How Threat Modeling Made Me Better at Online Dating #DateSafe Isaiah Sarju @isaiahsarju
A presentation at OWASP Appsec Tel Aviv 2019 in November 2019 in Tel Aviv-Yafo, Israel by Isaiah Sarju

How Threat Modeling Made Me Better at Online Dating #DateSafe Isaiah Sarju @isaiahsarju
Who am I • Security consultant, coowner Revis Solutions • Red teamer • Teacher • Anti: nihilism, security theater, wasted time • Pro: risk based security • Love chocolate chip cookies @isaiahsarju
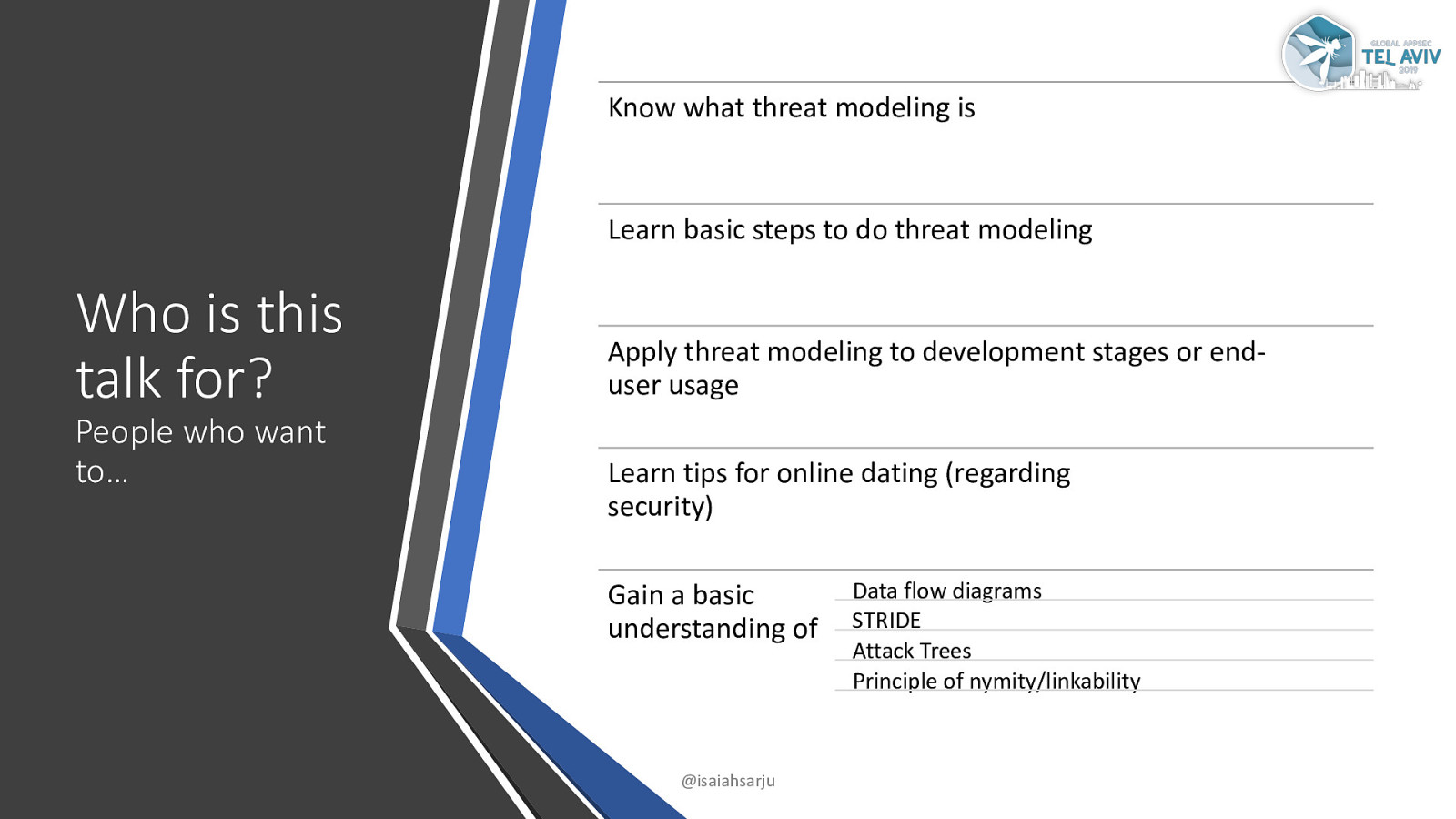
Know what threat modeling is Learn basic steps to do threat modeling Who is this talk for? People who want to… Apply threat modeling to development stages or enduser usage Learn tips for online dating (regarding security) Gain a basic understanding of @isaiahsarju Data flow diagrams STRIDE Attack Trees Principle of nymity/linkability

Technology and Dating
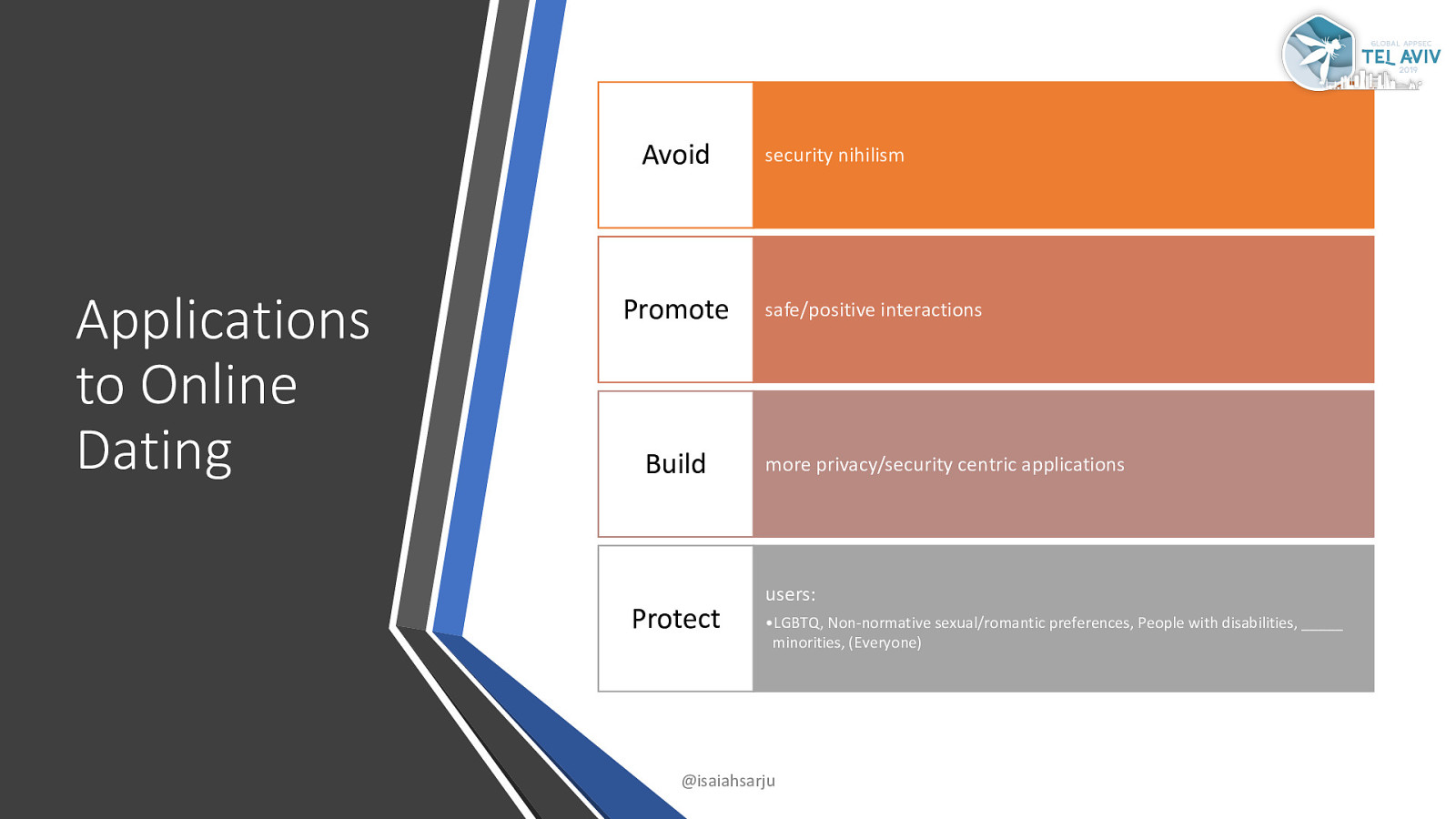
Avoid Applications to Online Dating Promote Build Protect security nihilism safe/positive interactions more privacy/security centric applications users: •LGBTQ, Non-normative sexual/romantic preferences, People with disabilities, _____ minorities, (Everyone) @isaiahsarju

There are many Consequences of Bad Threat Modeling Tinder Matching Disclosure Data Linking Disclosure @isaiahsarju
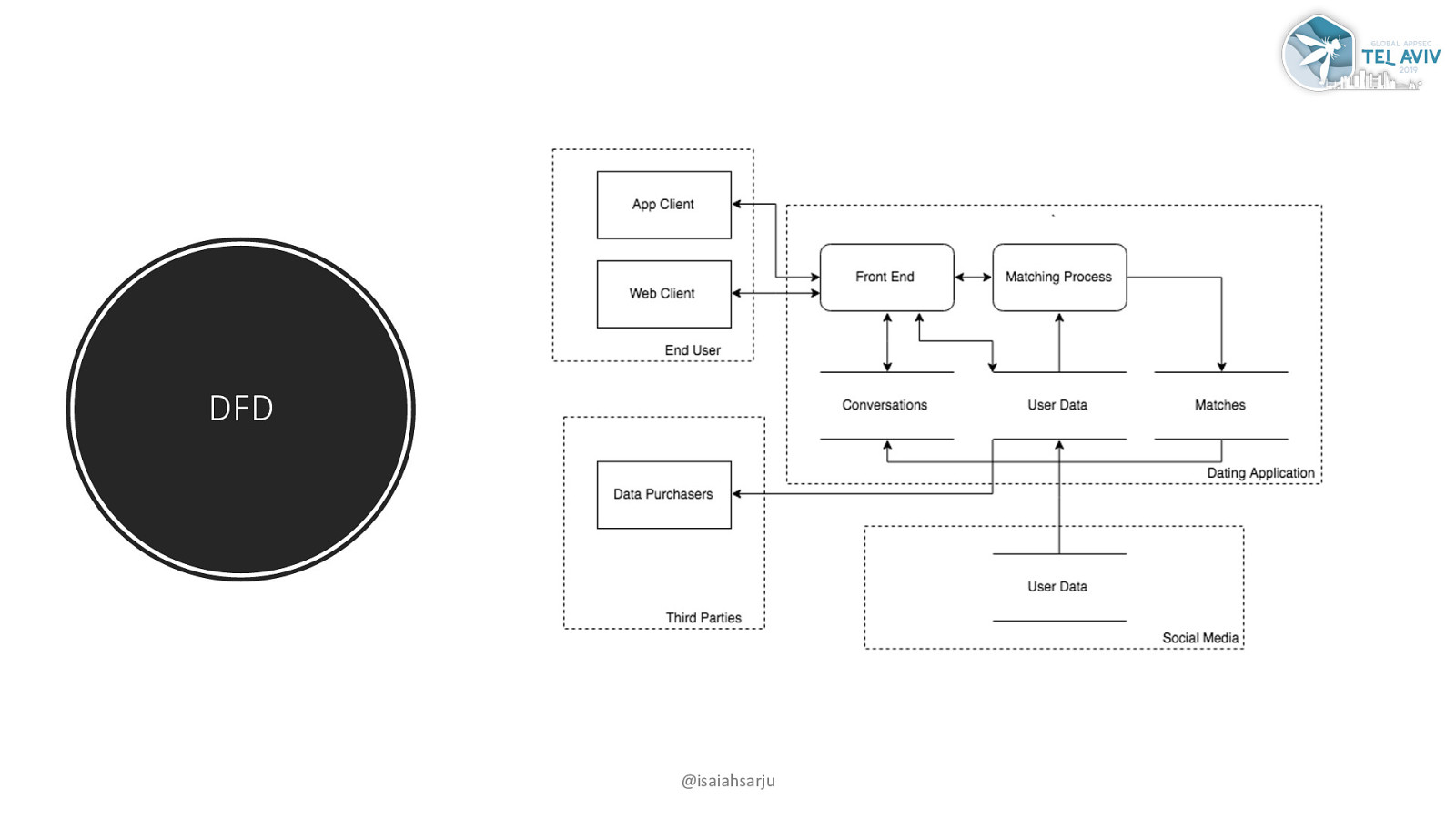
DFD @isaiahsarju
Decompose application processes Data flow diagrams Understand data flow “Problems tend to follow the data flow, not the control flow” – Adam Shostack Apply STRIDE to each step of the way @isaiahsarju
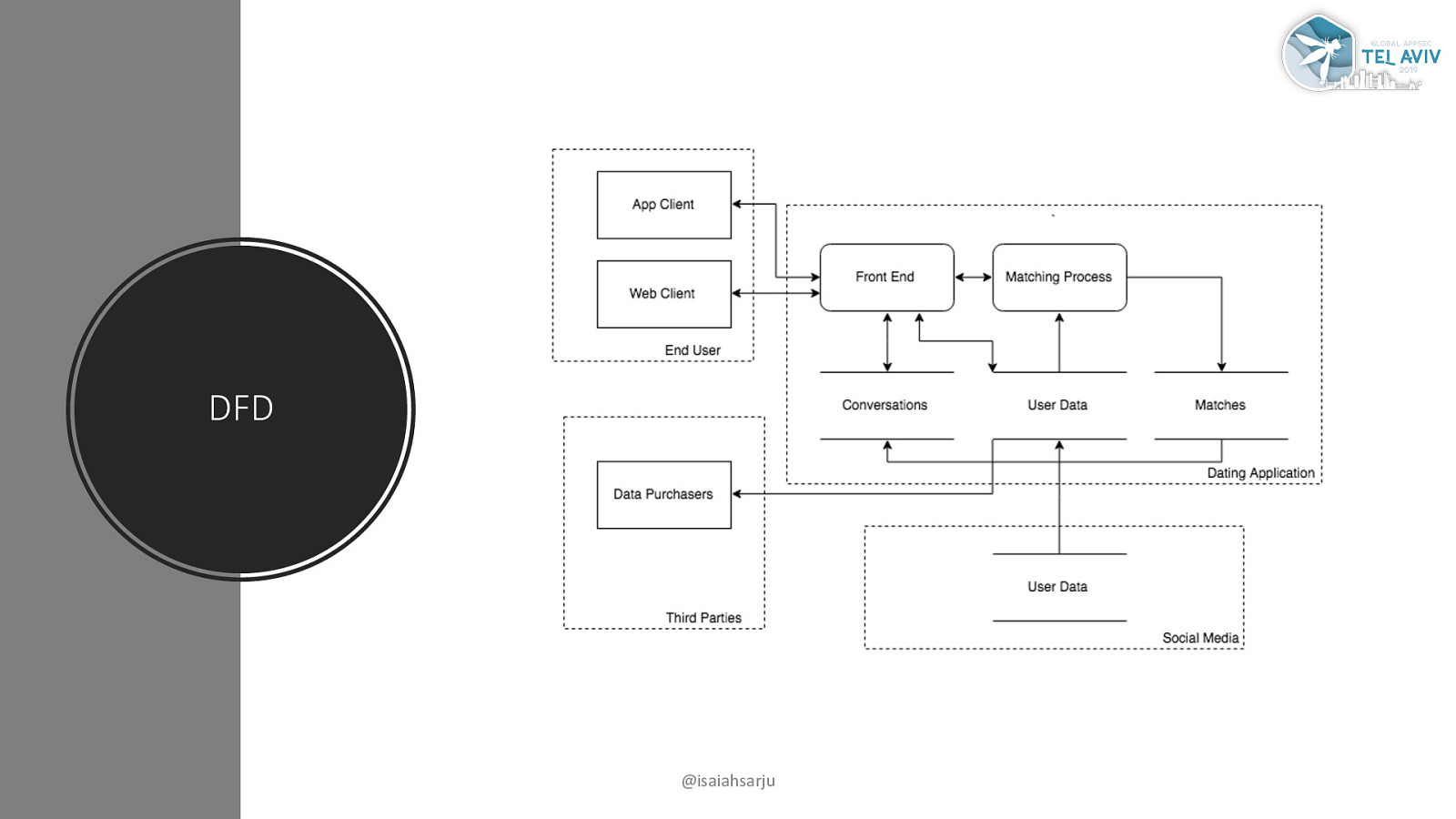
DFD @isaiahsarju
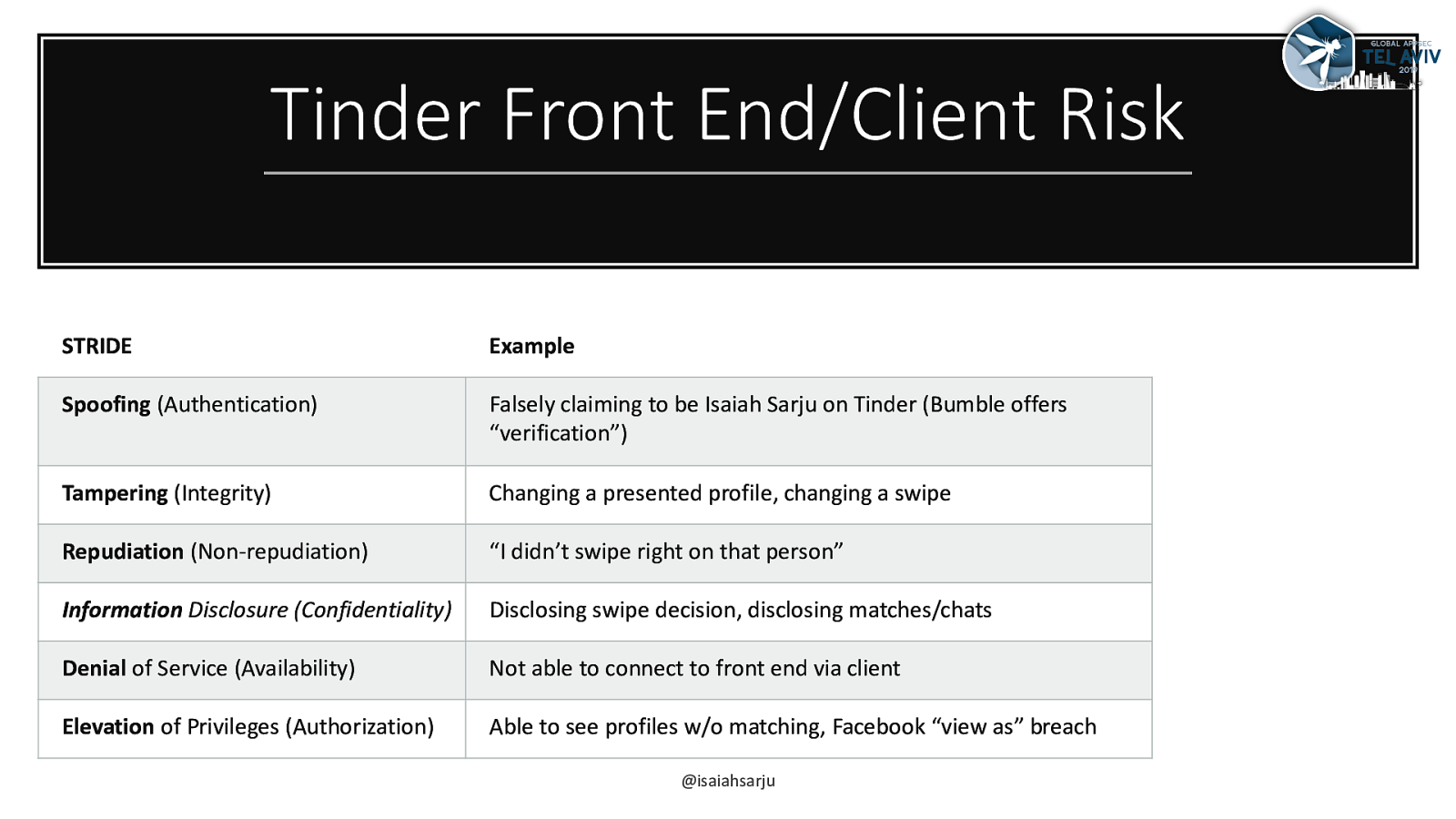
Tinder Front End/Client Risk STRIDE Example Spoofing (Authentication) Falsely claiming to be Isaiah Sarju on Tinder (Bumble offers “verification”) Tampering (Integrity) Changing a presented profile, changing a swipe Repudiation (Non-repudiation) “I didn’t swipe right on that person” Information Disclosure (Confidentiality) Disclosing swipe decision, disclosing matches/chats Denial of Service (Availability) Not able to connect to front end via client Elevation of Privileges (Authorization) Able to see profiles w/o matching, Facebook “view as” breach @isaiahsarju
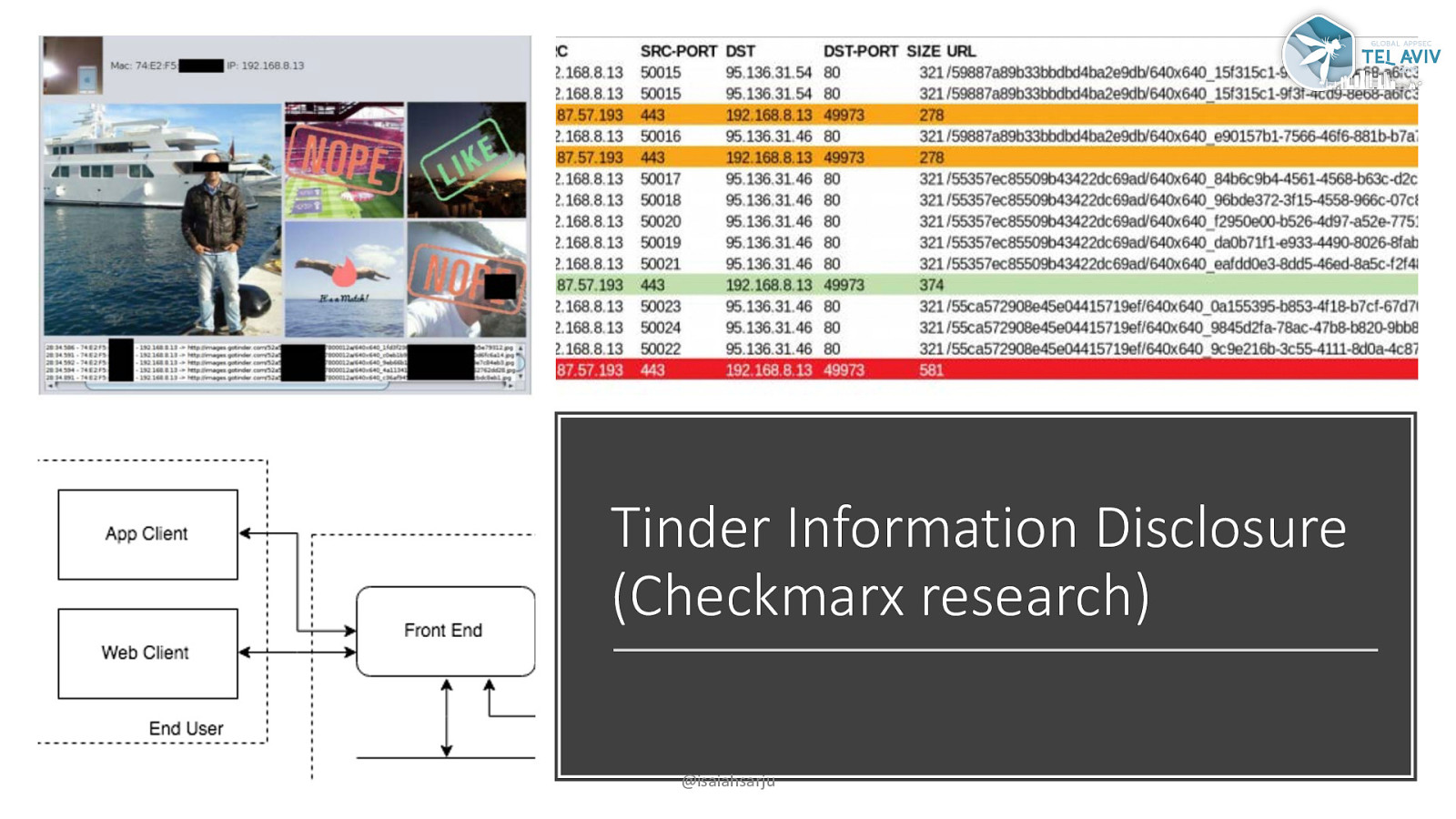
Tinder Information Disclosure (Checkmarx research) @isaiahsarju

Acceptance Avoidance Risk Management Techniques Transference Mitigation/Reduction @isaiahsarju
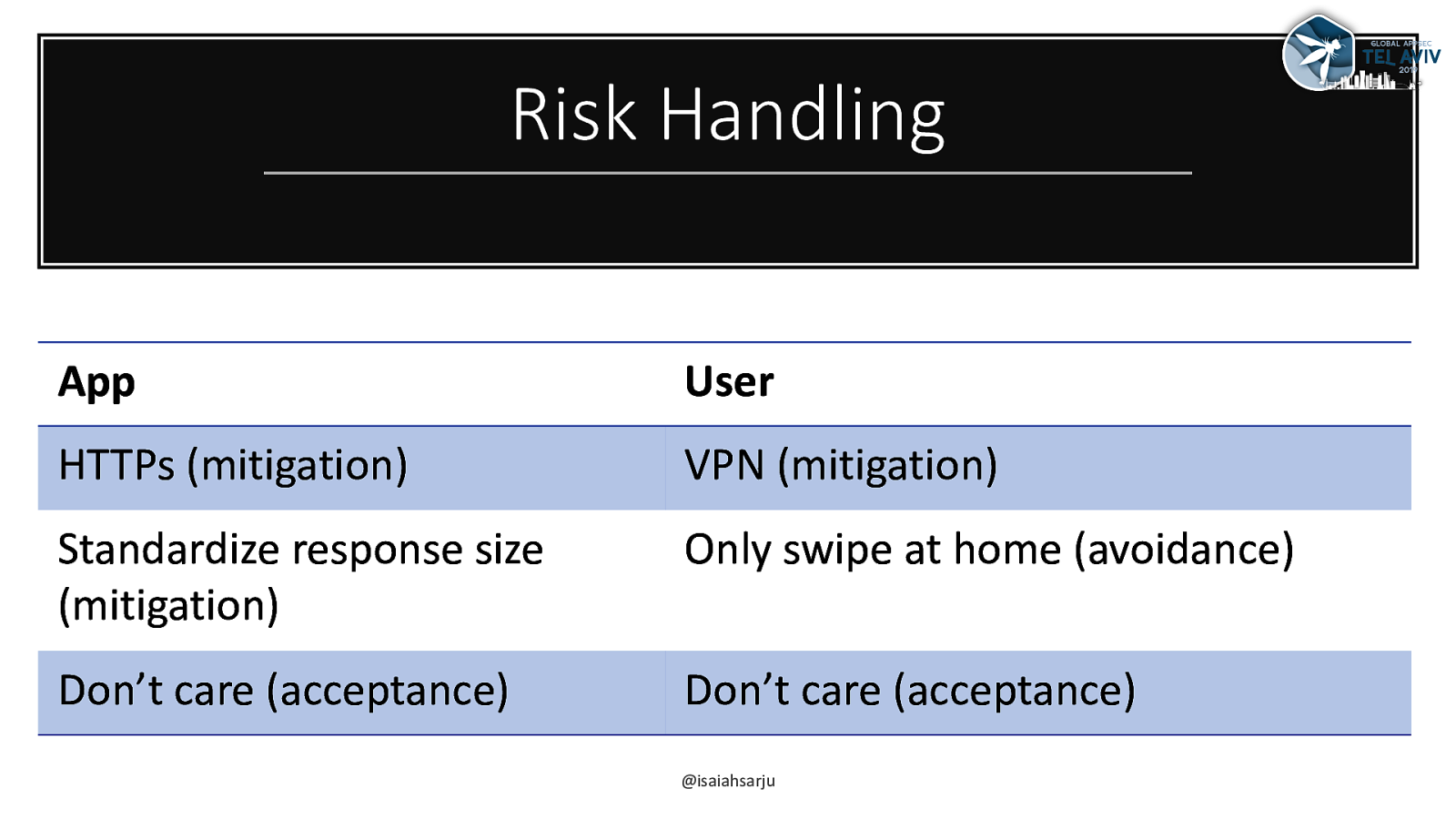
Risk Handling App User HTTPs (mitigation) VPN (mitigation) Standardize response size (mitigation) Only swipe at home (avoidance) Don’t care (acceptance) Don’t care (acceptance) @isaiahsarju
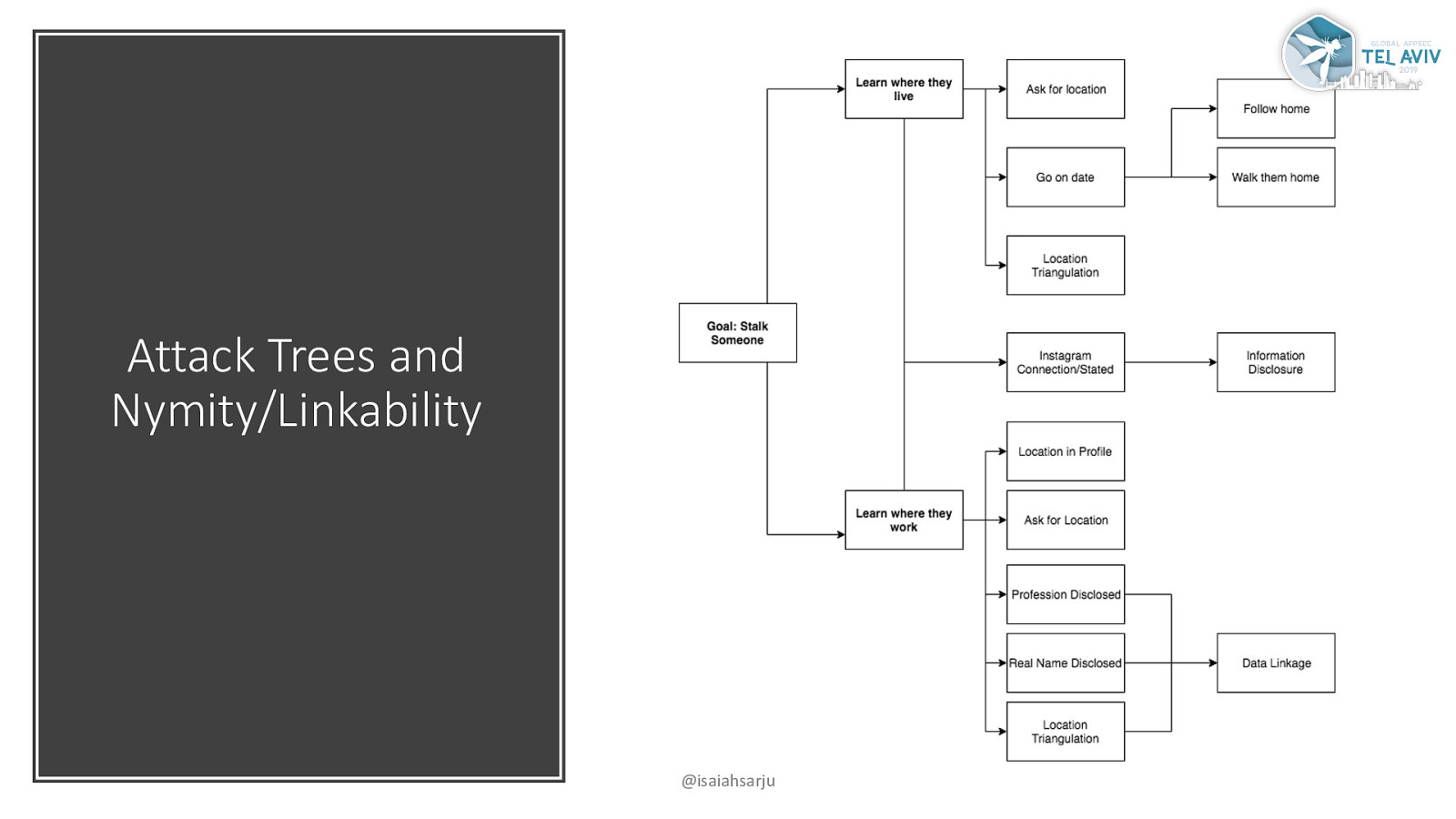
Attack Trees and Nymity/Linkability @isaiahsarju
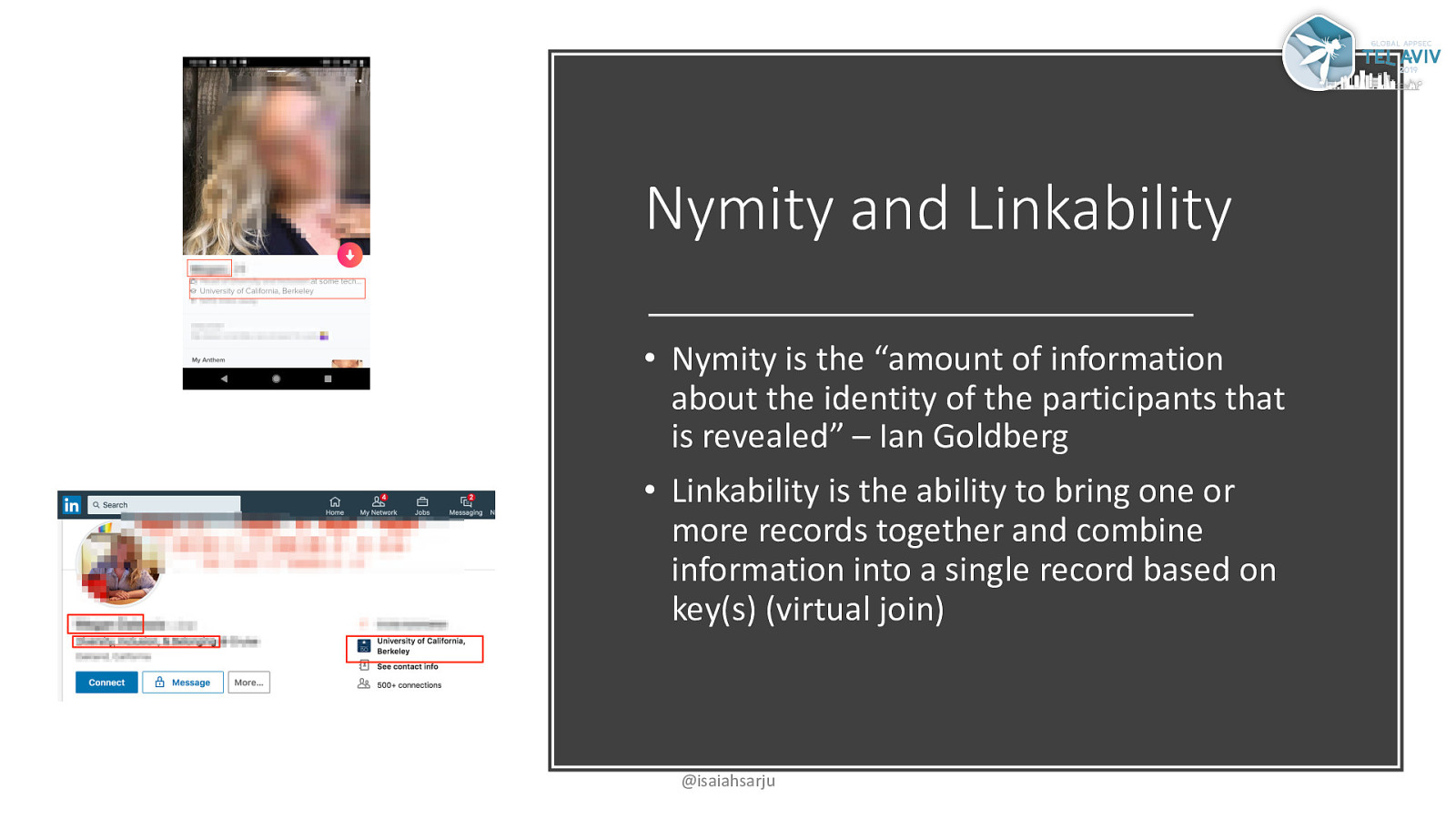
Nymity and Linkability • Nymity is the “amount of information about the identity of the participants that is revealed” – Ian Goldberg • Linkability is the ability to bring one or more records together and combine information into a single record based on key(s) (virtual join) @isaiahsarju
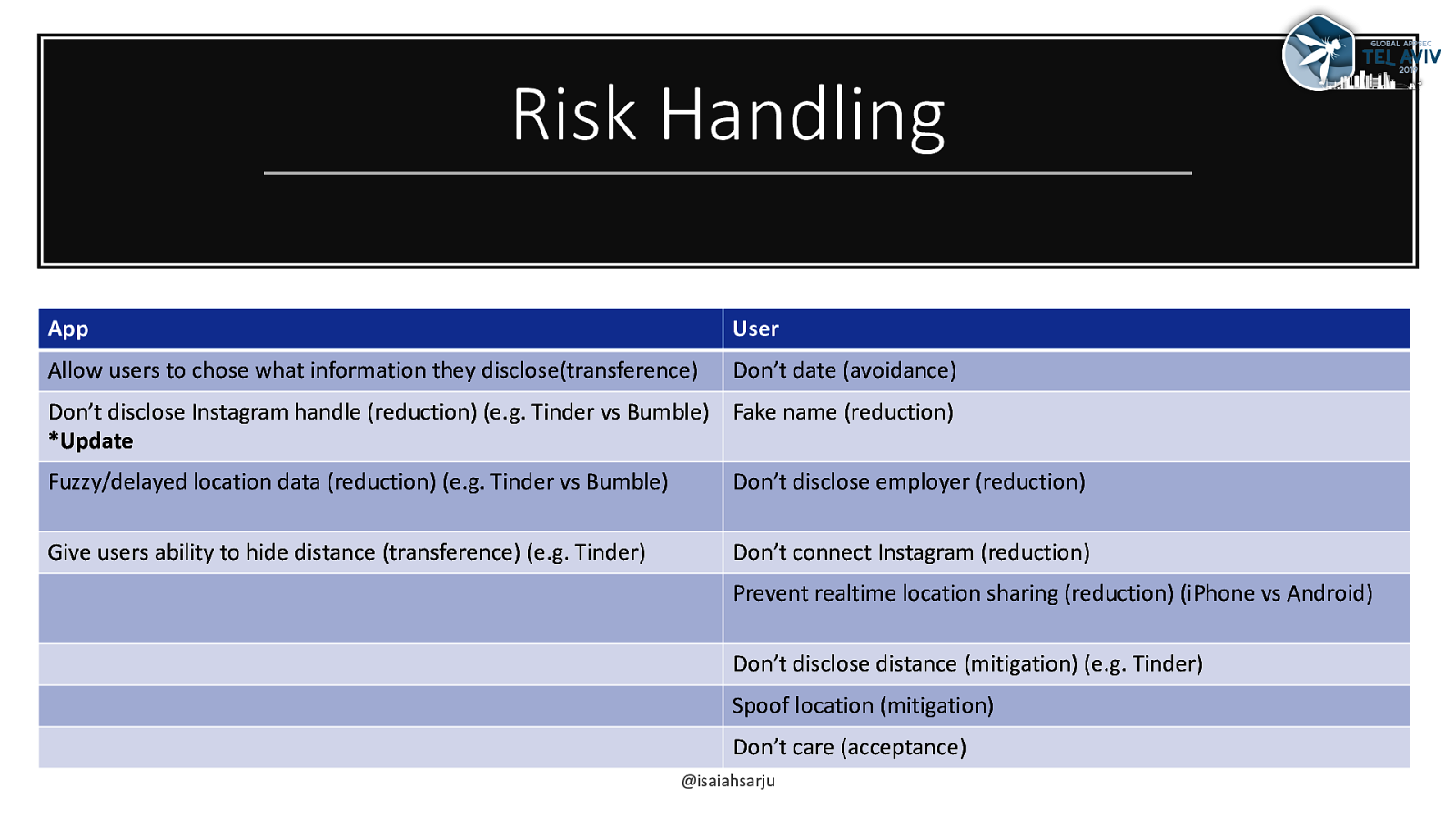
Risk Handling App User Allow users to chose what information they disclose(transference) Don’t date (avoidance) Don’t disclose Instagram handle (reduction) (e.g. Tinder vs Bumble) Fake name (reduction) *Update Fuzzy/delayed location data (reduction) (e.g. Tinder vs Bumble) Don’t disclose employer (reduction) Give users ability to hide distance (transference) (e.g. Tinder) Don’t connect Instagram (reduction) Prevent realtime location sharing (reduction) (iPhone vs Android) Don’t disclose distance (mitigation) (e.g. Tinder) Spoof location (mitigation) Don’t care (acceptance) @isaiahsarju
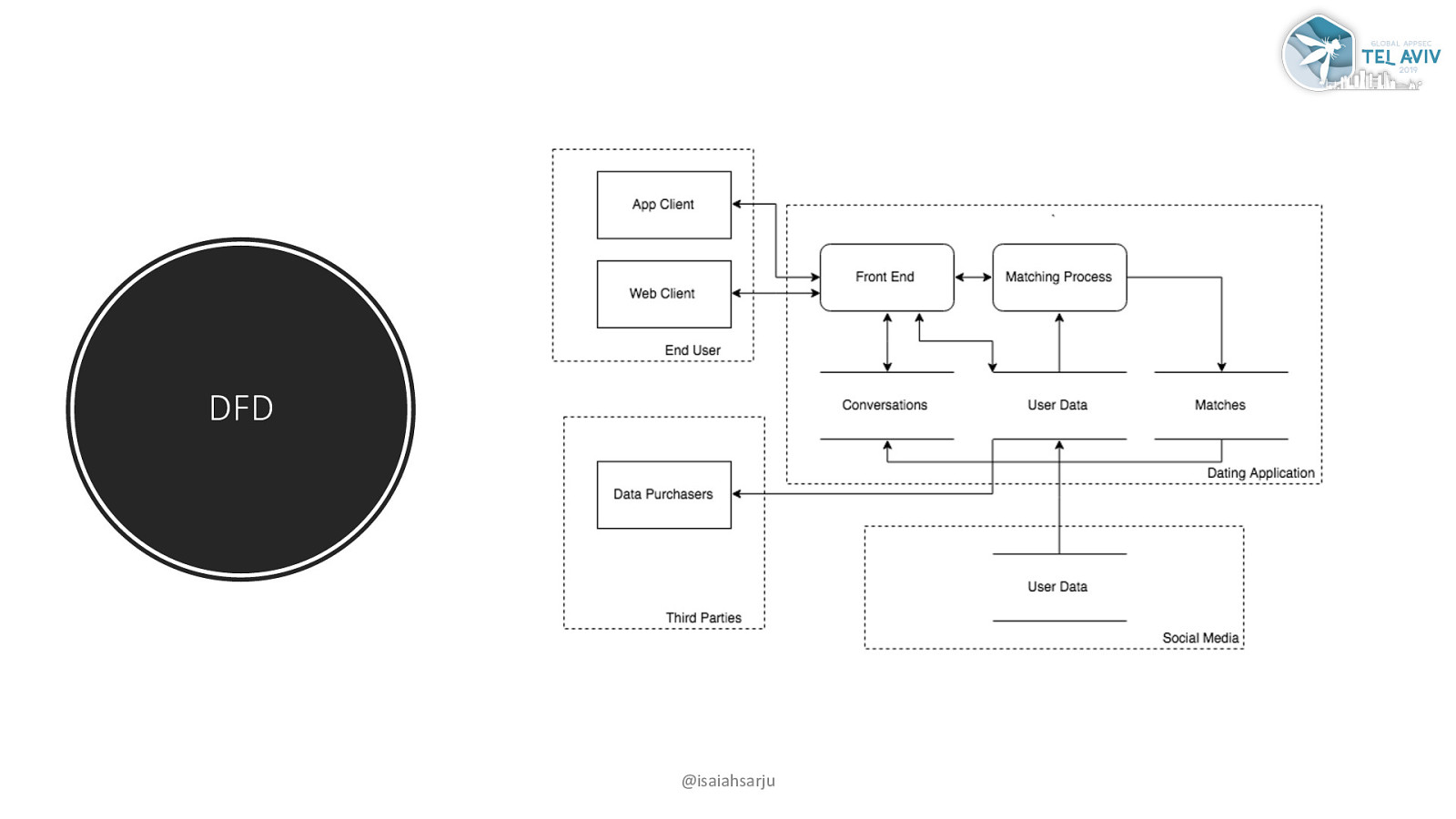
DFD @isaiahsarju
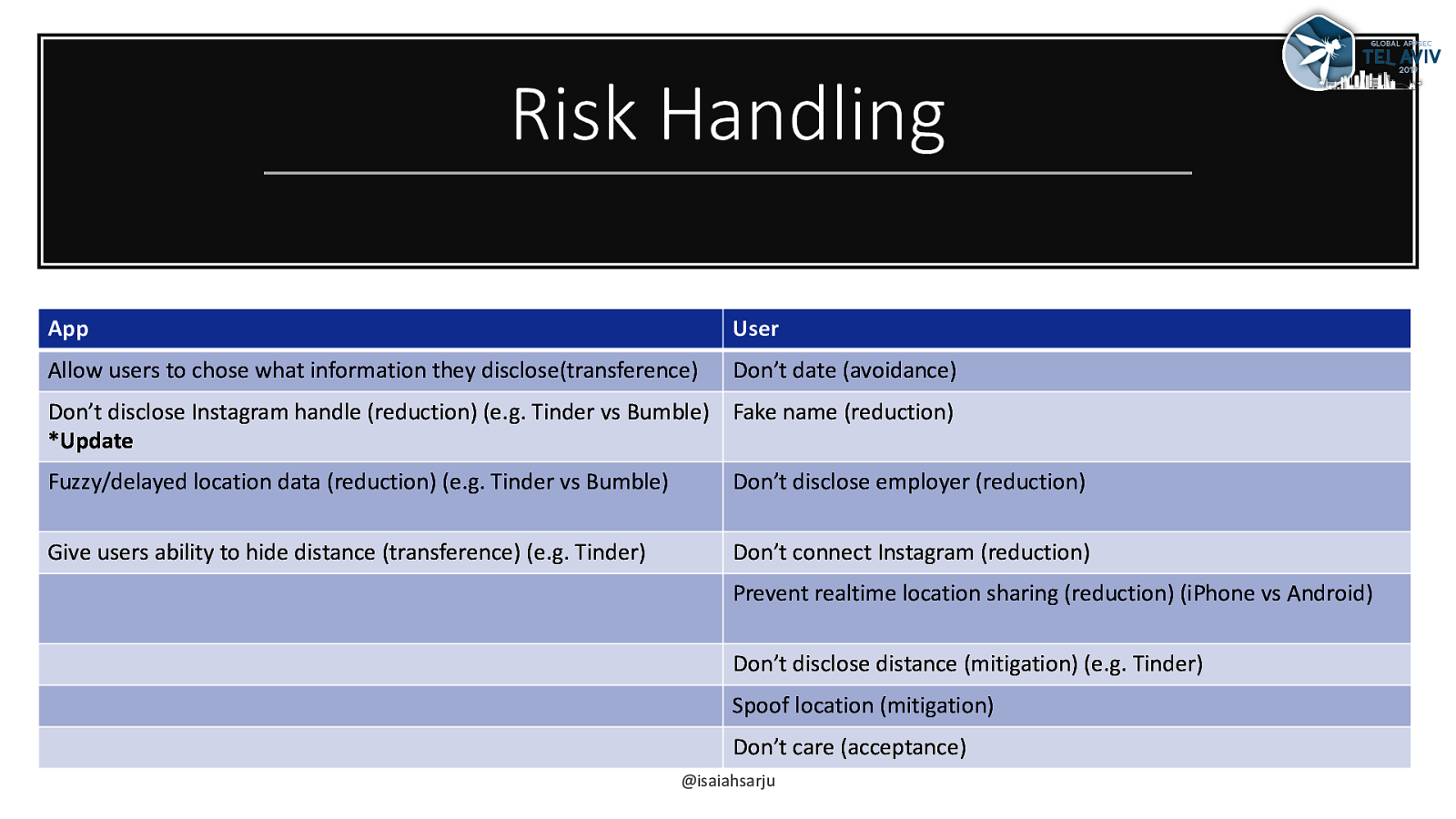
Risk Handling App User Allow users to chose what information they disclose(transference) Don’t date (avoidance) Don’t disclose Instagram handle (reduction) (e.g. Tinder vs Bumble) Fake name (reduction) *Update Fuzzy/delayed location data (reduction) (e.g. Tinder vs Bumble) Don’t disclose employer (reduction) Give users ability to hide distance (transference) (e.g. Tinder) Don’t connect Instagram (reduction) Prevent realtime location sharing (reduction) (iPhone vs Android) Don’t disclose distance (mitigation) (e.g. Tinder) Spoof location (mitigation) Don’t care (acceptance) @isaiahsarju
Helps builders build better Helps defenders think intentionally My Love of Threat Modeling Helps attackers prioritize attacks Helps everyone make intentional decisions about data responsibility @isaiahsarju
Sources • Hergovich, Philipp and Ortega, Josue, The Strength of Absent Ties: Social Integration via Online Dating (September 14, 2018), https://arxiv.org/pdf/1709.10478.pdf • Smith, Aaron, and Monica Anderson. “5 Facts about Online Dating.” Pew Research Center, Pew Research Center, 29 Feb. 2016, www.pewresearch.org/fact-tank/2016/02/29/5-facts-about-online-dating/. • C. Fitzpatrick, J. Birnholtz and J. R. Brubaker, “Social and Personal Disclosure in a Location-Based Real Time Dating App,” 2015 48th Hawaii International Conference on System Sciences, Kauai, HI, 2015, pp. 1983-1992. doi: 10.1109/HICSS.2015.237, http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=7070049&isnumber=7069647 • Ghorayshi, Azeen. “Grindr Is Sharing The HIV Status Of Its Users With Other Companies.” BuzzFeed News, BuzzFeed News, 3 Apr. 2018, www.buzzfeednews.com/article/azeenghorayshi/grindr-hiv-status-privacy#.yp0J48W0N. • Nandwani M., Kaushal R. (2018) Evaluating User Vulnerability to Privacy Disclosures over Online Dating Platforms. In: Barolli L., Enokido T. (eds) Innovative Mobile and Internet Services in Ubiquitous Computing. IMIS 2017. Advances in Intelligent Systems and Computing, vol 612. Springer, Cham • Duportail, Judith. “I Asked Tinder for My Data. It Sent Me 800 Pages of My Deepest, Darkest Secrets.” The Guardian, Guardian News and Media, 26 Sept. 2017, www.theguardian.com/technology/2017/sep/26/tinder-personal-data-dating-app-messages-hacked-sold. • “Are You on Tinder?” Checkmarx, Jan 2018. https://info.checkmarx.com/hubfs/Tinder_Research.pdf. • Shostack, Adam. Threat Modeling: Designing for Security. Wiley, 2014. @isaiahsarju

Q’s @isaiahsarju

Info • @isaiahsarju all over The Internet • https://github.com/isaiahsarju/presentations @isaiahsarju