Beyond SQLI to ORM leaks N E X T By: Arun Krishnan and Adithya Raj
A presentation at bi0s Meetup in May 2025 in by Adithya Raj

Beyond SQLI to ORM leaks N E X T By: Arun Krishnan and Adithya Raj
Who are we? Web Security Researchers CTF players @teambi0s 3+ Years in Web Security Adithya Raj 2025 Arun Krishnan 1 N E X T
Contents Beyond SQLI Django ORM What is an ORM 2025 ORM attacks 2 Live Demo Conclusion N E X T
Beyond SQLI 2025 SQL Injection (SQLi) is a major security flaw caused by directly inserting user input into SQL queries, allowing attackers to manipulate database operations. There’s a clear need for a consistent, reusable way to handle database queries that reduces human error and enforces best practices by default. SQLI can easily be mitigated by using prepared statements under the hood. Writing secure queries manually for every user input can become repetitive and error-prone, especially as applications scale. 3 N E X T
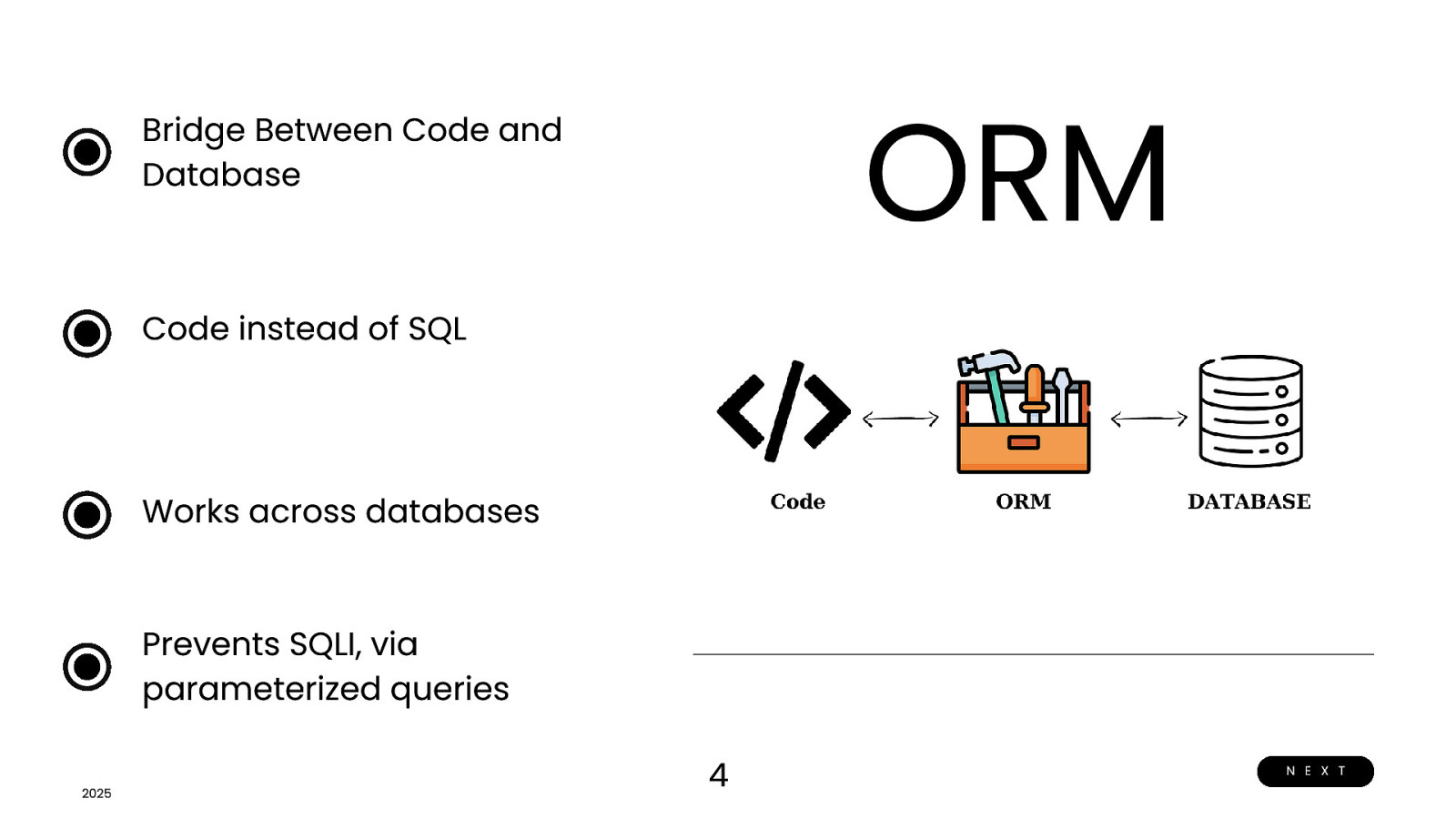
ORM Bridge Between Code and Database Code instead of SQL Works across databases Prevents SQLI, via parameterized queries 2025 2025 4 N E X T
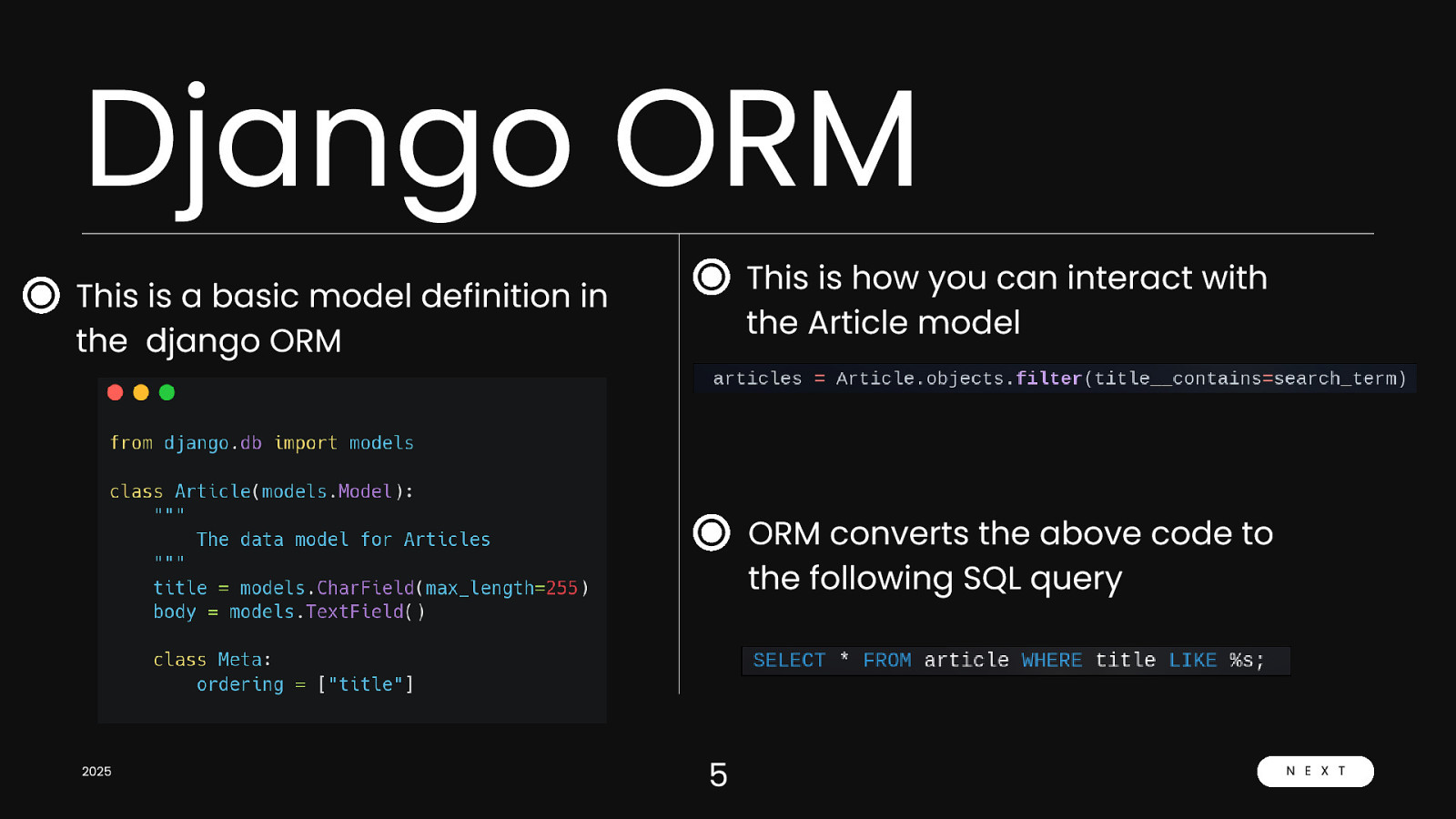
Django ORM This is how you can interact with the Article model This is a basic model definition in the django ORM ORM converts the above code to the following SQL query 2025 5 N E X T
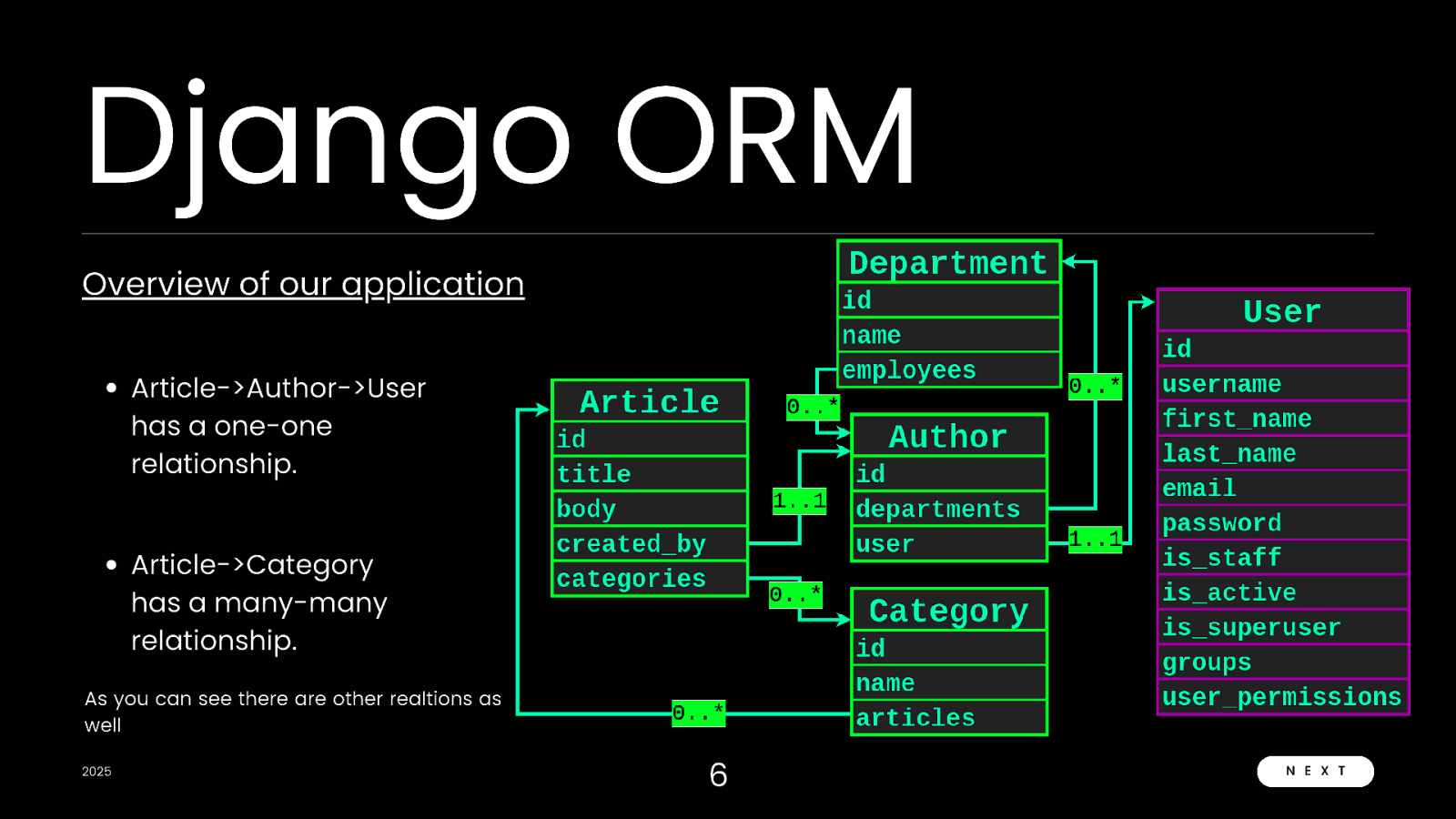
Django ORM Overview of our application Article->Author->User has a one-one relationship. Article->Category has a many-many relationship. As you can see there are other realtions as well 2025 6 N E X T
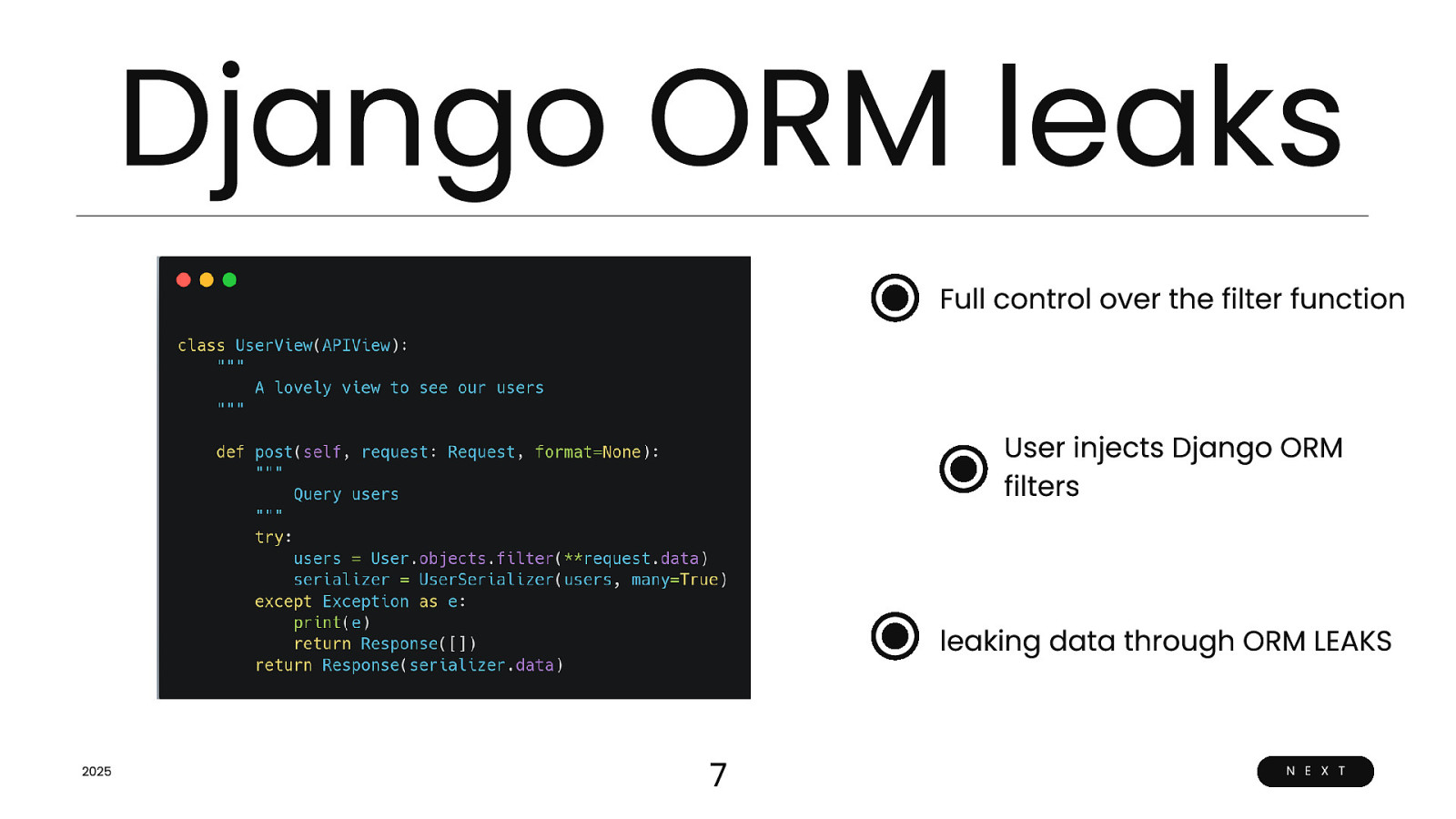
Django ORM leaks Full control over the filter function User injects Django ORM filters leaking data through ORM LEAKS 2025 7 N E X T
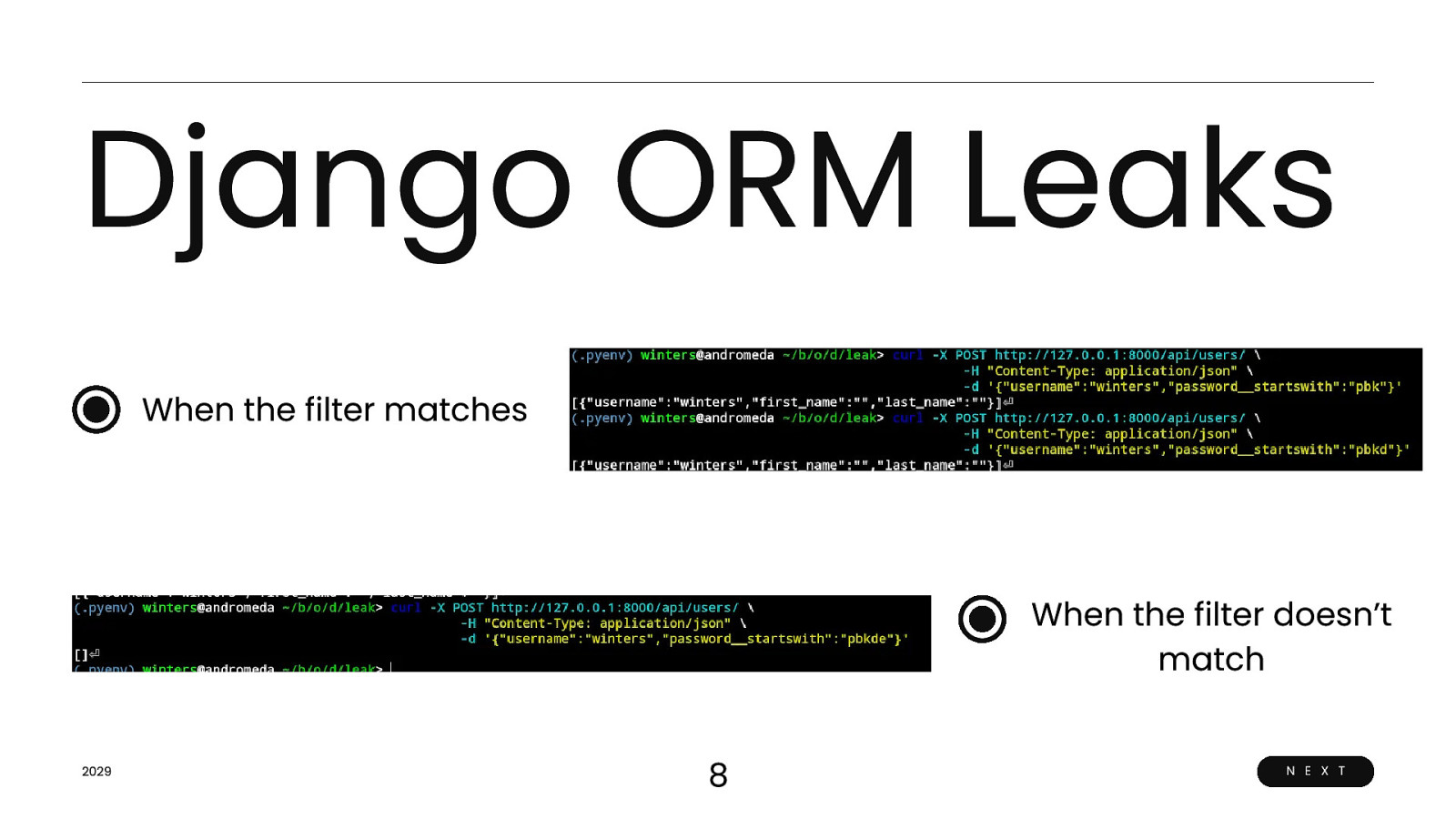
Django ORM Leaks When the filter matches When the filter doesn’t match 2029 8 N E X T
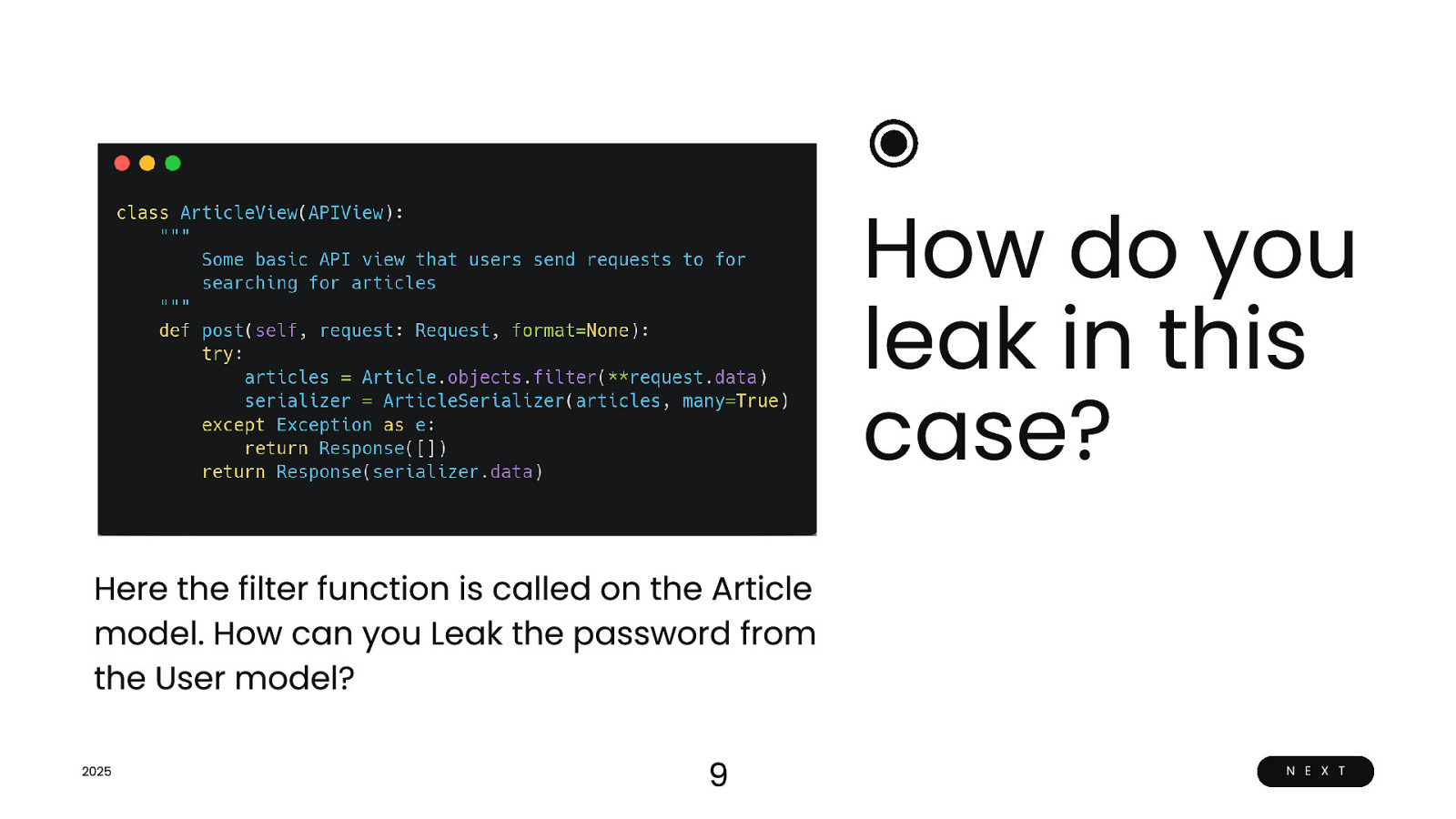
How do you leak in this case? Here the filter function is called on the Article model. How can you Leak the password from the User model? 2025 9 N E X T
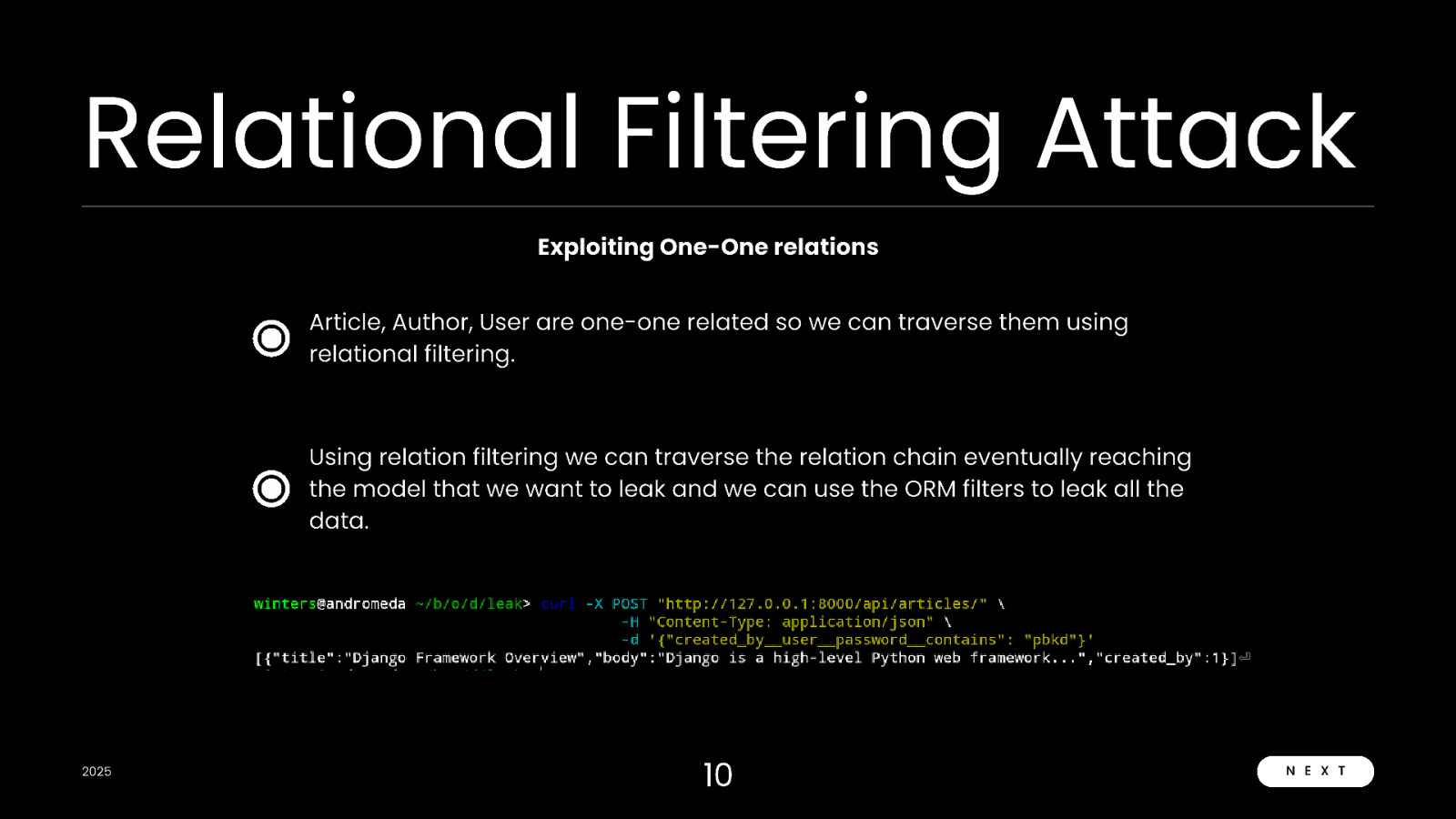
Relational Filtering Attack Exploiting One-One relations Article, Author, User are one-one related so we can traverse them using relational filtering. Using relation filtering we can traverse the relation chain eventually reaching the model that we want to leak and we can use the ORM filters to leak all the data. 2025 10 N E X T
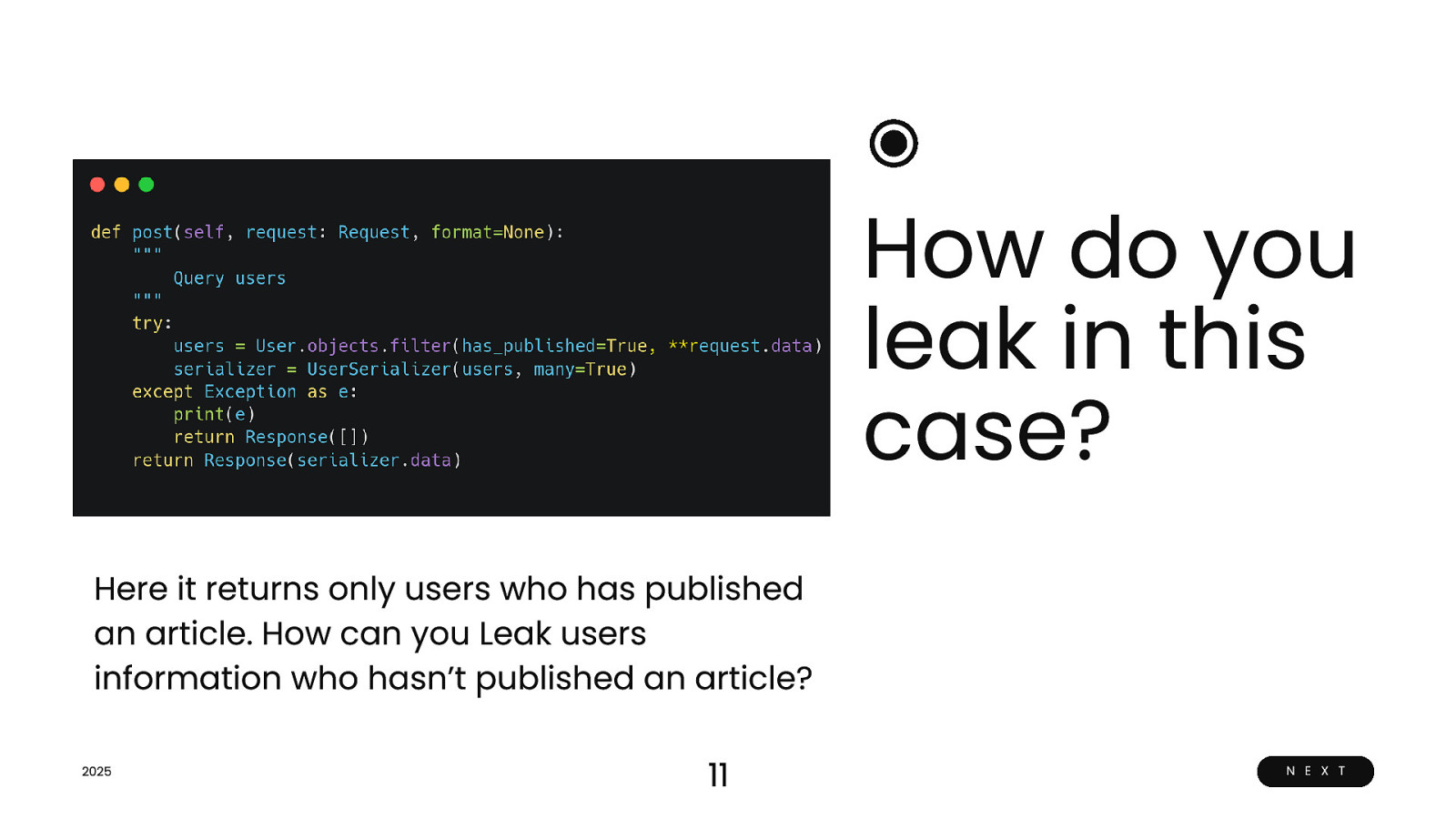
How do you leak in this case? Here it returns only users who has published an article. How can you Leak users information who hasn’t published an article? 2025 11 N E X T
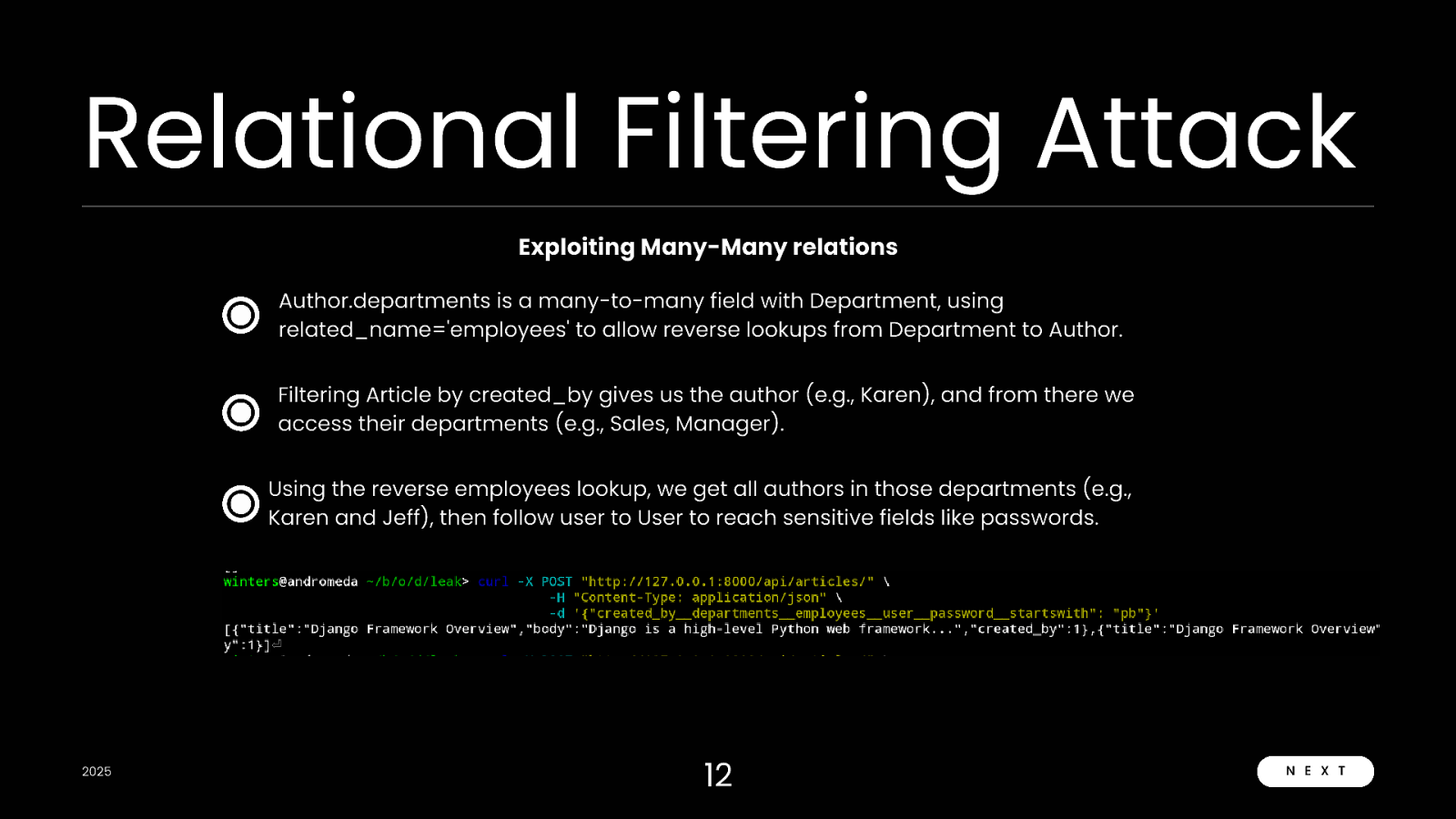
Relational Filtering Attack Exploiting Many-Many relations Author.departments is a many-to-many field with Department, using related_name=’employees’ to allow reverse lookups from Department to Author. Filtering Article by created_by gives us the author (e.g., Karen), and from there we access their departments (e.g., Sales, Manager). Using the reverse employees lookup, we get all authors in those departments (e.g., Karen and Jeff), then follow user to User to reach sensitive fields like passwords. 2025 12 N E X T
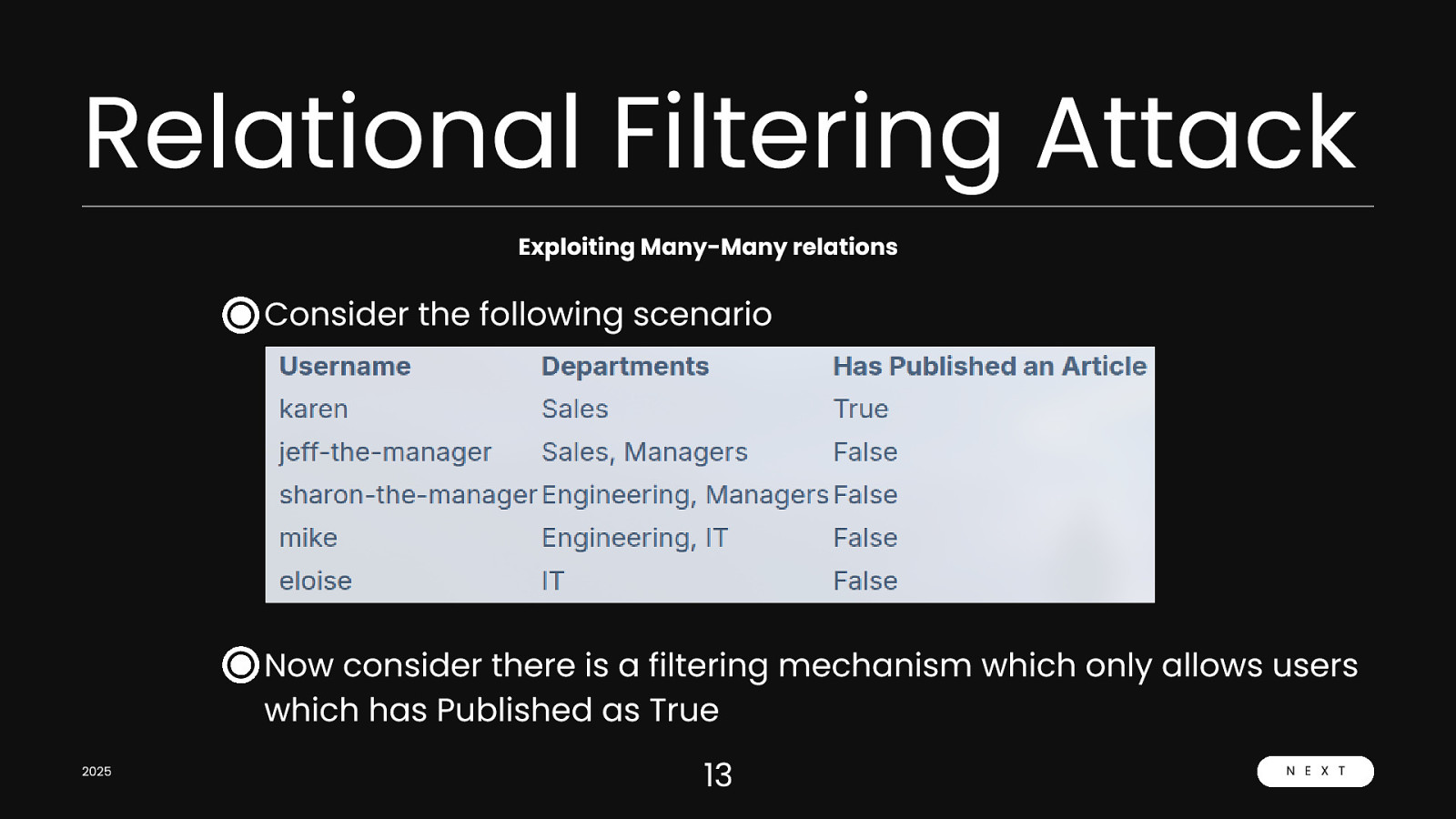
Relational Filtering Attack Exploiting Many-Many relations Consider the following scenario Now consider there is a filtering mechanism which only allows users which has Published as True 2025 13 N E X T
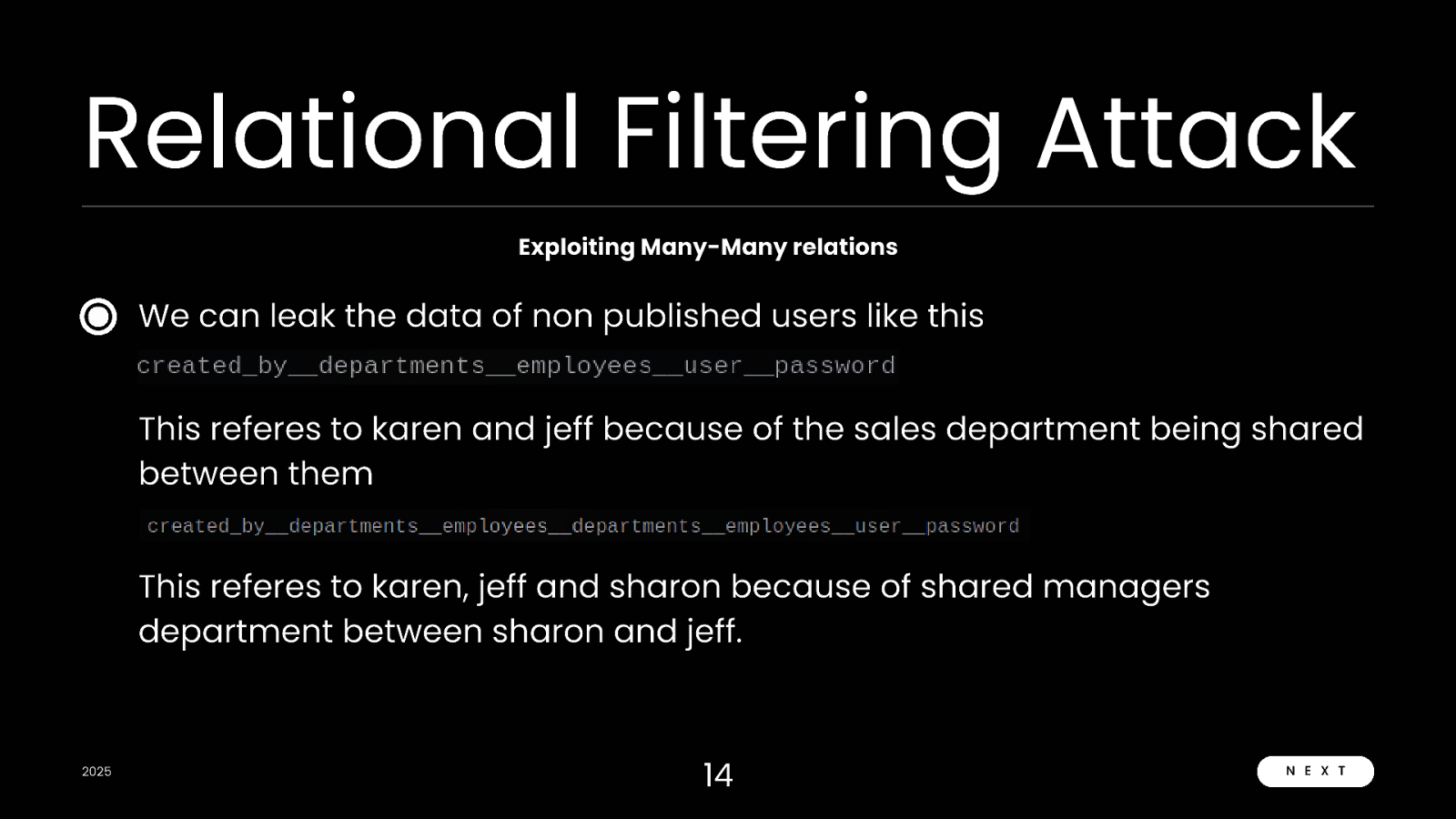
Relational Filtering Attack Exploiting Many-Many relations We can leak the data of non published users like this This referes to karen and jeff because of the sales department being shared between them This referes to karen, jeff and sharon because of shared managers department between sharon and jeff. 2025 14 N E X T
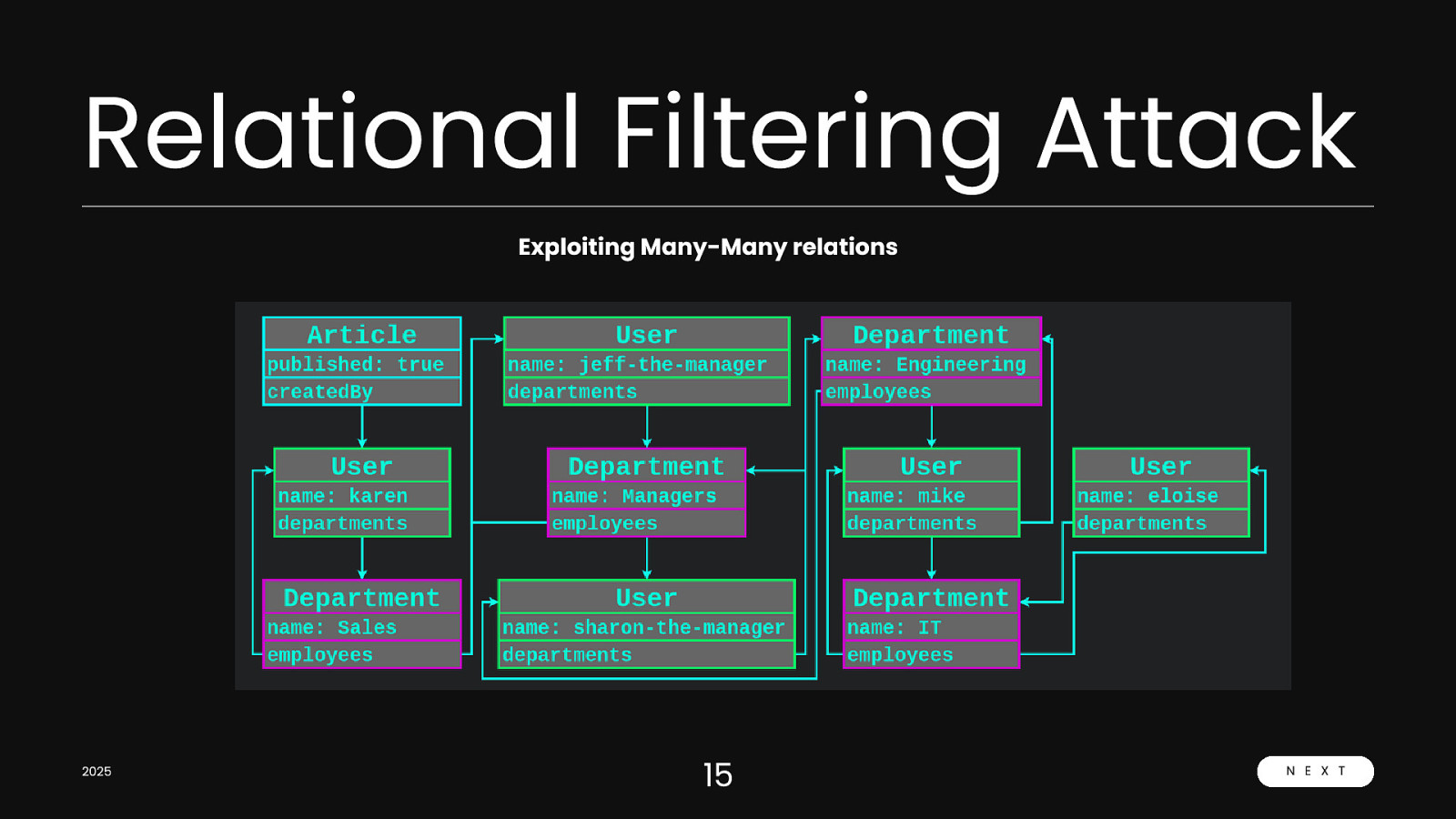
Relational Filtering Attack Exploiting Many-Many relations 2025 15 N E X T

Relational Filtering Attack Exploiting Many-Many relations We can continue the chain to cover all the users in the model. Hence we can loop over all the users because of the shared departments between each of them and leak all the data we want 2025 16 N E X T
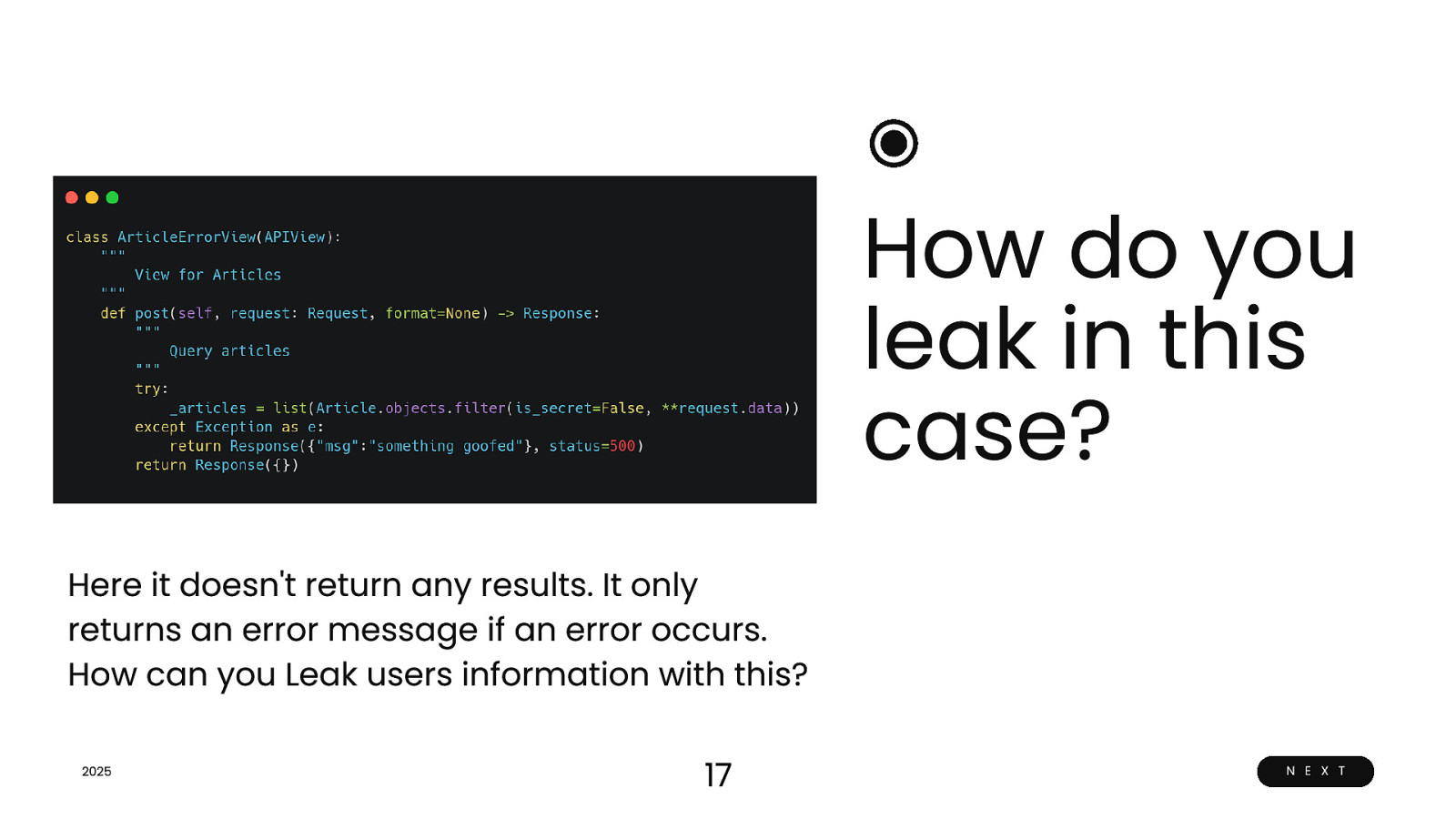
How do you leak in this case? Here it doesn’t return any results. It only returns an error message if an error occurs. How can you Leak users information with this? 2025 17 N E X T
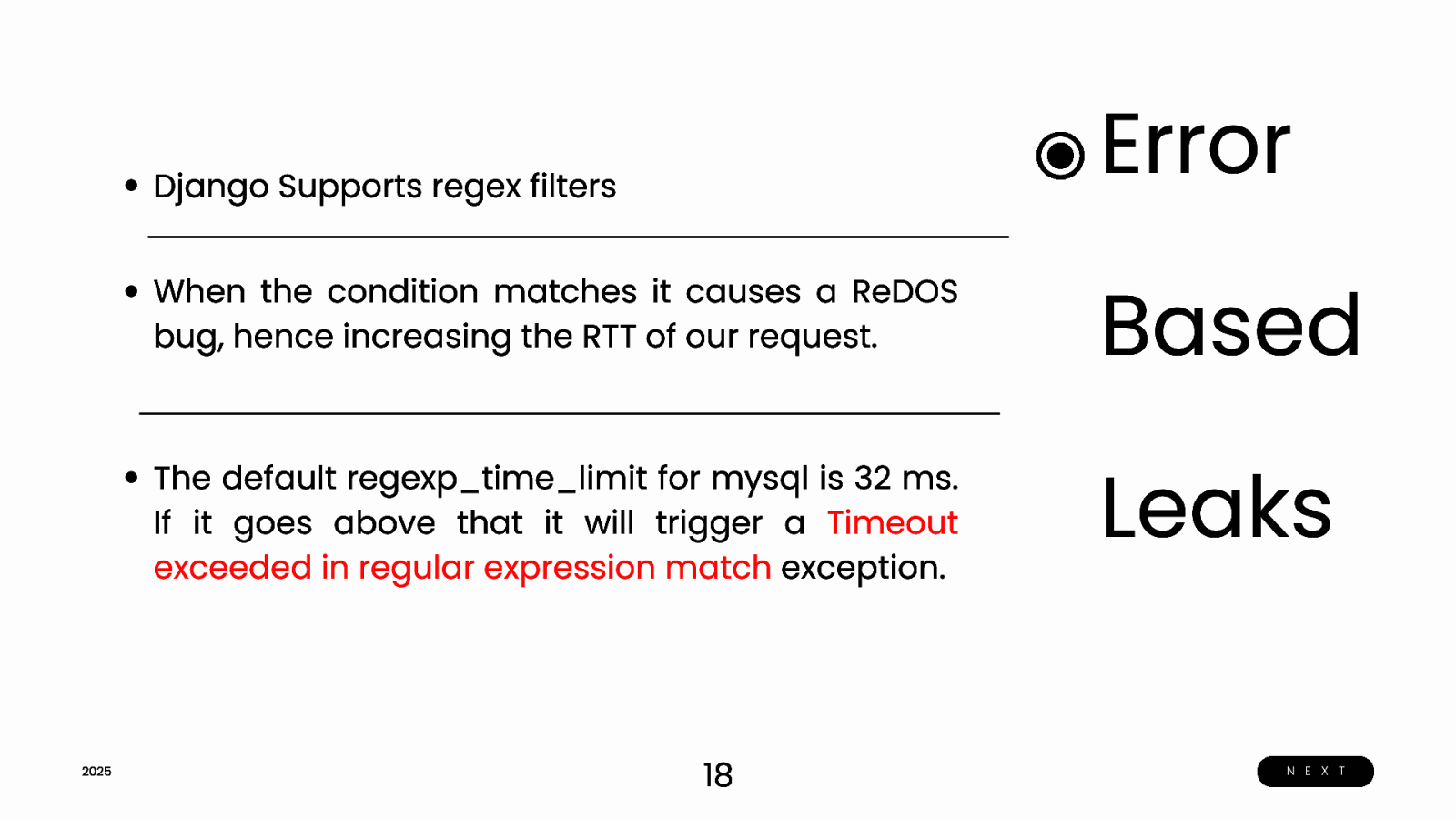
Error Django Supports regex filters 2025 When the condition matches it causes a ReDOS bug, hence increasing the RTT of our request. Based The default regexp_time_limit for mysql is 32 ms. If it goes above that it will trigger a Timeout exceeded in regular expression match exception. Leaks 18 N E X T
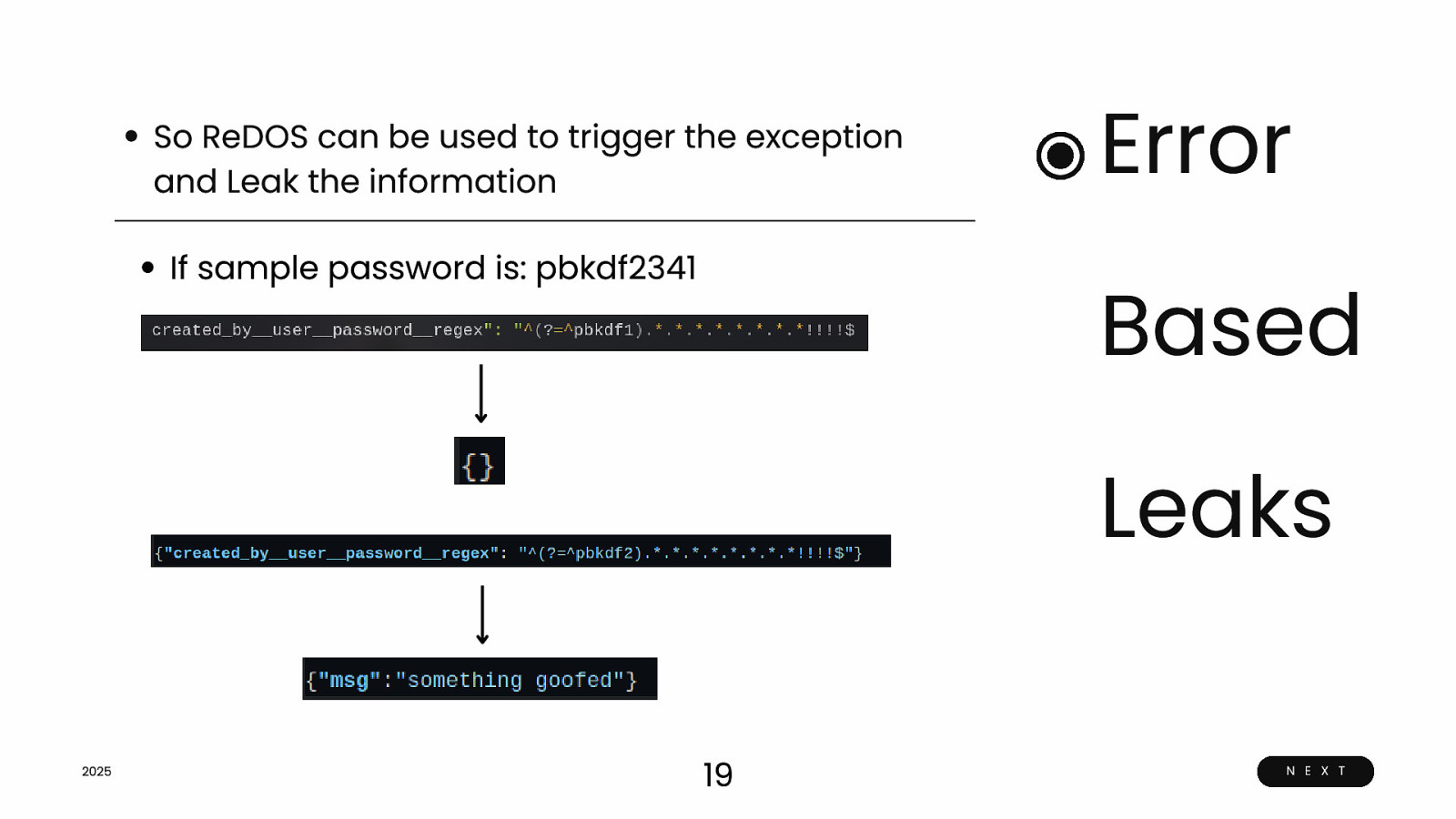
So ReDOS can be used to trigger the exception and Leak the information If sample password is: pbkdf2341 Error Based Leaks 2025 19 N E X T
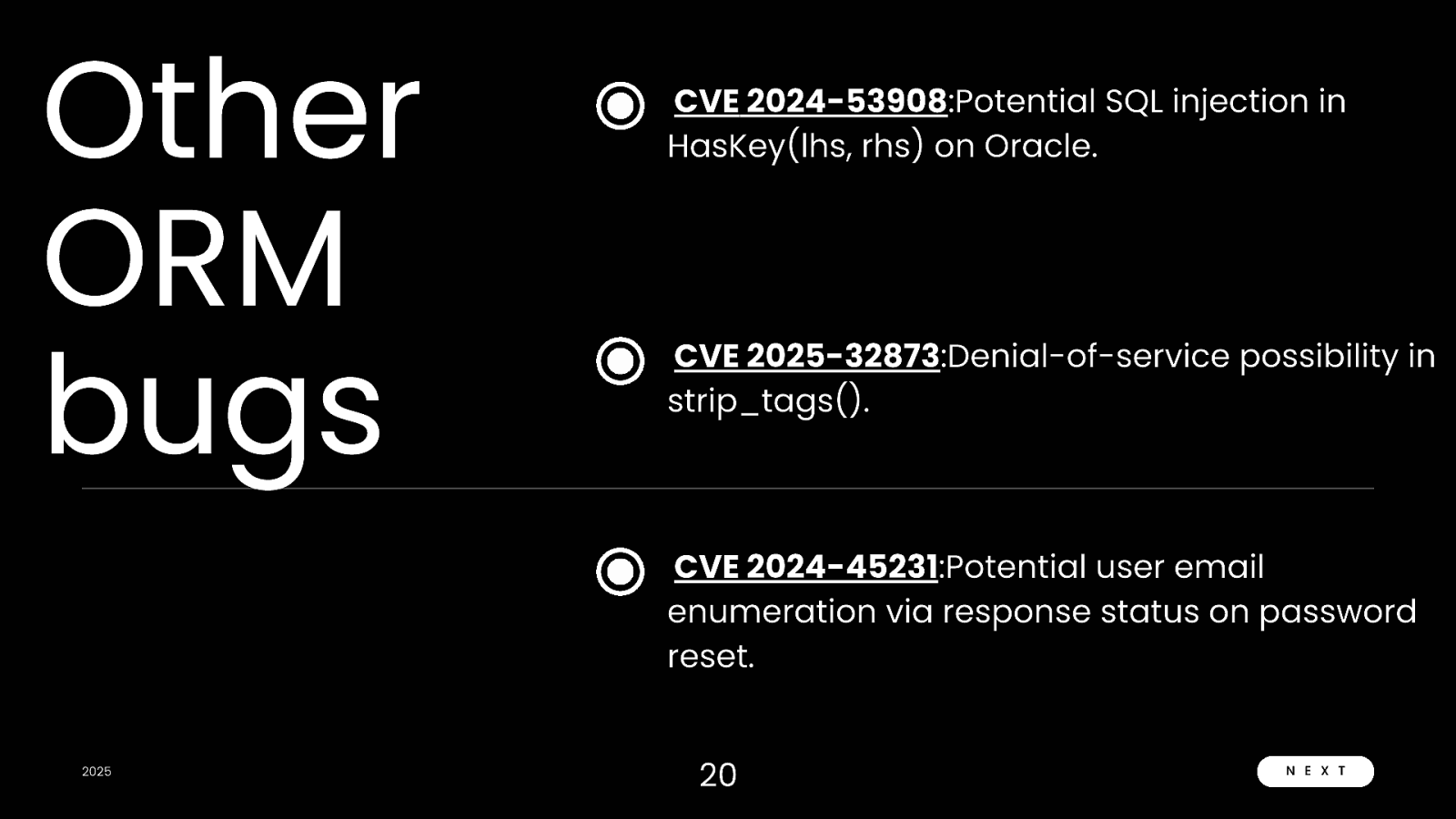
Other ORM bugs CVE 2024-53908:Potential SQL injection in HasKey(lhs, rhs) on Oracle. CVE 2025-32873:Denial-of-service possibility in strip_tags(). CVE 2024-45231:Potential user email enumeration via response status on password reset. 2025 20 N E X T

DIVE LEMO 2025 21 N E X T
References O Django ORM Research by elttam 2025 R M Time based attacks on Prisma ORM by elttam 22 Preventing SQL Injection in Django by Jacobian N E X T
Get in Touch For more information, please reach out to us at Adithya Raj Arun Krishnan Email: adithyaraj2515@gmail.com Twitter: x.com/Adithyaraj2515 Linkedin: www.linkedin.com/in/luc1f3r Email: arun.krishnan.w@gmail.com Twitter: x.com/ArunKr1shnan Website: https://winters0x64.xyz We look forward to hearing from you!