Cyber Security Simon Whittaker Cyber Security Director - Vertical Structure Ltd vsltd.co/cyberSecurityBCCM
Slide 1

Slide 2
Prepare, Protect, Persist ® • Prepare • We help you and your partners to understand how to identify and resolve potential security issues at the earliest stages with hands on ‘hack yourself first’, threat modelling and GDPR compliance workshops as well as security training for non-technical colleagues. • Protect • Using automated and manual penetration testing techniques, we provide a comprehensive security report for your Web and mobile applications, including API testing, and networks. The report highlights potential issues and their resolutions. • Persist • We ensure that your organisation benefits from continual improvements in security levels through information assurance processes, auditing and certification including ISO27001:2013 and Cyber Essentials. © Vertical Structure Ltd where applicable [email protected]
Slide 3

Fundamental Security Concepts The basics © Vertical Structure Ltd where applicable [email protected]
Slide 4
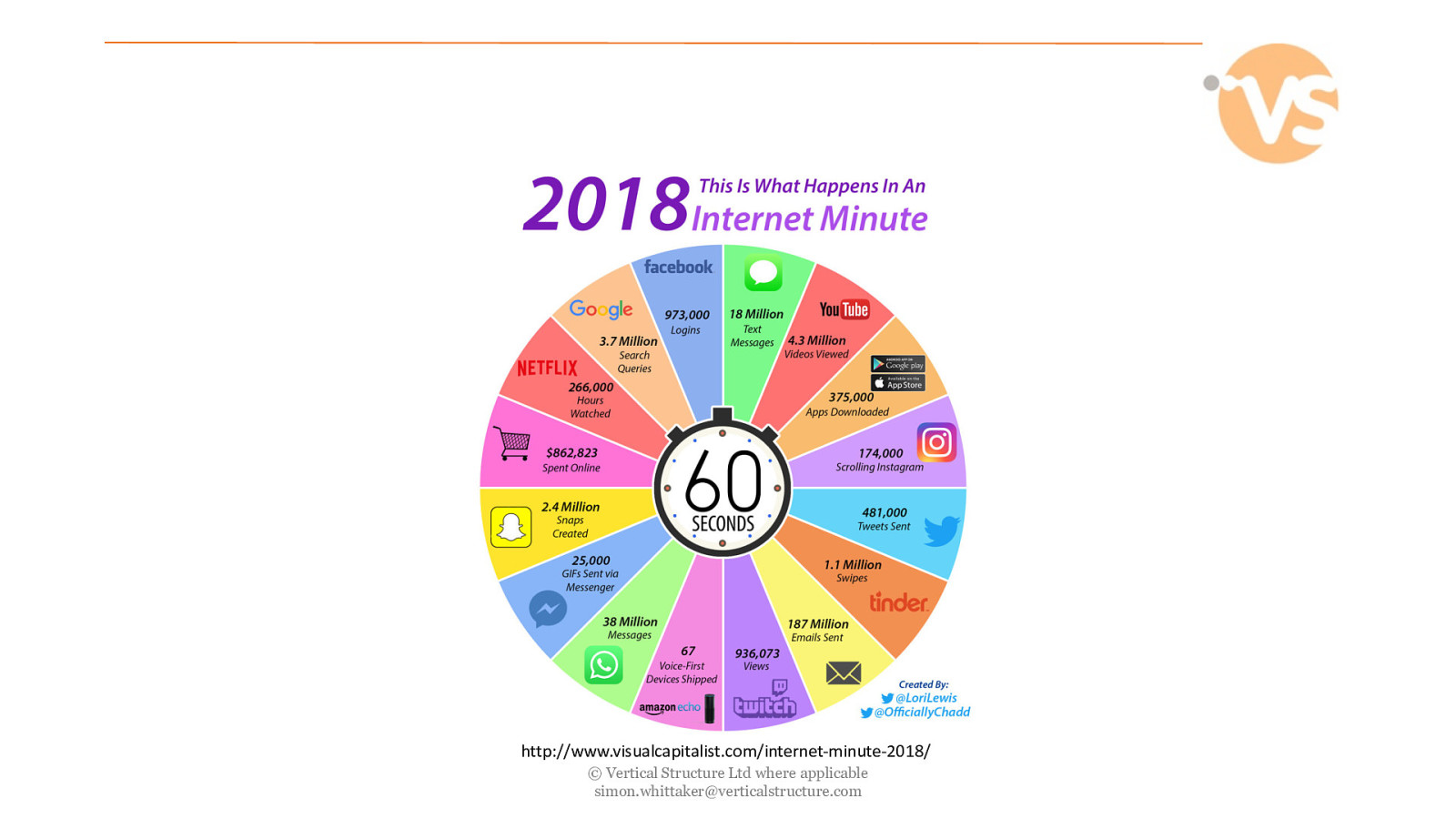
http://www.visualcapitalist.com/internet-minute-2018/ © Vertical Structure Ltd where applicable [email protected]
Slide 5

Security Breaches through the ages • ‘Target’ stores in November 2013 • 40 million customer records stolen • ‘Neiman Marcus’ during 2013 • Millions affected • ‘Home Depot’ in September 2014 • 56 million credit card details stolen • ‘JPMorgan Chase’ data breach during 2014 • 76 million households and 7 million small businesses • ‘Sony Pictures’ hack in November 2014 • Massive amounts of confidential internal information • OPM – June 2015 • Ashley Madison – July 2015 • Talk Talk – November 2015 • LinkedIn – revealed May 2016 • 117 million user details • Dropbox – revealed August 2016 • 68 million user details • Yahoo – revealed Dec 2016 • 1 billion user details… • • • • Equifax - September 2017 Butlins – August 2018 Exactis – June 2018 British Airways – September 2018 • Included 5.6 million finger prints https://www.privacyrights.org/data-breaches © Vertical Structure Ltd where applicable [email protected]
Slide 6
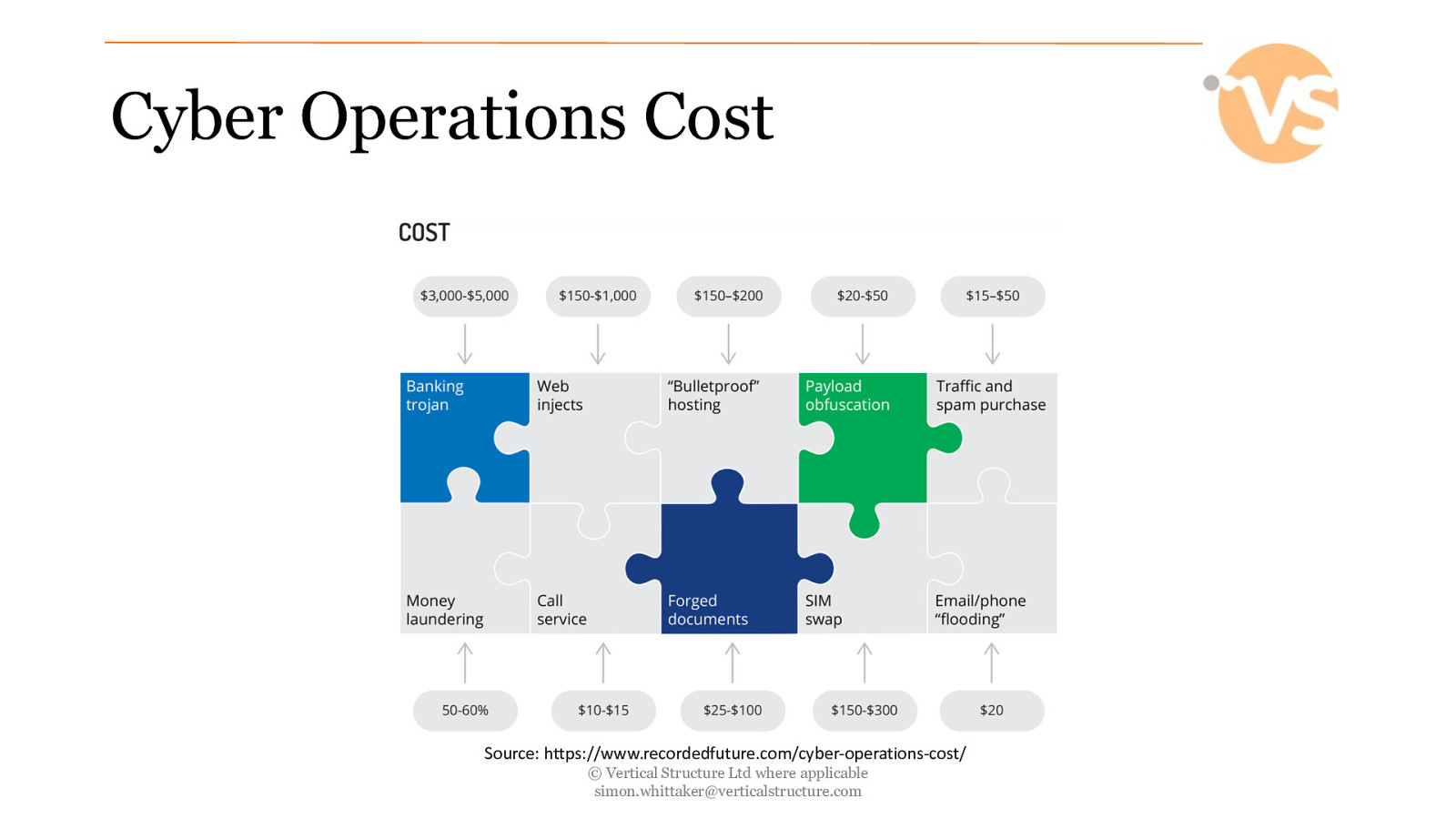
Cyber Operations Cost Source: https://www.recordedfuture.com/cyber-operations-cost/ © Vertical Structure Ltd where applicable [email protected]
Slide 7
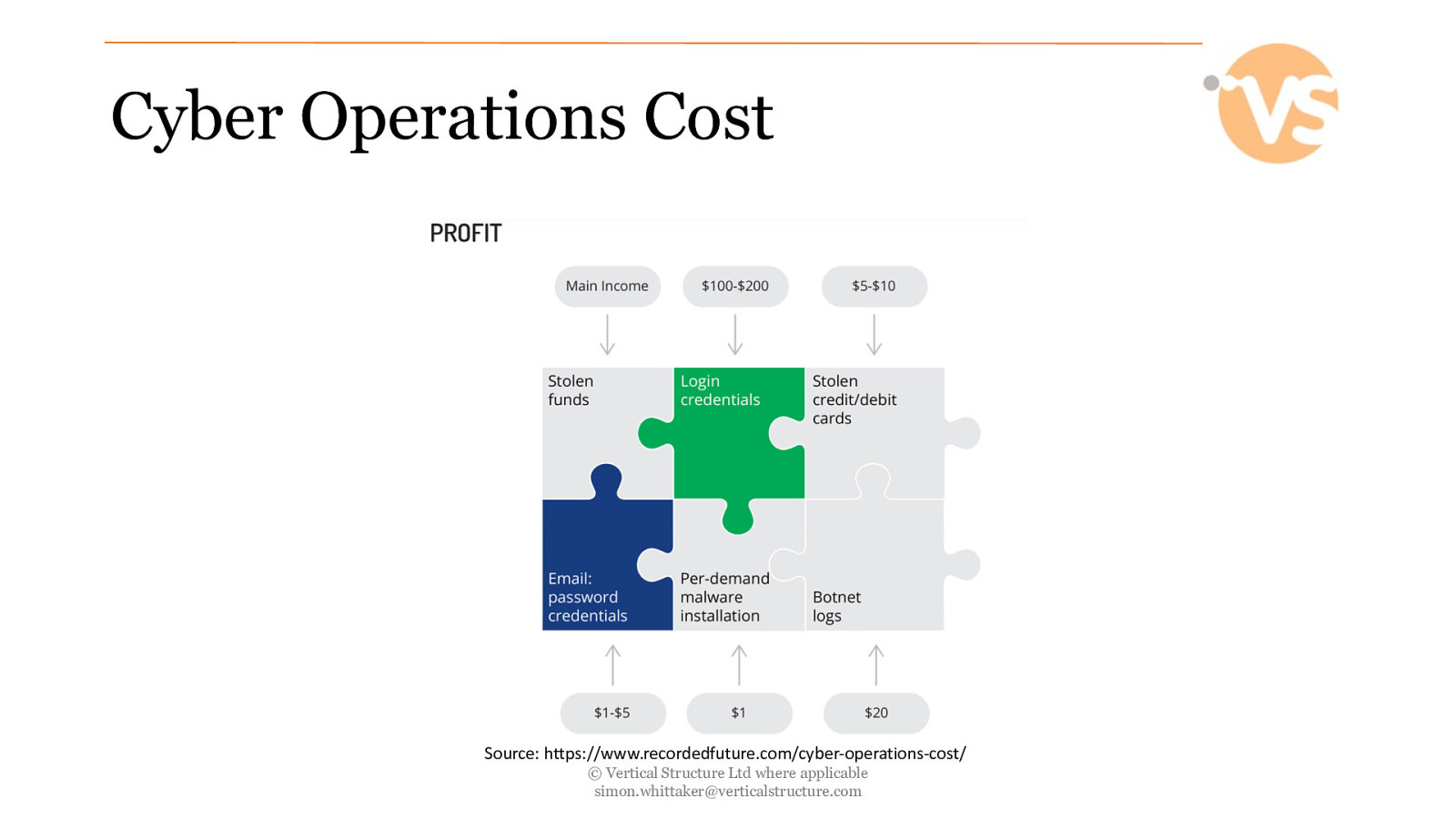
Cyber Operations Cost Source: https://www.recordedfuture.com/cyber-operations-cost/ © Vertical Structure Ltd where applicable [email protected]
Slide 8
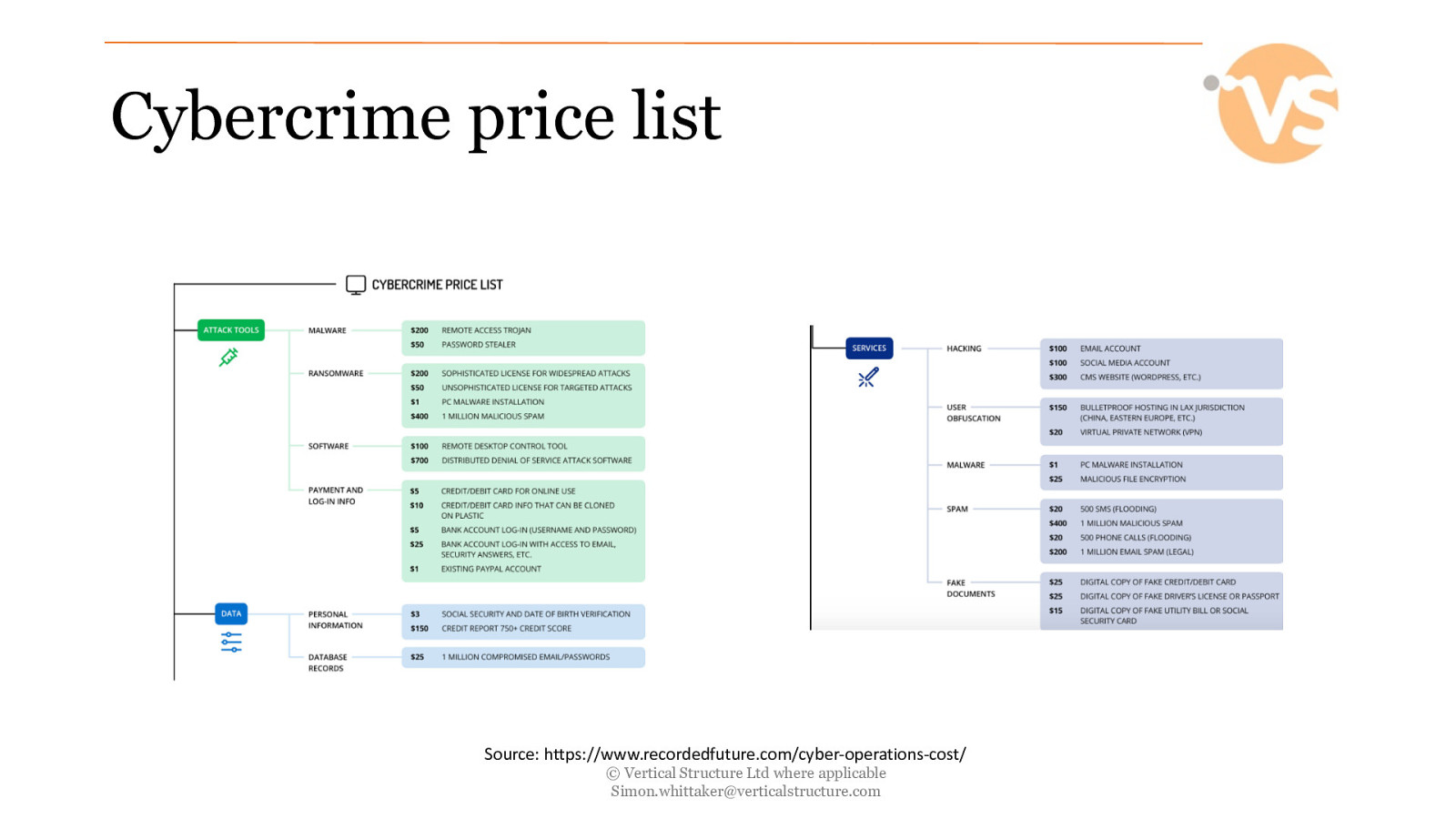
Cybercrime price list Source: https://www.recordedfuture.com/cyber-operations-cost/ © Vertical Structure Ltd where applicable [email protected]
Slide 9

”Hackers” – the stock image © Vertical Structure Ltd where applicable [email protected]
Slide 10

The reality © Vertical Structure Ltd where applicable [email protected]
Slide 11

• “It’s time to think differently about cyber risk – ditching the talk of hackers – and recognising that our businesses are being targeted by ruthless criminal entrepreneurs with business plans and extensive resources – intent on fraud, extortion or theft of hard won intellectual property.” • Paul Taylor, UK Head of Cyber Security, KPMG • http://bit.ly/takingTheOffensive © Vertical Structure Ltd where applicable [email protected]
Slide 12

© Vertical Structure Ltd where applicable [email protected]
Slide 13
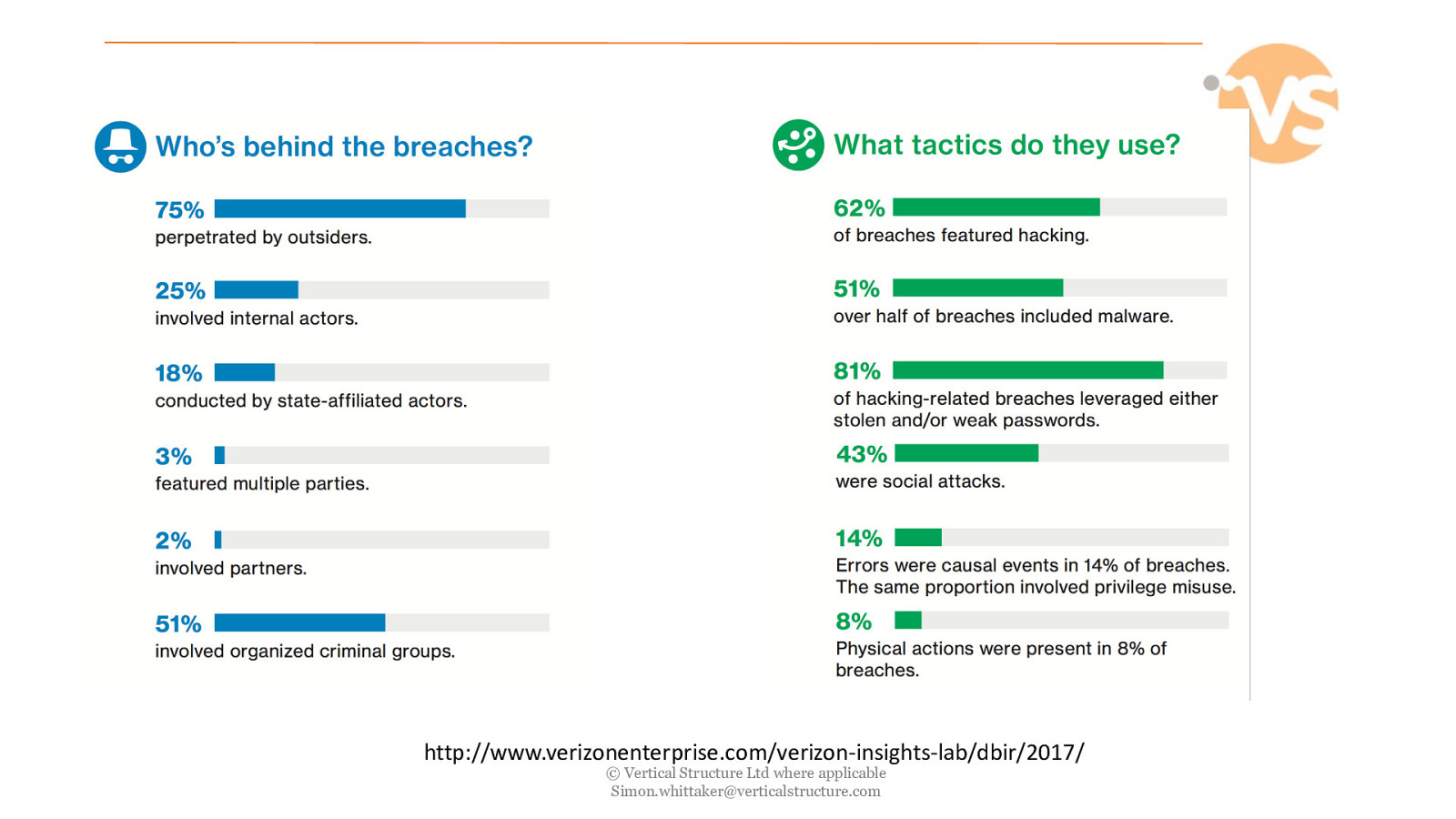
http://www.verizonenterprise.com/verizon-insights-lab/dbir/2017/ © Vertical Structure Ltd where applicable [email protected]
Slide 14
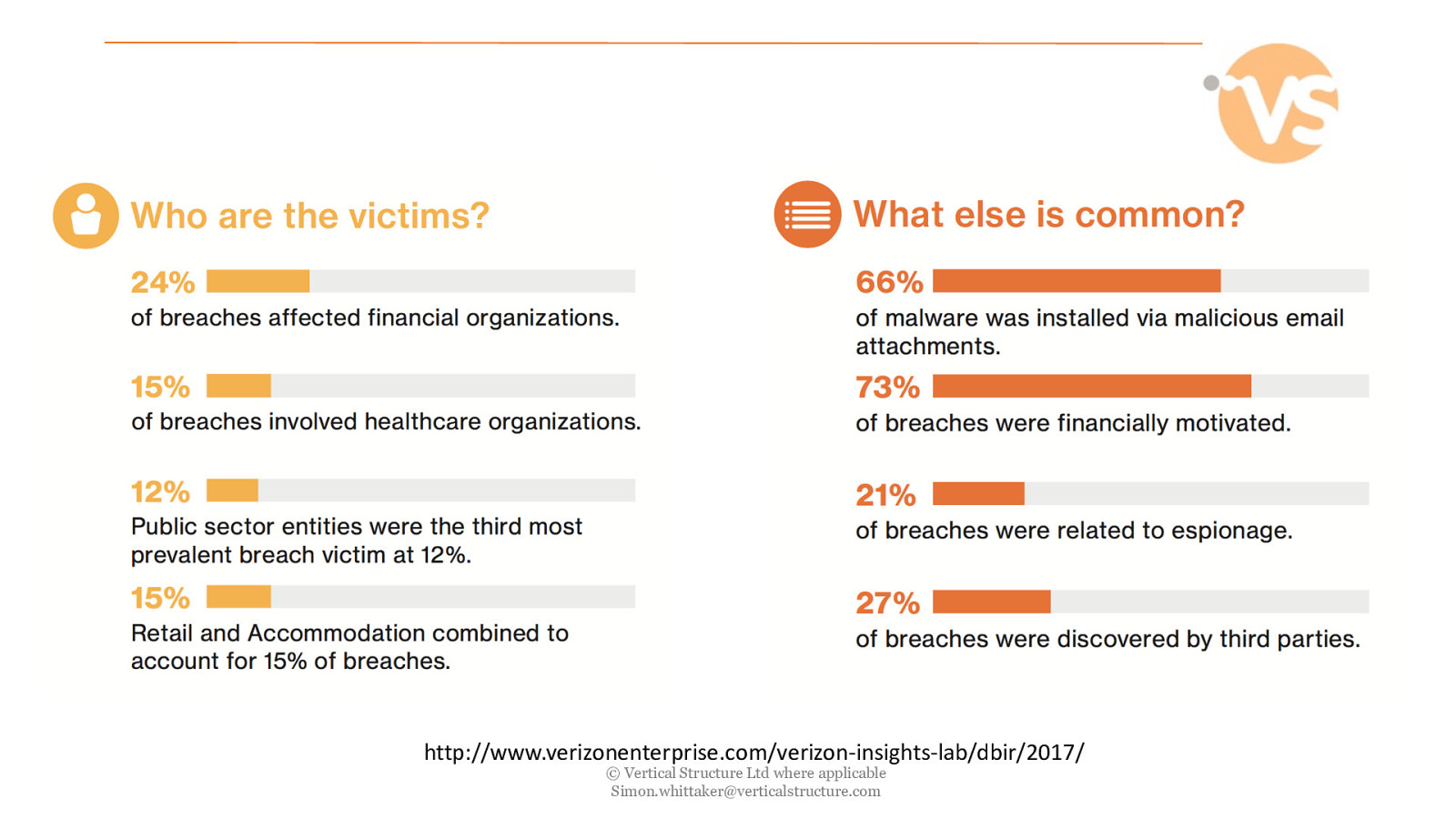
http://www.verizonenterprise.com/verizon-insights-lab/dbir/2017/ © Vertical Structure Ltd where applicable [email protected]
Slide 15
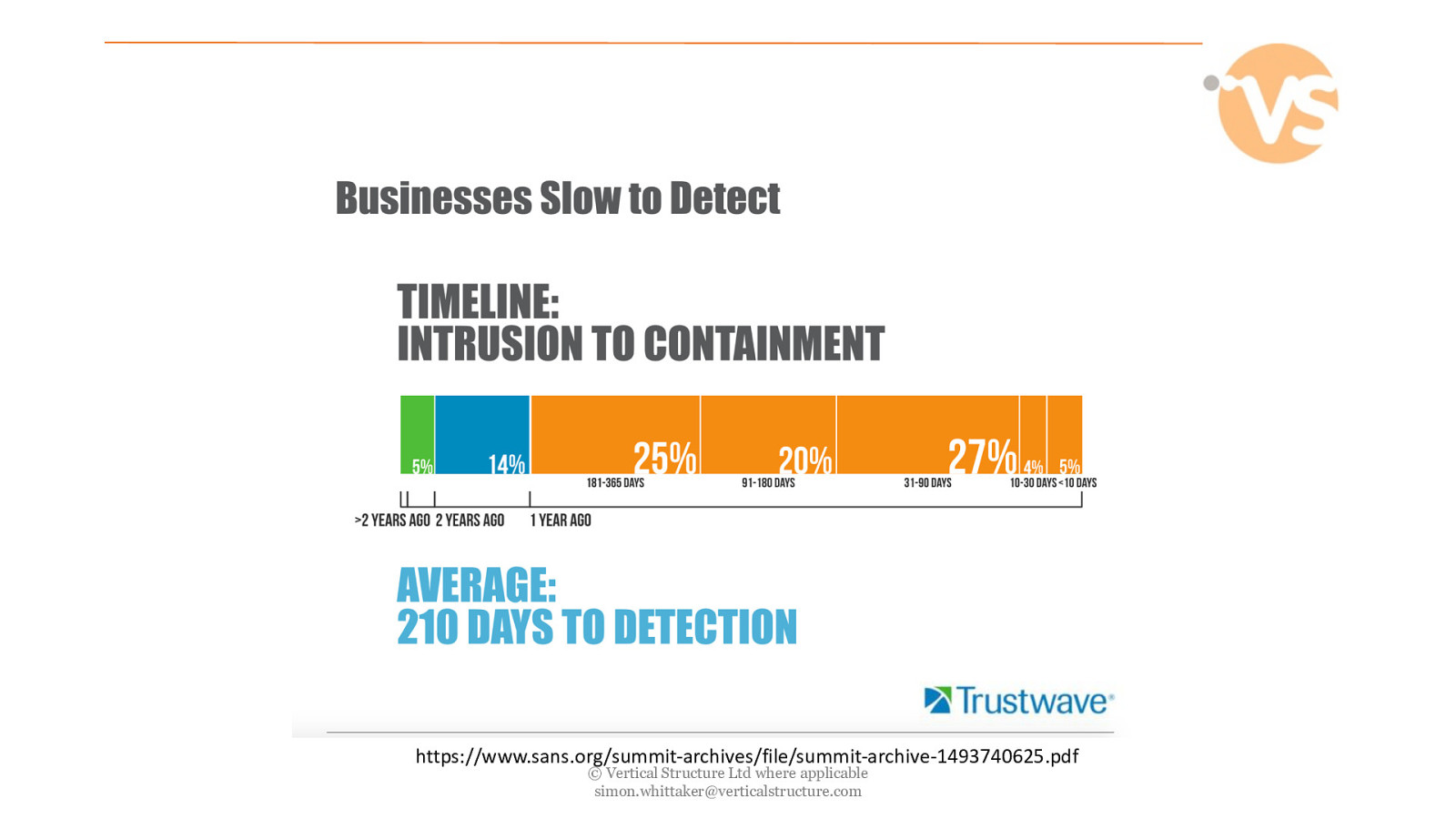
https://www.sans.org/summit-archives/file/summit-archive-1493740625.pdf © Vertical Structure Ltd where applicable [email protected]
Slide 16
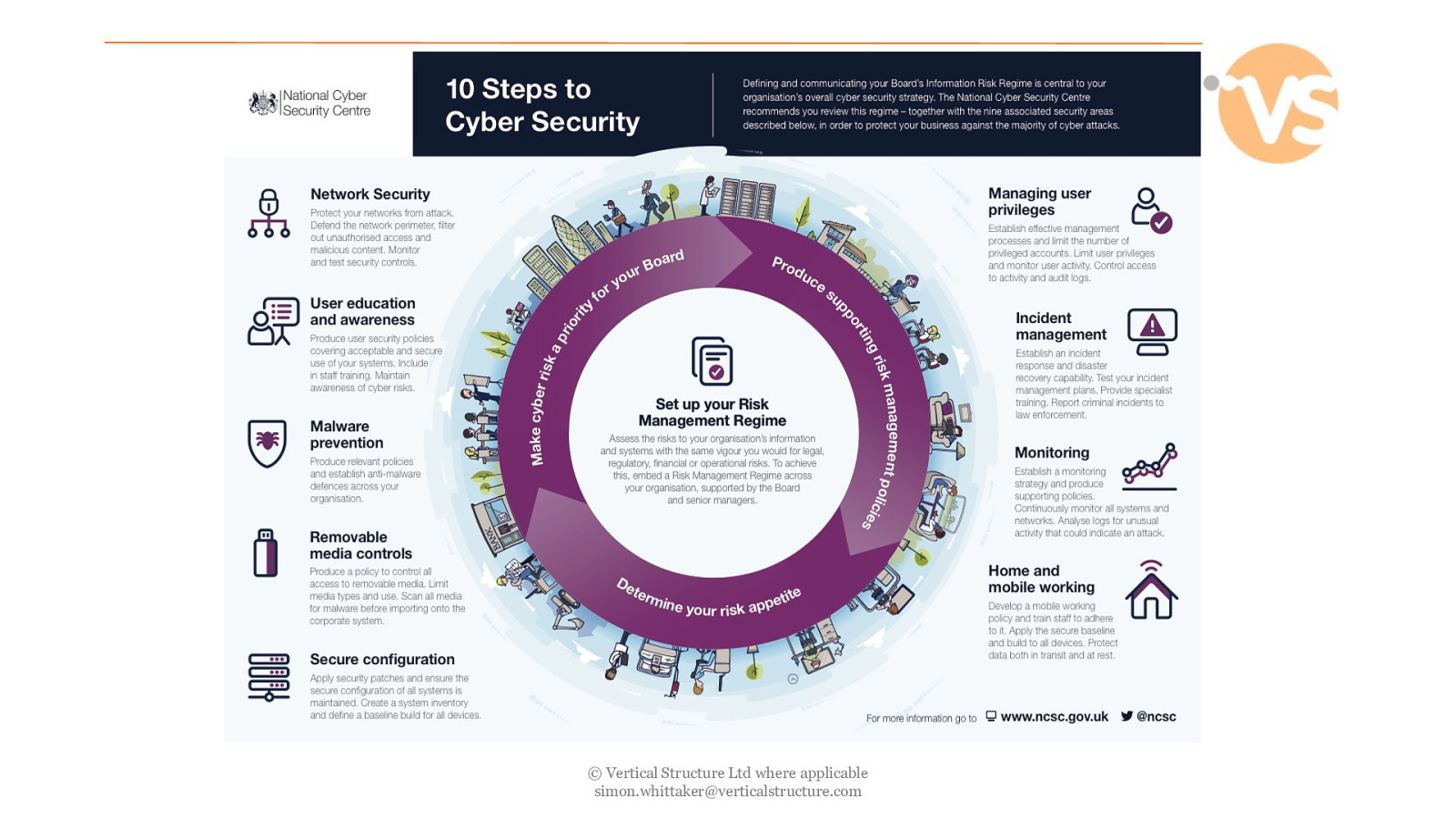
© Vertical Structure Ltd where applicable [email protected]
Slide 17

Risk Management Regime © Vertical Structure Ltd where applicable [email protected]
Slide 18

Network Security © Vertical Structure Ltd where applicable [email protected]
Slide 19
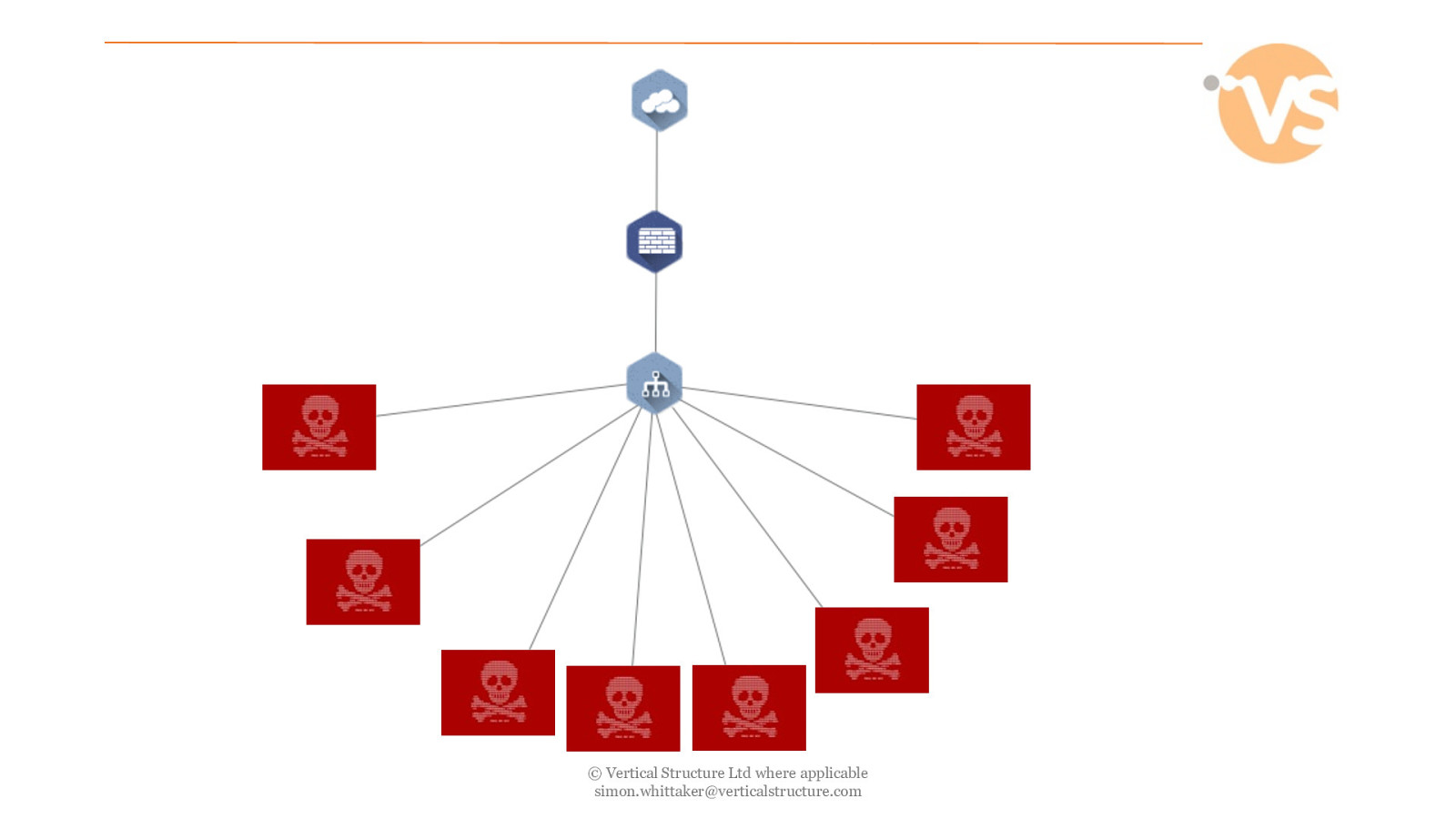
© Vertical Structure Ltd where applicable [email protected]
Slide 20

User Education and Awareness © Vertical Structure Ltd where applicable [email protected]
Slide 21

Listen to your users • Amy has her passwords written on a post-it note under her keyboard. • Brian keeps backups of important data on his personal pen drive. • Claire let David use her account – just for five minutes – while she went to make a cup of tea. • People break the rules because they need to get the job done. https://www.ncsc.gov.uk/blog-post/security-breaches-communication-what-are-your-users-telling-you © Vertical Structure Ltd where applicable [email protected]
Slide 22

Social Engineering Social engineering, in the context of information security, refers to psychological manipulation of people into performing actions or divulging confidential information. A type of confidence trick for the purpose of information gathering, fraud, or system access, it differs from a traditional “con” in that it is often one of many steps in a more complex fraud scheme. The term “social engineering” as an act of psychological manipulation is also associated with the social sciences, but its usage has caught on among computer and information security professionals. Source: https://en.wikipedia.org/wiki/Social_engineering_(security) © Vertical Structure Ltd where applicable [email protected]
Slide 23
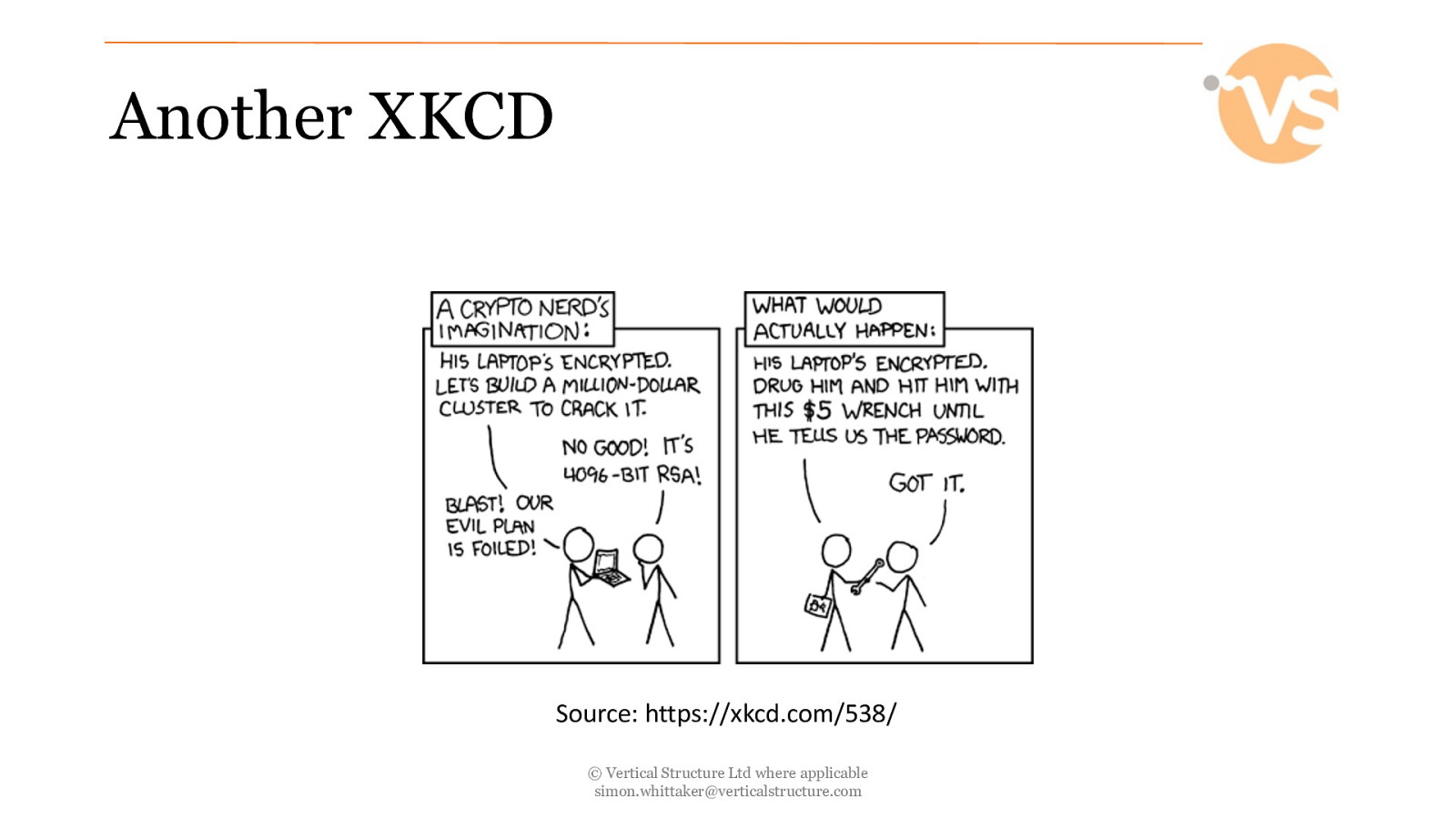
Another XKCD Source: https://xkcd.com/538/ © Vertical Structure Ltd where applicable [email protected]
Slide 24
Social Engineering – Real Life • We recognise: • Voice sounds and patterns • Facial features • Mannerisms • Relationships and Trust are formed © Vertical Structure Ltd where applicable [email protected]
Slide 25

Social Engineering – Online • Providers are geographically diverse – often we might not meet people that are supporting us or that we’re working with - relationships aren’t formed • Information often stored in 3rd party helpdesk systems • Poor security measures • Some banks have a business fraud prevention call originating from an unknown number, they ask for your bank details to approve/reject transactions • Mobile phone companies call and ask for name, DoB, phone number for data protection purposes before proceeding with the call • The system is broken © Vertical Structure Ltd where applicable [email protected]
Slide 26
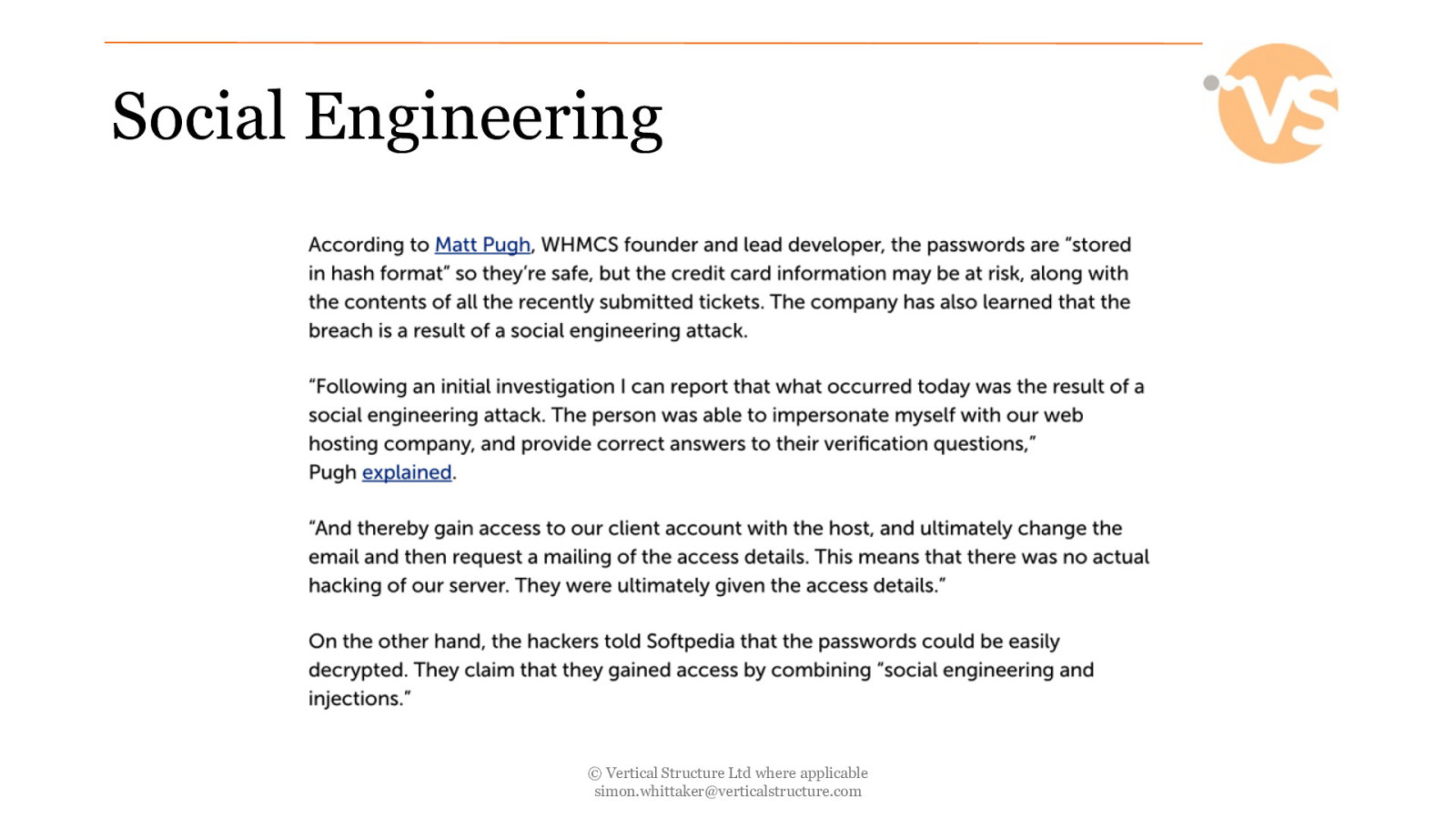
Social Engineering © Vertical Structure Ltd where applicable [email protected]
Slide 27

Social Engineering - What can be done? • Establishing frameworks of trust on an employee/personnel level (i.e., specify and train personnel when/where/why/how sensitive information should be handled) • Identifying which information is sensitive and evaluating its exposure to social engineering and breakdowns in security systems (building, computer system, etc.) • Establishing security protocols, policies, and procedures for handling sensitive information. © Vertical Structure Ltd where applicable [email protected]
Slide 28

Social Engineering - What can be done? • Training employees in security protocols relevant to their position. (e.g., in situations such as tailgating, if a person’s identity cannot be verified, then employees must be trained to politely refuse.) • Performing unannounced, periodic tests of the security framework. • Reviewing the above steps regularly: no solutions to information integrity are perfect. • Using a waste management service that has dumpsters with locks on them, with keys to them limited only to the waste management company and the cleaning staff. Locating the dumpster either in view of employees such that trying to access it carries a risk of being seen or caught or behind a locked gate or fence where the person must trespass before they can attempt to access the dumpster. © Vertical Structure Ltd where applicable [email protected]
Slide 29
Malware prevention © Vertical Structure Ltd where applicable [email protected]
Slide 30
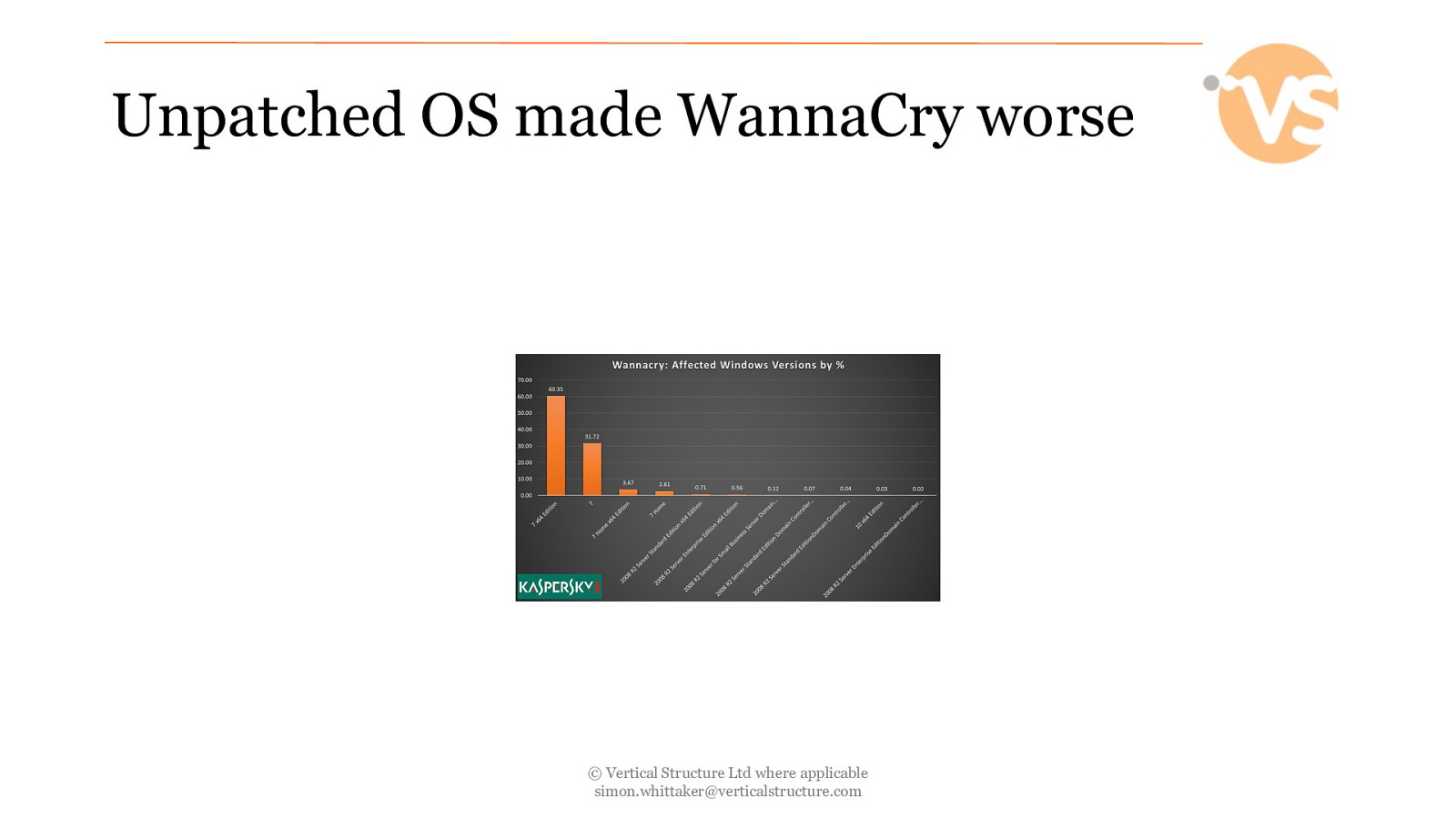
Unpatched OS made WannaCry worse © Vertical Structure Ltd where applicable [email protected]
Slide 31

Removable Media Controls © Vertical Structure Ltd where applicable [email protected]
Slide 32

Secure Configuration © Vertical Structure Ltd where applicable [email protected]
Slide 33
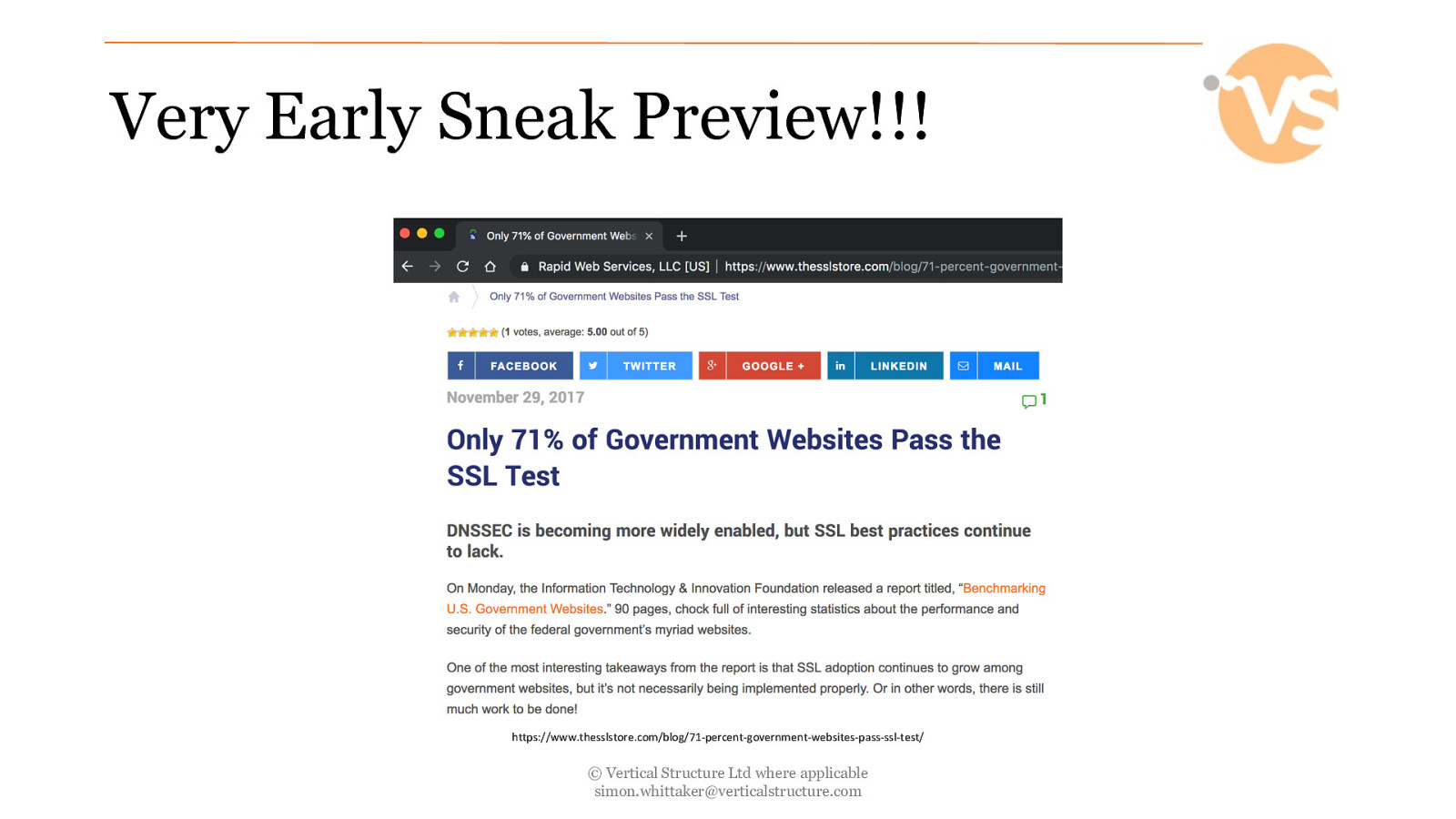
Very Early Sneak Preview!!! https://www.thesslstore.com/blog/71-percent-government-websites-pass-ssl-test/ © Vertical Structure Ltd where applicable [email protected]
Slide 34
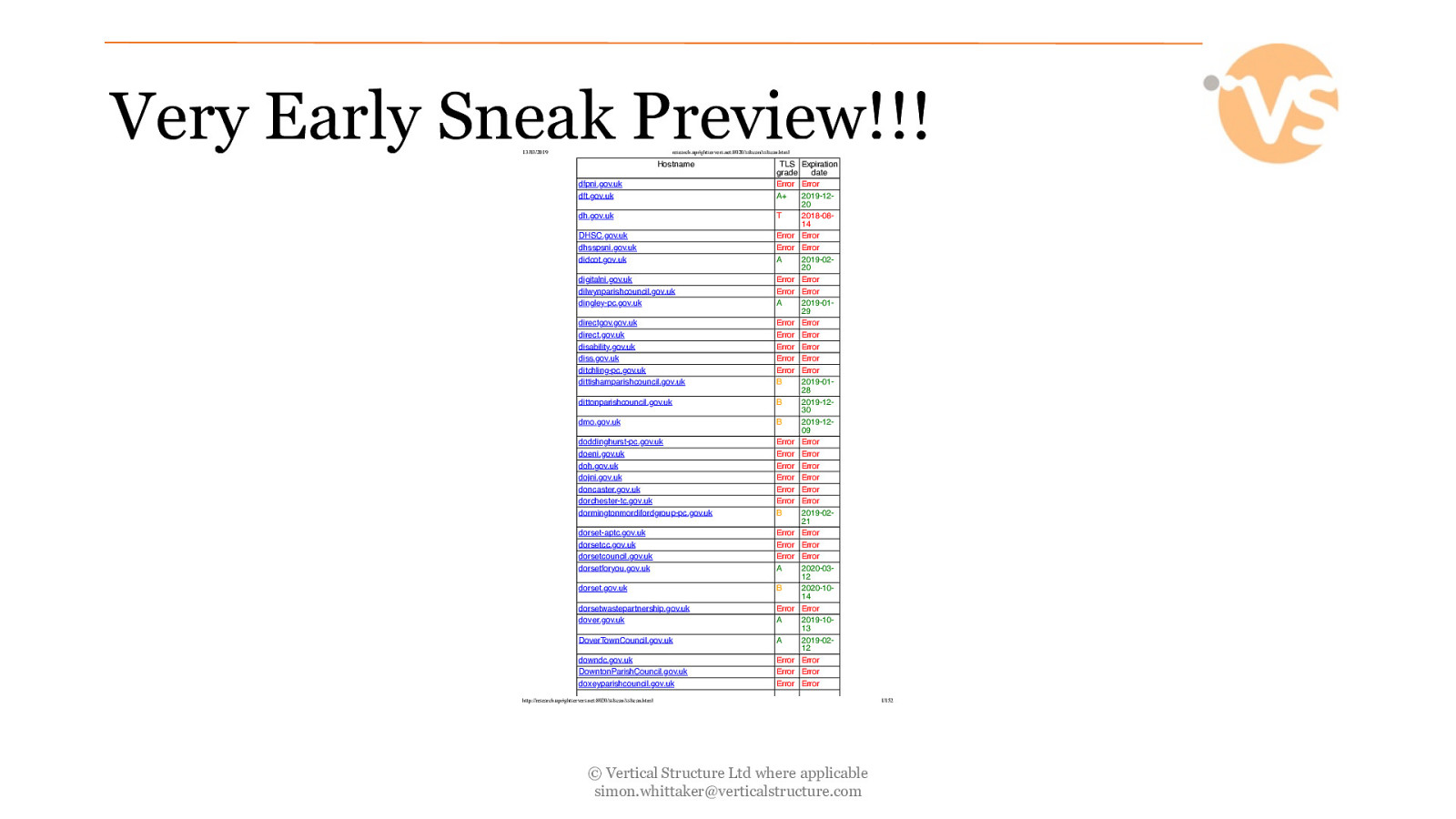
Very Early Sneak Preview!!! 13/03/2019 research.uprightservers.net:8020/sslscan/sslscan.html Hostname dfpni.gov.uk dft.gov.uk dh.gov.uk DHSC.gov.uk dhsspsni.gov.uk didcot.gov.uk digitalni.gov.uk dilwynparishcouncil.gov.uk dingley-pc.gov.uk directgov.gov.uk direct.gov.uk disability.gov.uk diss.gov.uk ditchling-pc.gov.uk dittishamparishcouncil.gov.uk dittonparishcouncil.gov.uk dmo.gov.uk doddinghurst-pc.gov.uk doeni.gov.uk doh.gov.uk dojni.gov.uk doncaster.gov.uk dorchester-tc.gov.uk dormingtonmordifordgroup-pc.gov.uk dorset-aptc.gov.uk dorsetcc.gov.uk dorsetcouncil.gov.uk dorsetforyou.gov.uk dorset.gov.uk dorsetwastepartnership.gov.uk dover.gov.uk DoverTownCouncil.gov.uk downdc.gov.uk DowntonParishCouncil.gov.uk doxeyparishcouncil.gov.uk TLS Expiration grade date Error Error A+ 2019-1220 T 2018-0814 Error Error Error Error A 2019-0220 Error Error Error Error A 2019-0129 Error Error Error Error Error Error Error Error Error Error B 2019-0128 B 2019-1230 B 2019-1209 Error Error Error Error Error Error Error Error Error Error Error Error B 2019-0221 Error Error Error Error Error Error A 2020-0312 B 2020-1014 Error Error A 2019-1013 A 2019-0212 Error Error Error Error Error Error http://research.uprightservers.net:8020/sslscan/sslscan.html © Vertical Structure Ltd where applicable [email protected] 1/152
Slide 35
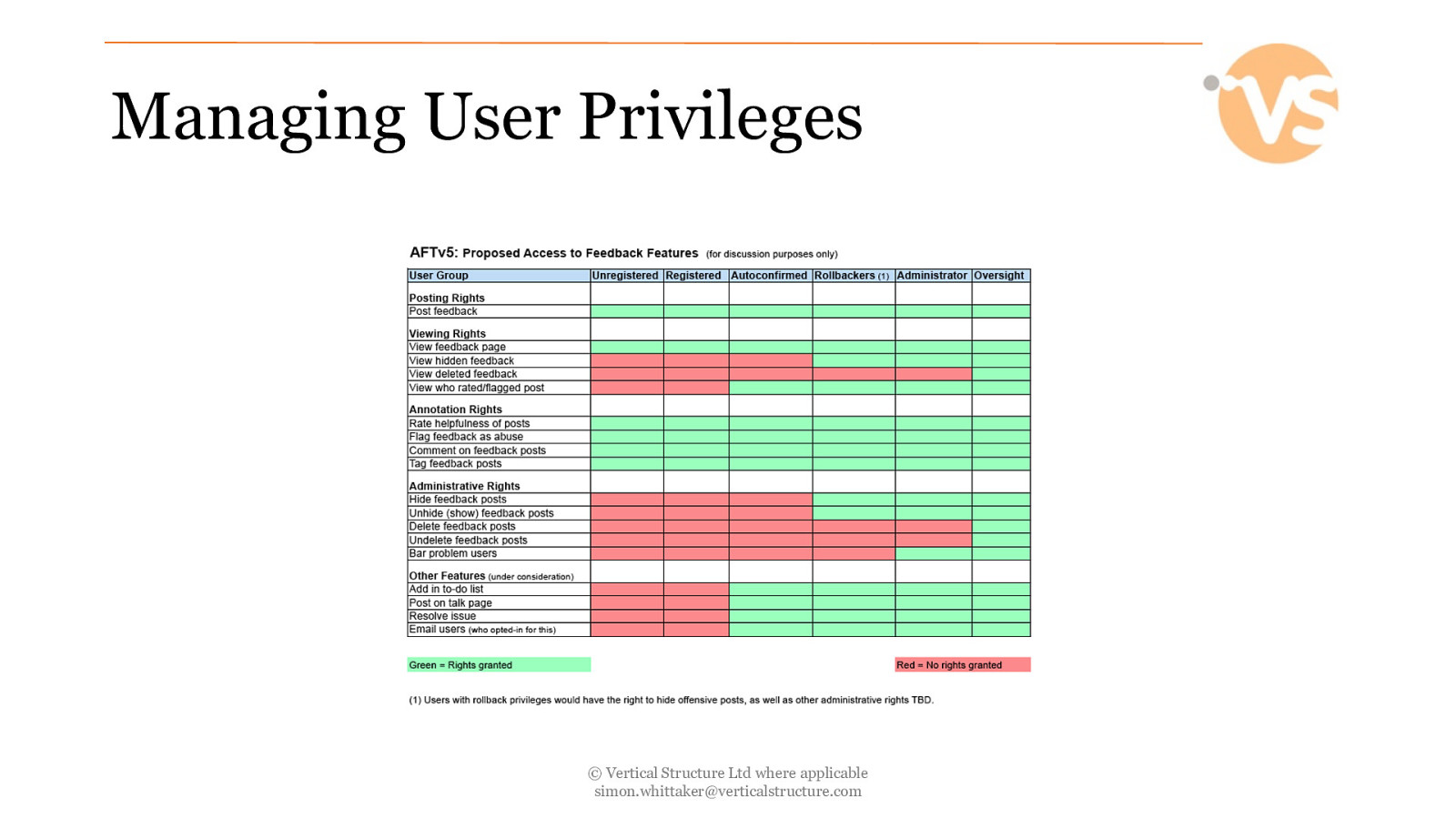
Managing User Privileges © Vertical Structure Ltd where applicable [email protected]
Slide 36

Incident Management © Vertical Structure Ltd where applicable [email protected]
Slide 37
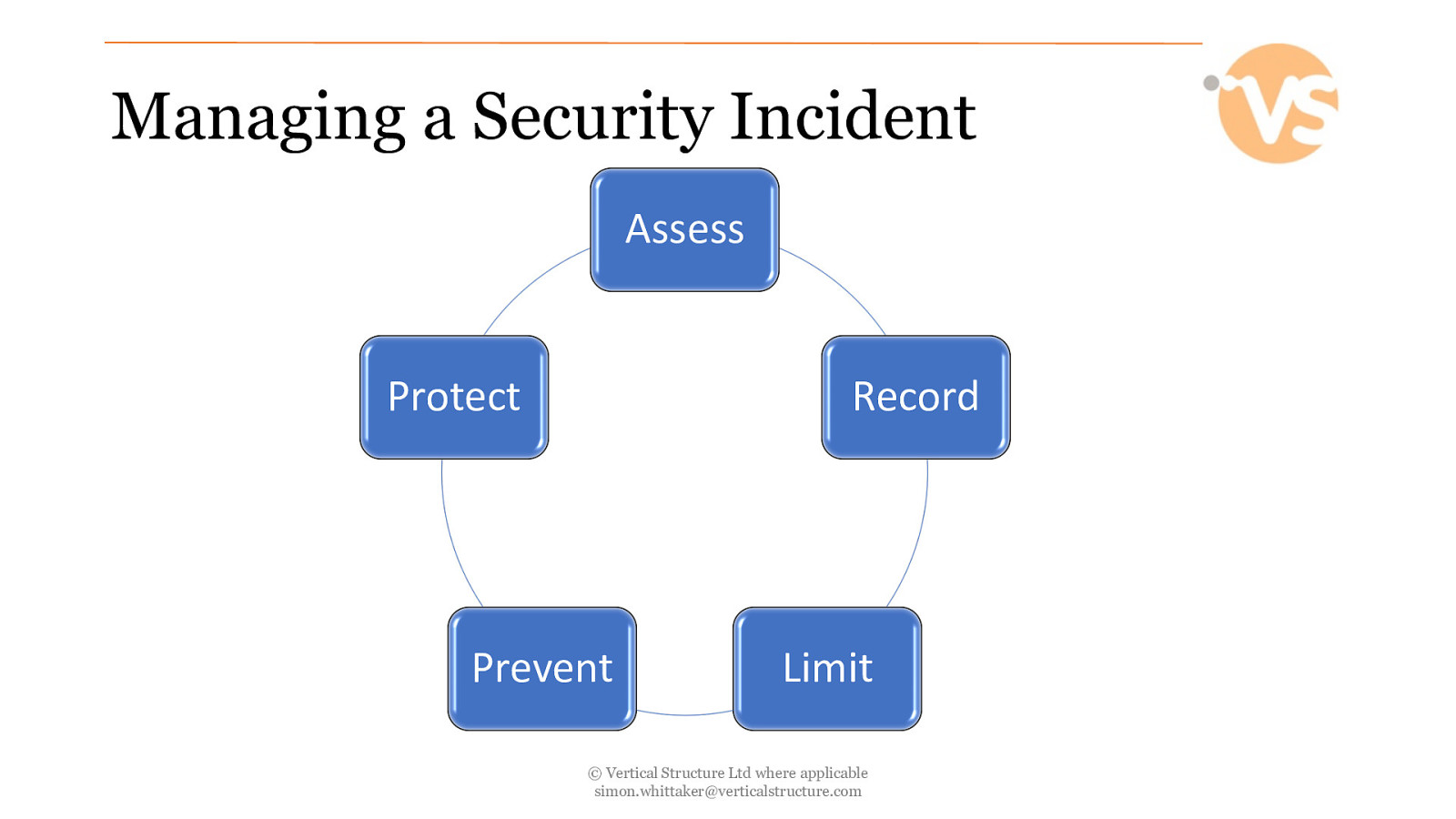
Managing a Security Incident Assess Protect Record Prevent Limit © Vertical Structure Ltd where applicable [email protected]
Slide 38

Monitoring © Vertical Structure Ltd where applicable [email protected]
Slide 39

Home and Mobile Working © Vertical Structure Ltd where applicable [email protected]
Slide 40
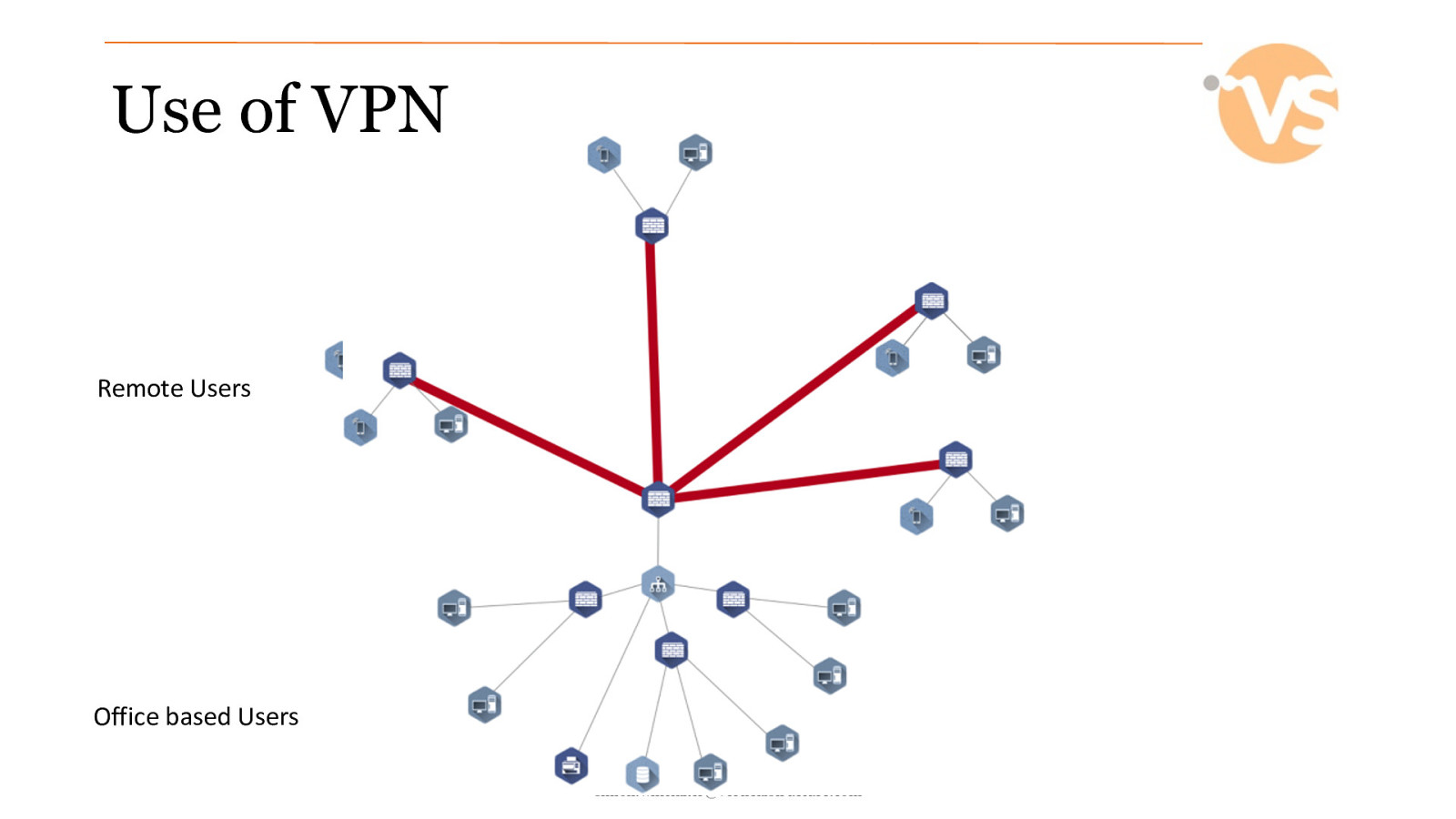
Use of VPN Remote Users Office based Users © Vertical Structure Ltd where applicable [email protected]
Slide 41

Why use a VPN? • Secure your connection back to base • Prevent traffic sniffing on “free” wifi networks • Allow access to internal resources without opening holes in the firewall • Control internet access to only “safe” places © Vertical Structure Ltd where applicable [email protected]
Slide 42

Passwords © Vertical Structure Ltd where applicable [email protected]
Slide 43

Have you been pwned? www.haveibeenpwned.com © Vertical Structure Ltd where applicable [email protected]
Slide 44

Password Policies Users are generally told to remember passwords, and to not share them, re-use them, or write them down. But the typical user has dozens of passwords to remember – not just yours. Regular password changing harms rather than improves security, so avoid placing this burden on users. However, users must change their passwords on indication or suspicion of compromise. Gov.uk advice on passwords https://www.ncsc.gov.uk/guidance/password-guidance-summary-how-protect-against-password-guessing-attacks © Vertical Structure Ltd where applicable [email protected]
Slide 45

Password Guidance 1. 2. 3. 4. 5. 6. 7. Change all default passwords Help users cope with password overload Understand the limitations of user-generated passwords Understand the limitations of machine-generated passwords Prioritise administrator and remote user accounts Use account lockout and protective monitoring Don’t store passwords as plain text © Vertical Structure Ltd where applicable [email protected]
Slide 46
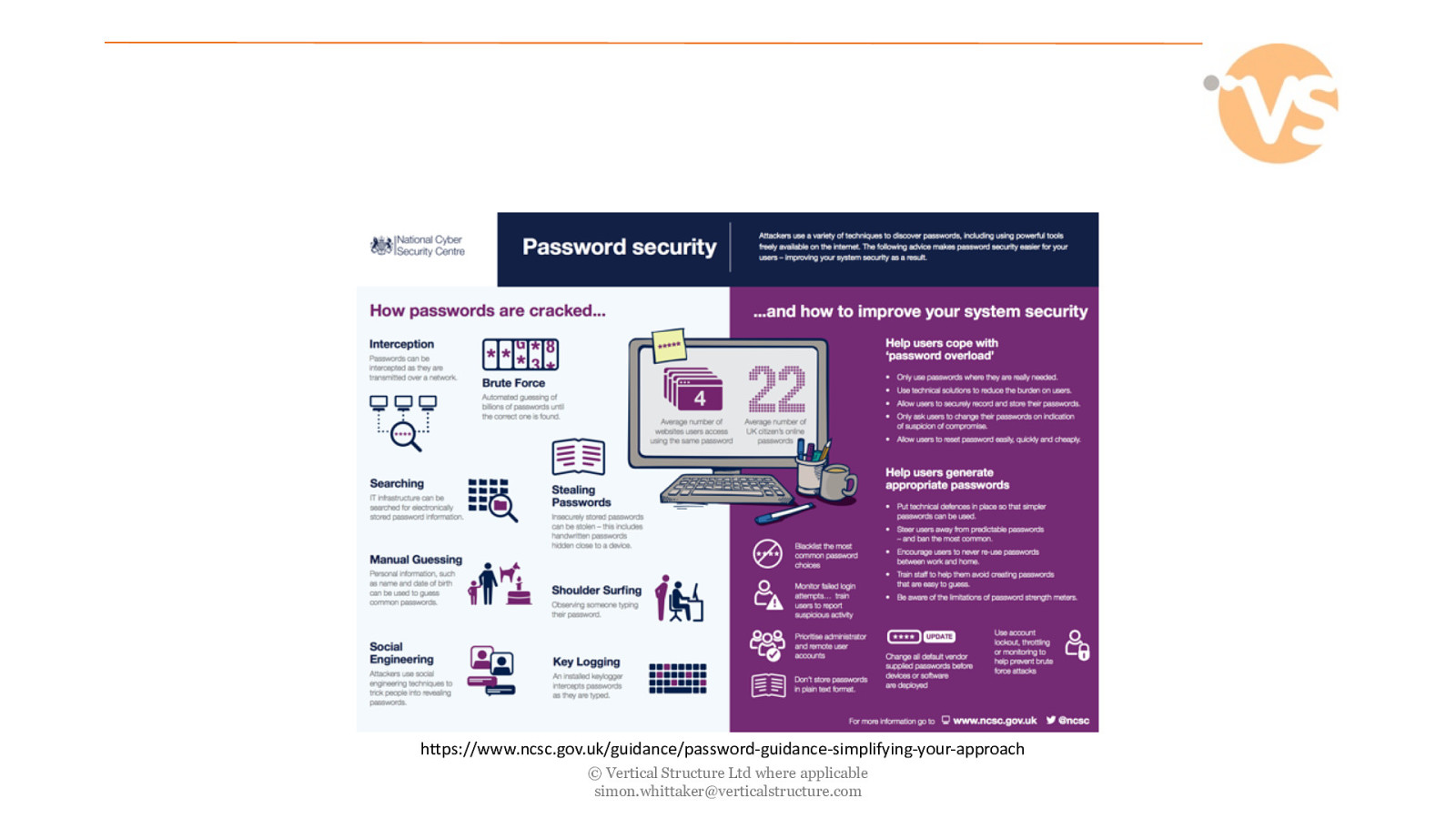
https://www.ncsc.gov.uk/guidance/password-guidance-simplifying-your-approach © Vertical Structure Ltd where applicable [email protected]
Slide 47
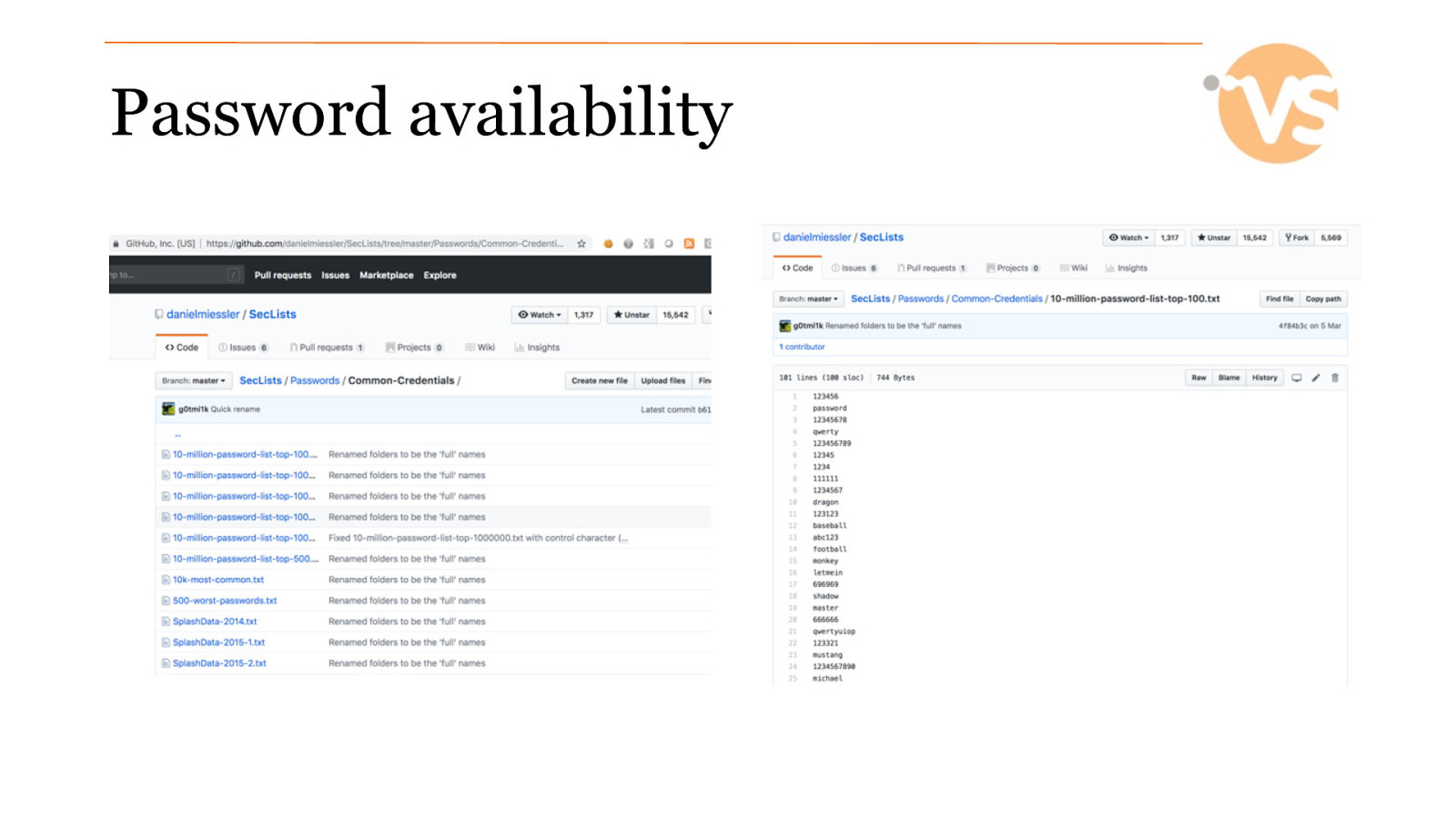
Password availability
Slide 48
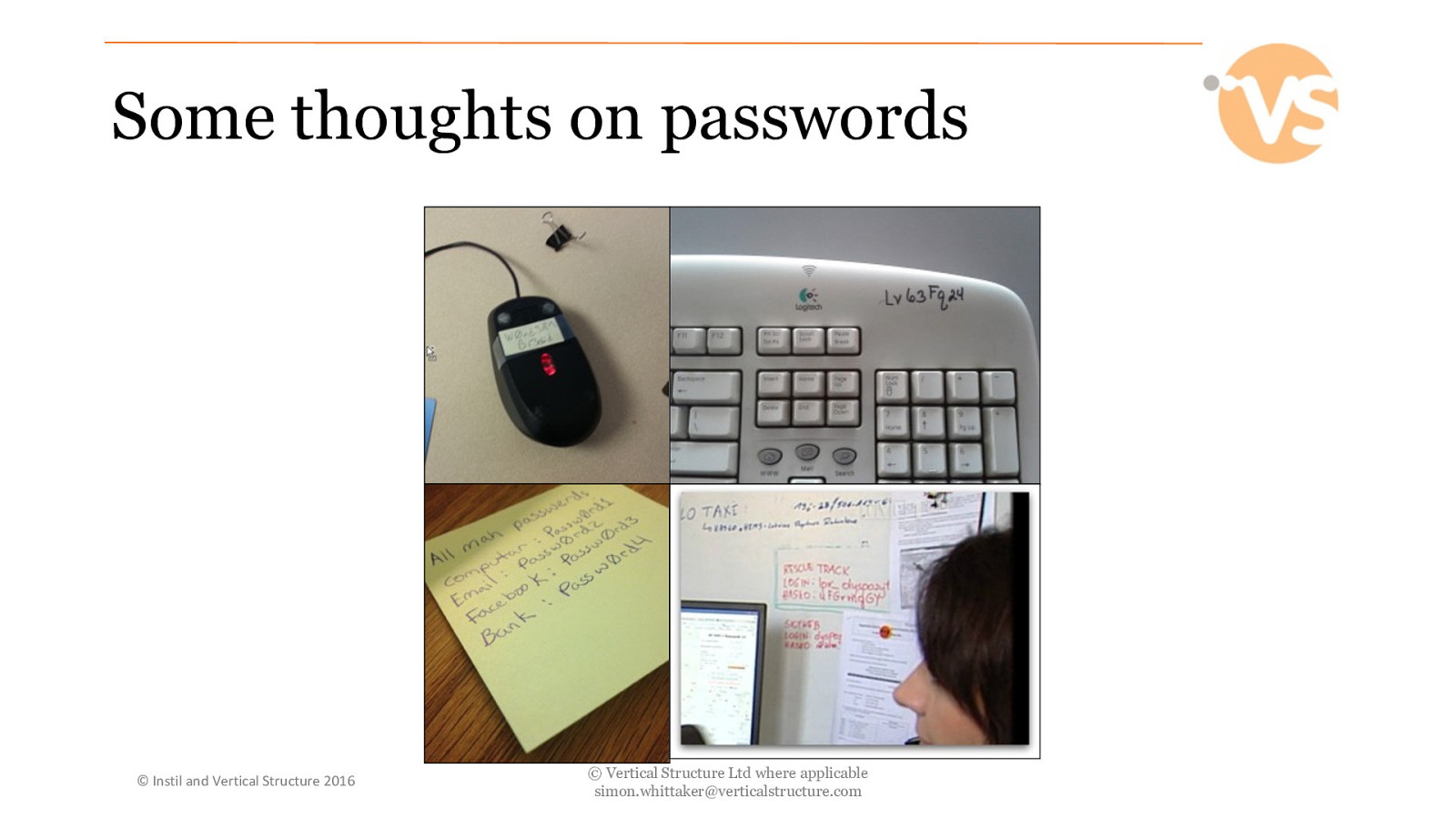
Some thoughts on passwords © Instil and Vertical Structure 2016 © Vertical Structure Ltd where applicable [email protected]
Slide 49
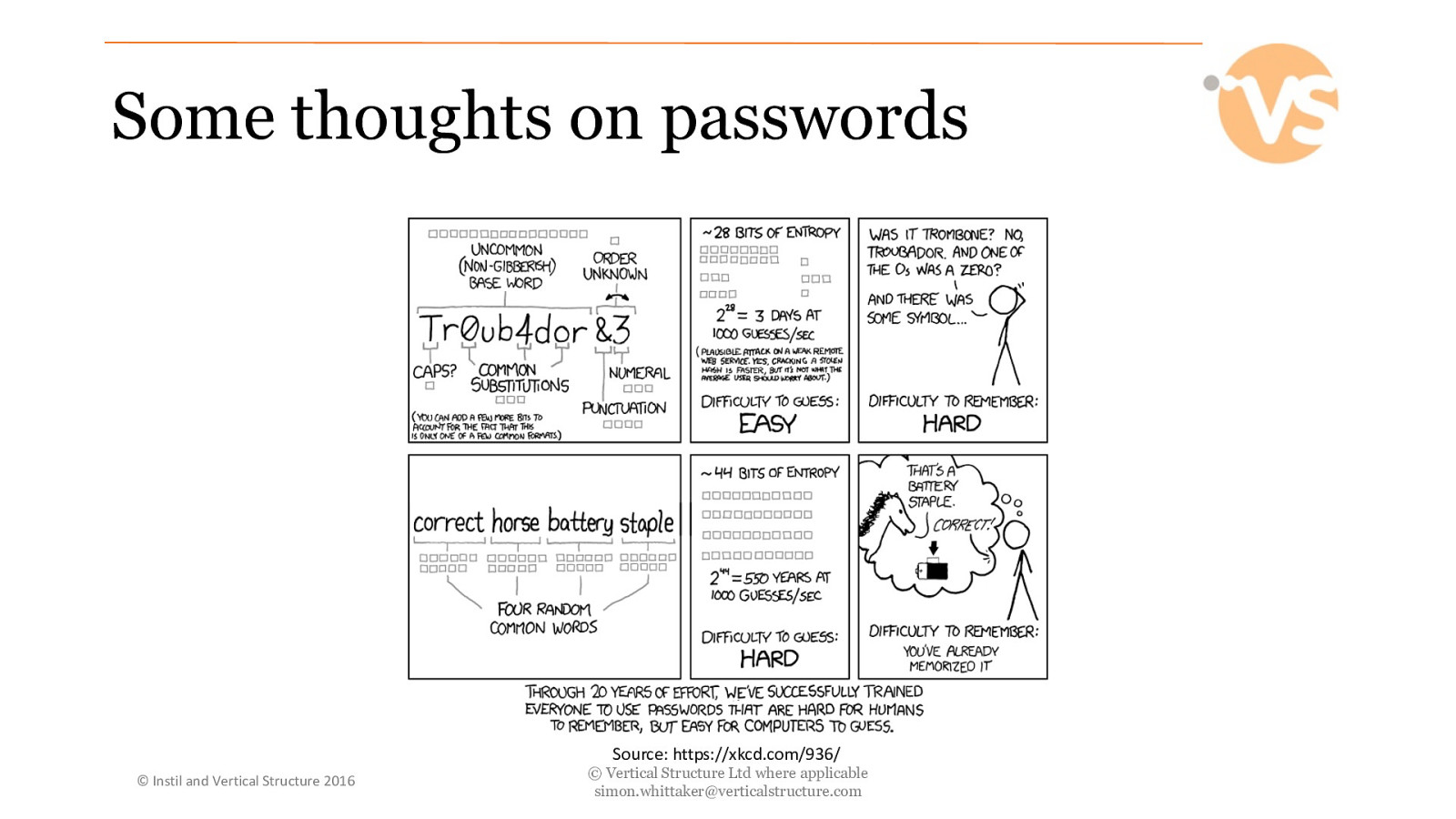
Some thoughts on passwords Source: https://xkcd.com/936/ © Instil and Vertical Structure 2016 © Vertical Structure Ltd where applicable [email protected]
Slide 50
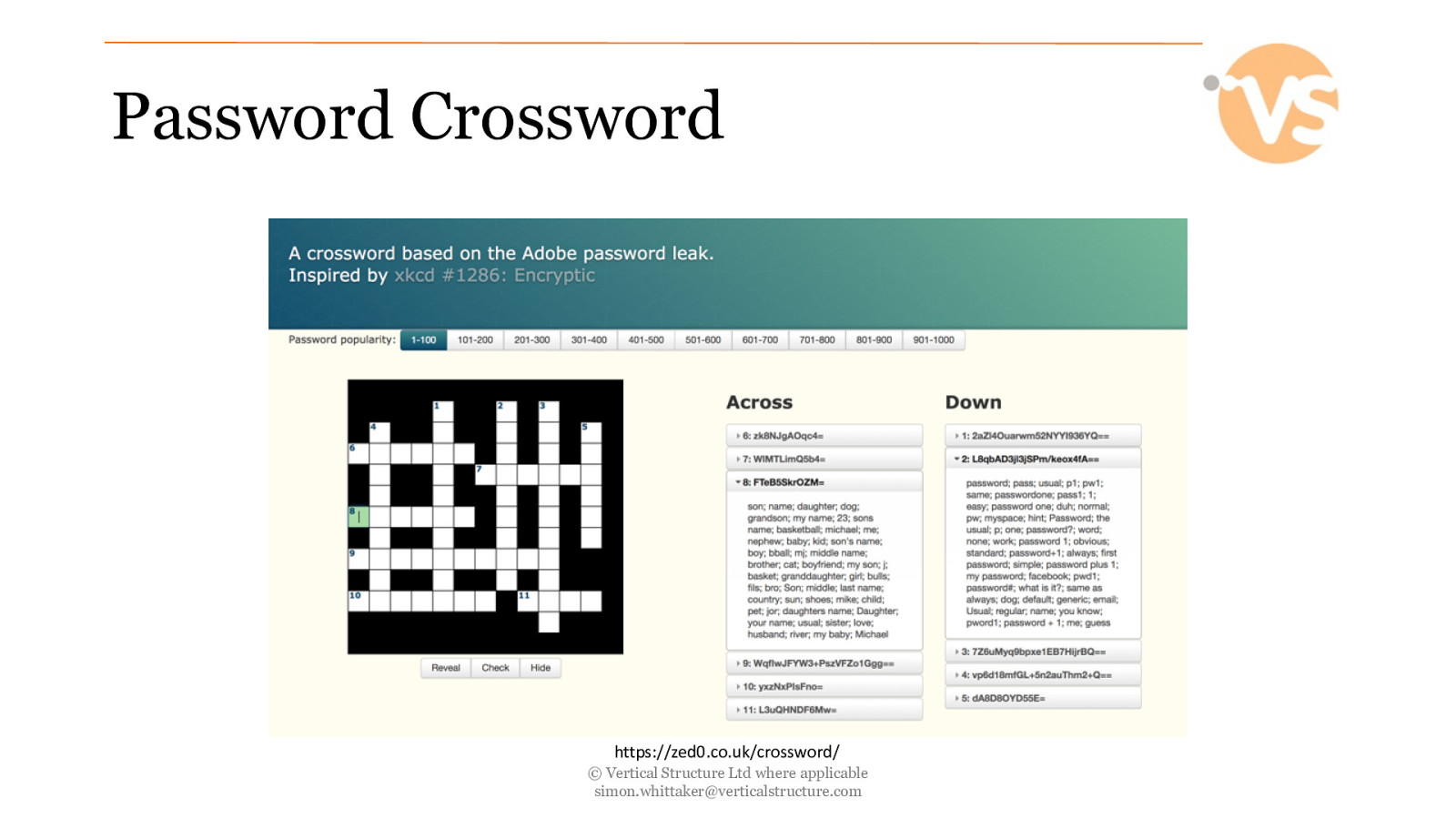
Password Crossword https://zed0.co.uk/crossword/ © Vertical Structure Ltd where applicable [email protected]
Slide 51

Password Managers © Vertical Structure Ltd where applicable [email protected]
Slide 52

Exercise - Password Responsibility • Thinking about the passwords(work and personal) that you use on a regular basis, identify where you are using the same password in multiple places. Please don’t write down or share your password in any way! • Create a list of what you think the most commonly used passwords are. © Vertical Structure Ltd where applicable [email protected]
Slide 53
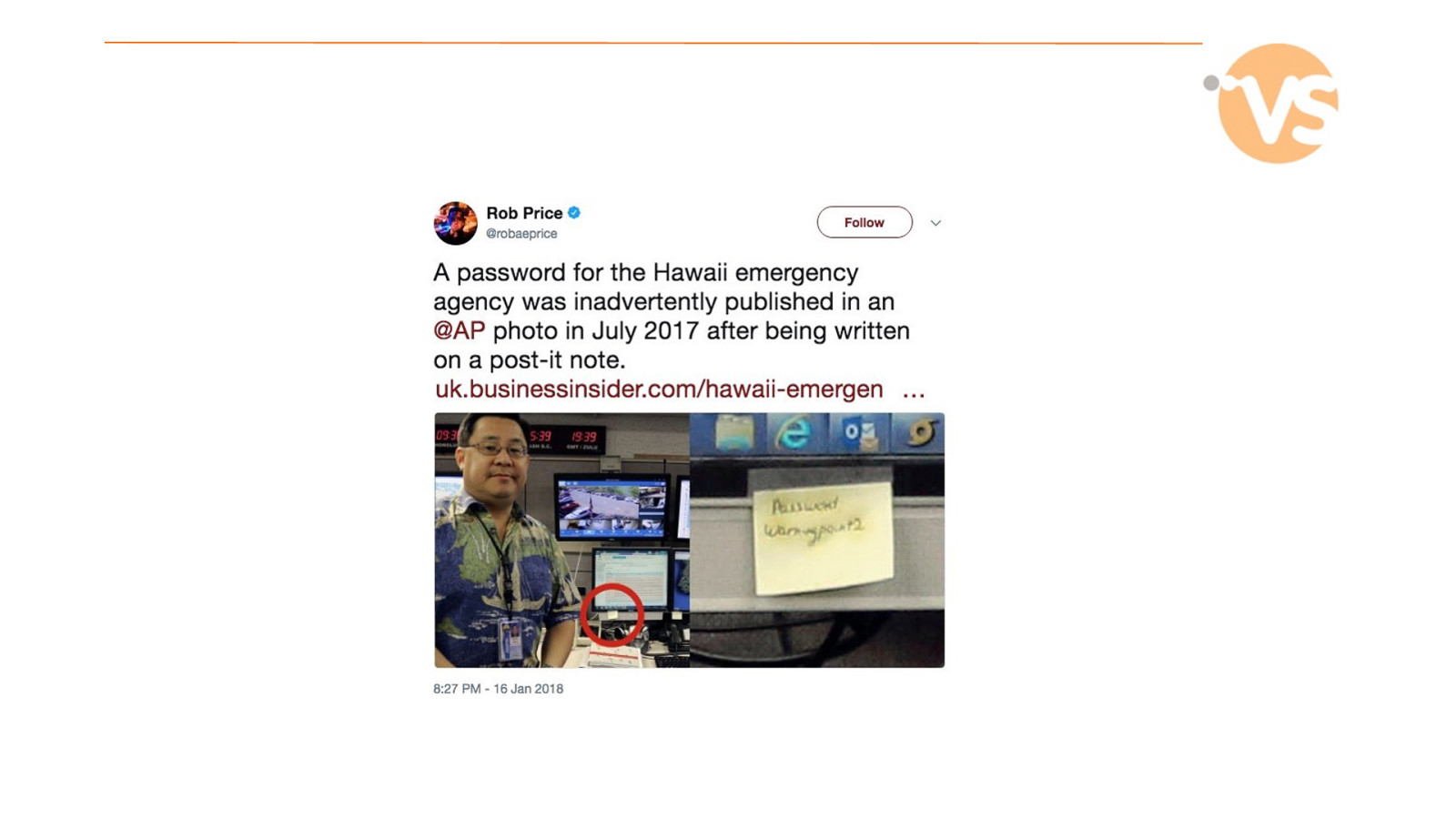
Slide 54

10 steps actions Network Security • Assess and test your exposure User Education • Teach your team how to respond Malware • Buy, use and update a reputable Anti-virus Removable Media Secure Configuration • Are USB sticks a benefit or hinderance? • Standardisation © Vertical Structure Ltd where applicable [email protected]
Slide 55

10 steps actions Managing Privilege Incident Management Monitoring Home and Mobile Working Risk Assessment • User addition and removal checklist • Teach your team how to respond • Reduce the time before compromise awareness • Effective policies and technology • Expand risks beyond “what if we get hacked” © Vertical Structure Ltd where applicable [email protected]
Slide 56

Takeaways 1. 2. 3. 4. Cyber Operations Cost • https://www.recordedfuture.com/cyber -operations-cost/ An Internet Minute 6. Taking the offensive • http://www.globalservices.bt.com/cont ent/dam/globalservices/documents/wh itepapers/taking-the-offensive.pdf • http://www.visualcapitalist.com/intern et-minute-2018 7. Effective Cyber Risk Assessments 8. NCSC small business advice • https://www.thesslstore.com/blog/cybe r-risk-assessment Data Breach List • https://www.privacyrights.org/databreaches Cyber Threat to the legal profession • https://www.ncsc.gov.uk/legalthreat • https://www.ncsc.gov.uk/smallbusiness 9. Verizon Breach Report • http://www.verizonenterprise.com/veri zon-insights-lab/dbir/2017/ 10. Vertical Structure • https://www.verticalstructure.com © Vertical Structure Ltd where applicable [email protected]
Slide 57

Questions? [email protected] vsltd.co/cyberSecurityBCCM