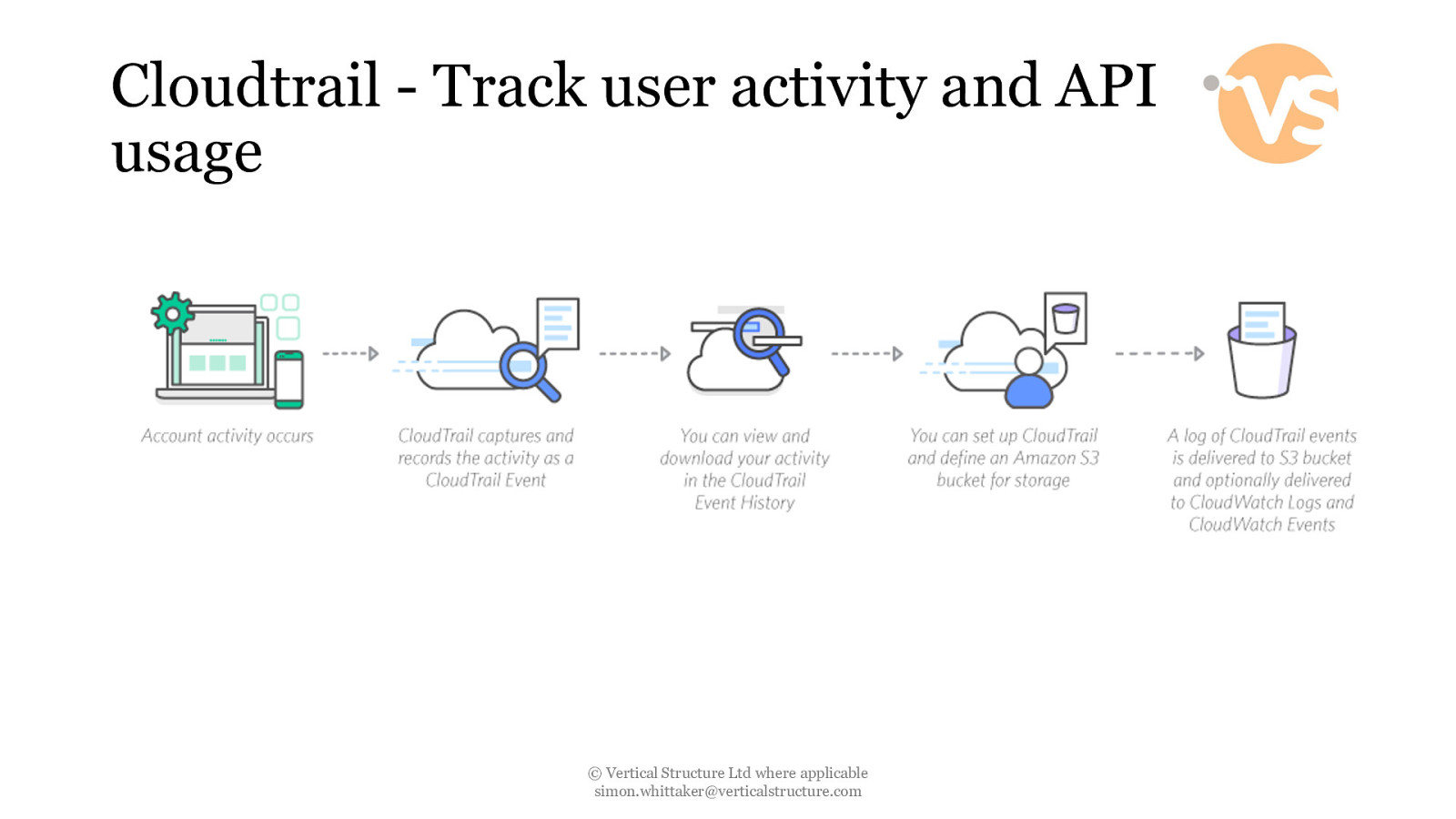
Cloudtrail - Track user activity and API usage © Vertical Structure Ltd where applicable [email protected]
Slide 56
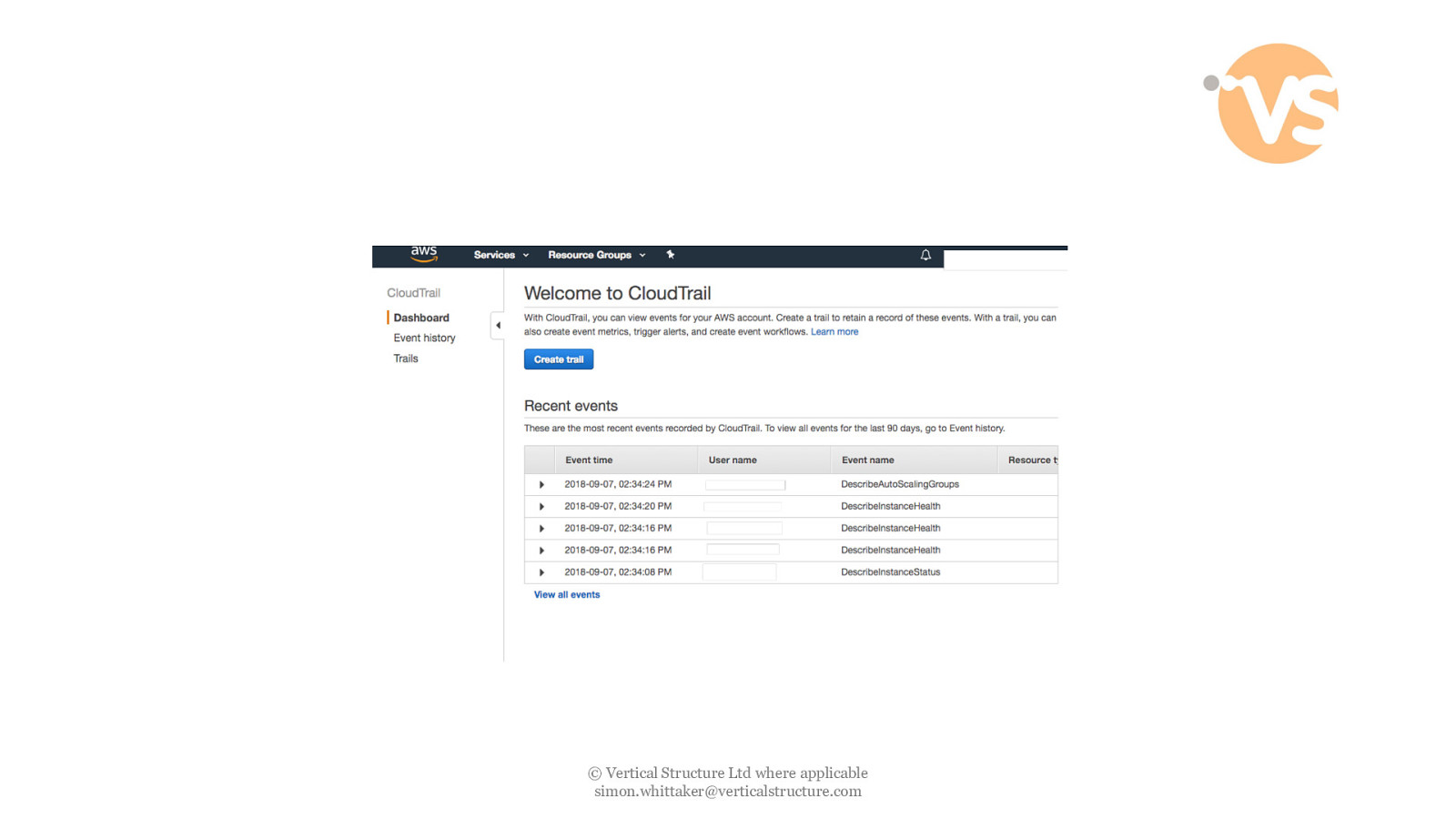
© Vertical Structure Ltd where applicable [email protected]
Slide 57
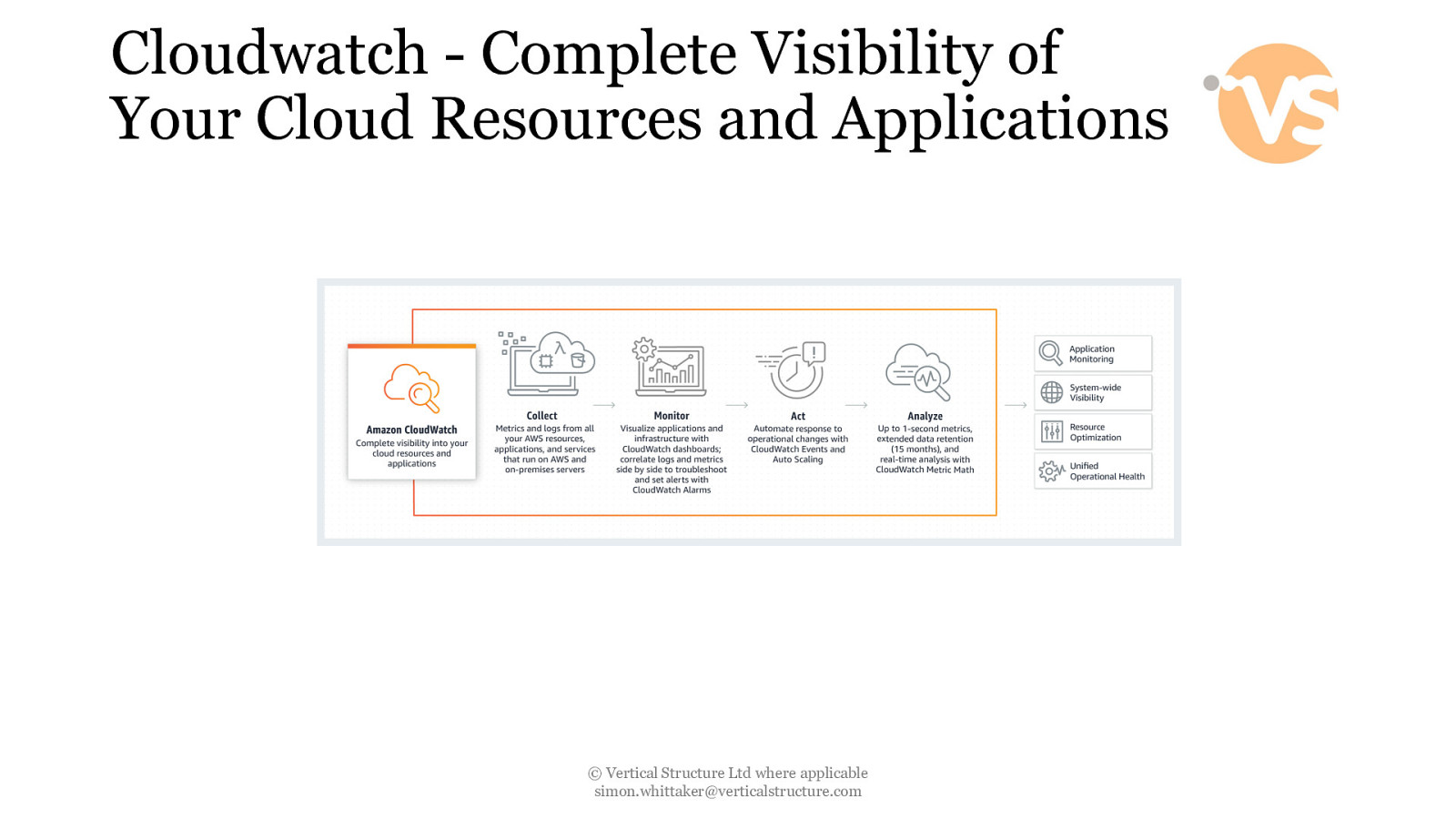
Cloudwatch - Complete Visibility of Your Cloud Resources and Applications © Vertical Structure Ltd where applicable [email protected]
Slide 58
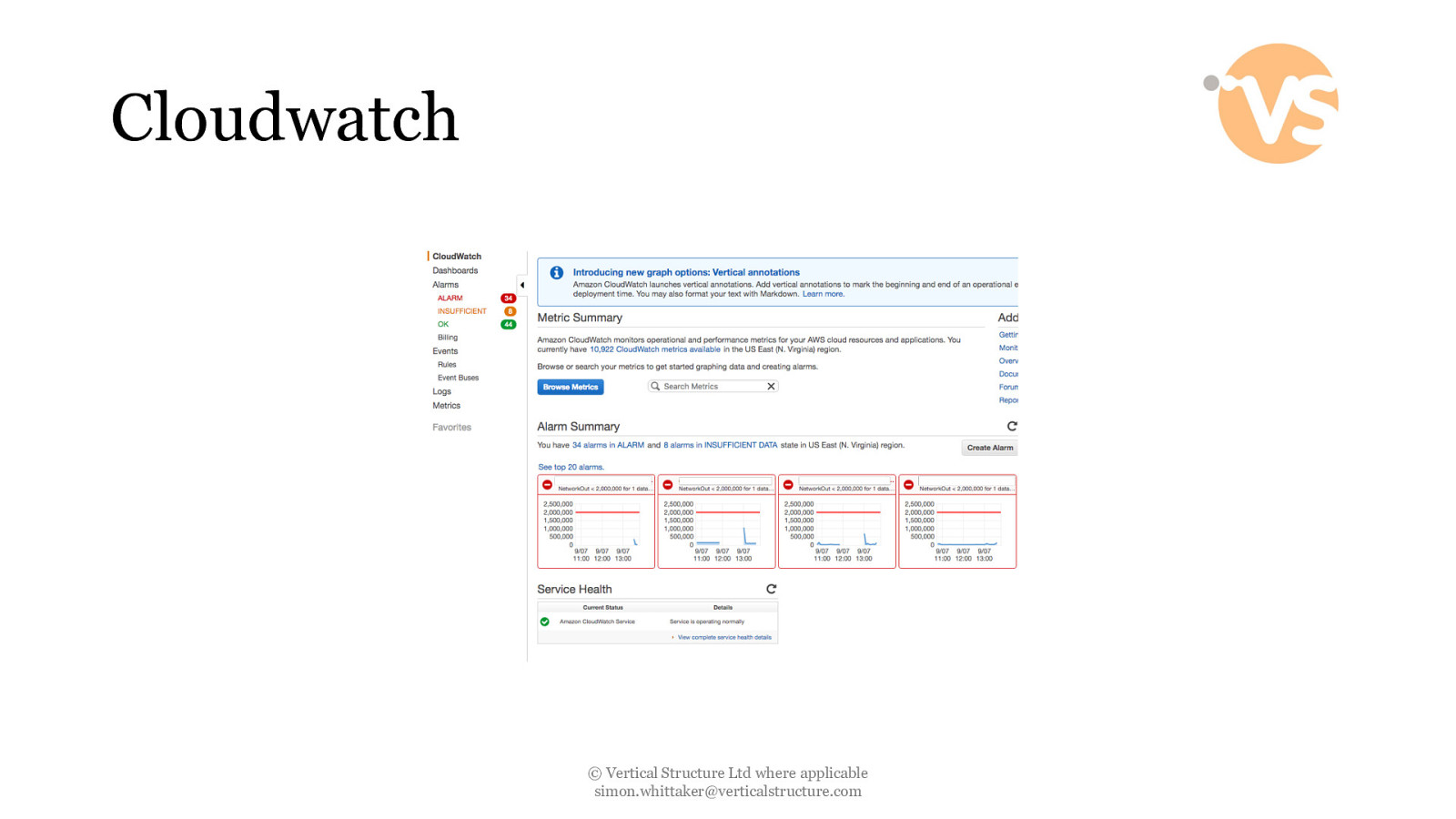
Cloudwatch © Vertical Structure Ltd where applicable [email protected]
Slide 59

Shield – Managed DDoS Protection © Vertical Structure Ltd where applicable [email protected]
Slide 60
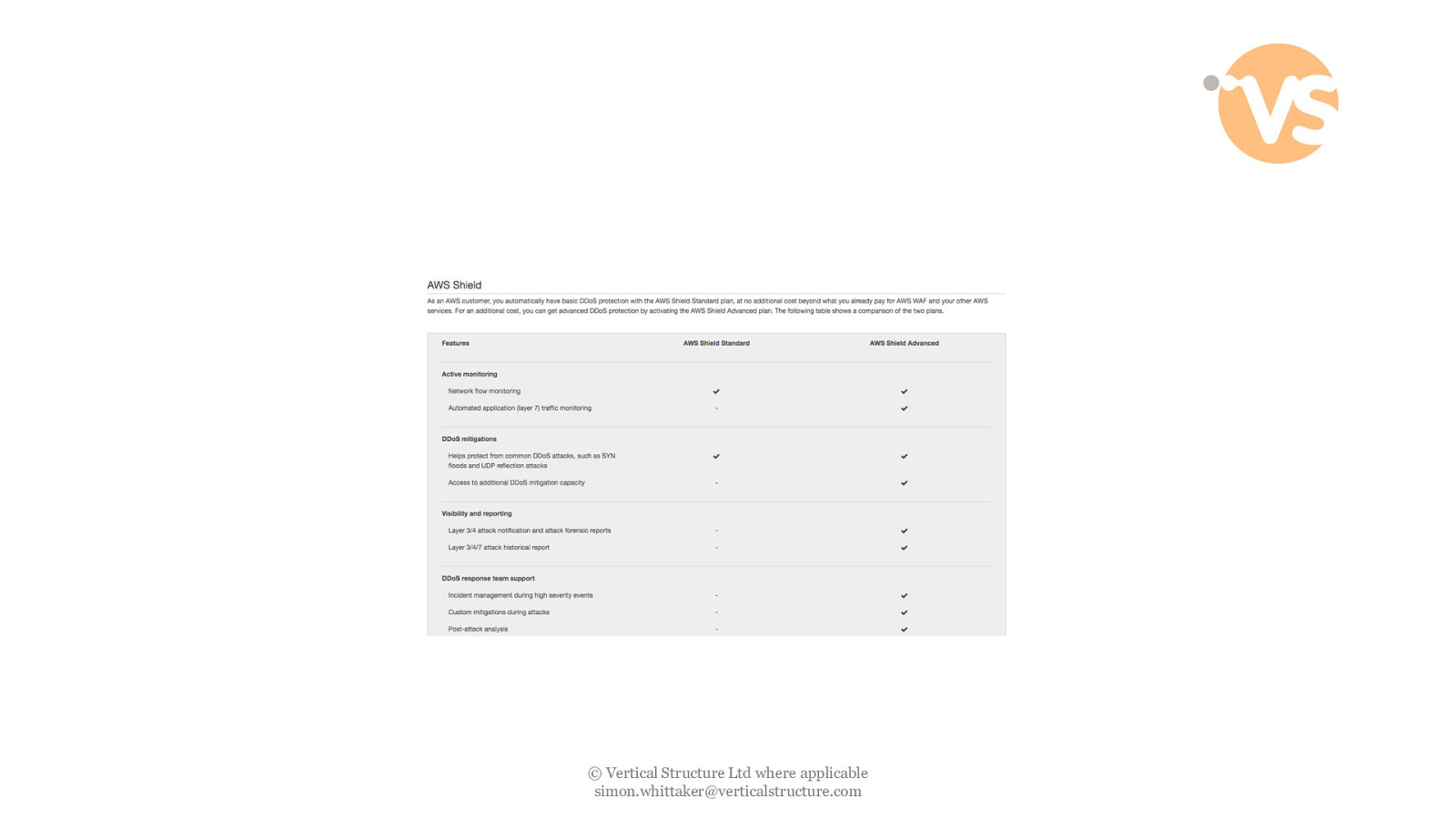
© Vertical Structure Ltd where applicable [email protected]
Slide 61

WAF – Web Application Firewall © Vertical Structure Ltd where applicable [email protected]
Slide 62

AWS Systems Manager © Vertical Structure Ltd where applicable [email protected]
Slide 63

In conclusion • Know and use the tools • It is not practical, there are no simulations • Certificates and keys are “key” • Learning the types of questions will help you • ACloudGuru • Whizlabs © Vertical Structure Ltd where applicable [email protected]
Slide 64

Fancy trying your hand? https://vsltd.co/devopsbelfastnov18