Java Deserialization By Rohit Narayanan M
A presentation at Internal Team Session in September 2021 in by Rohit Narayanan M

Java Deserialization By Rohit Narayanan M
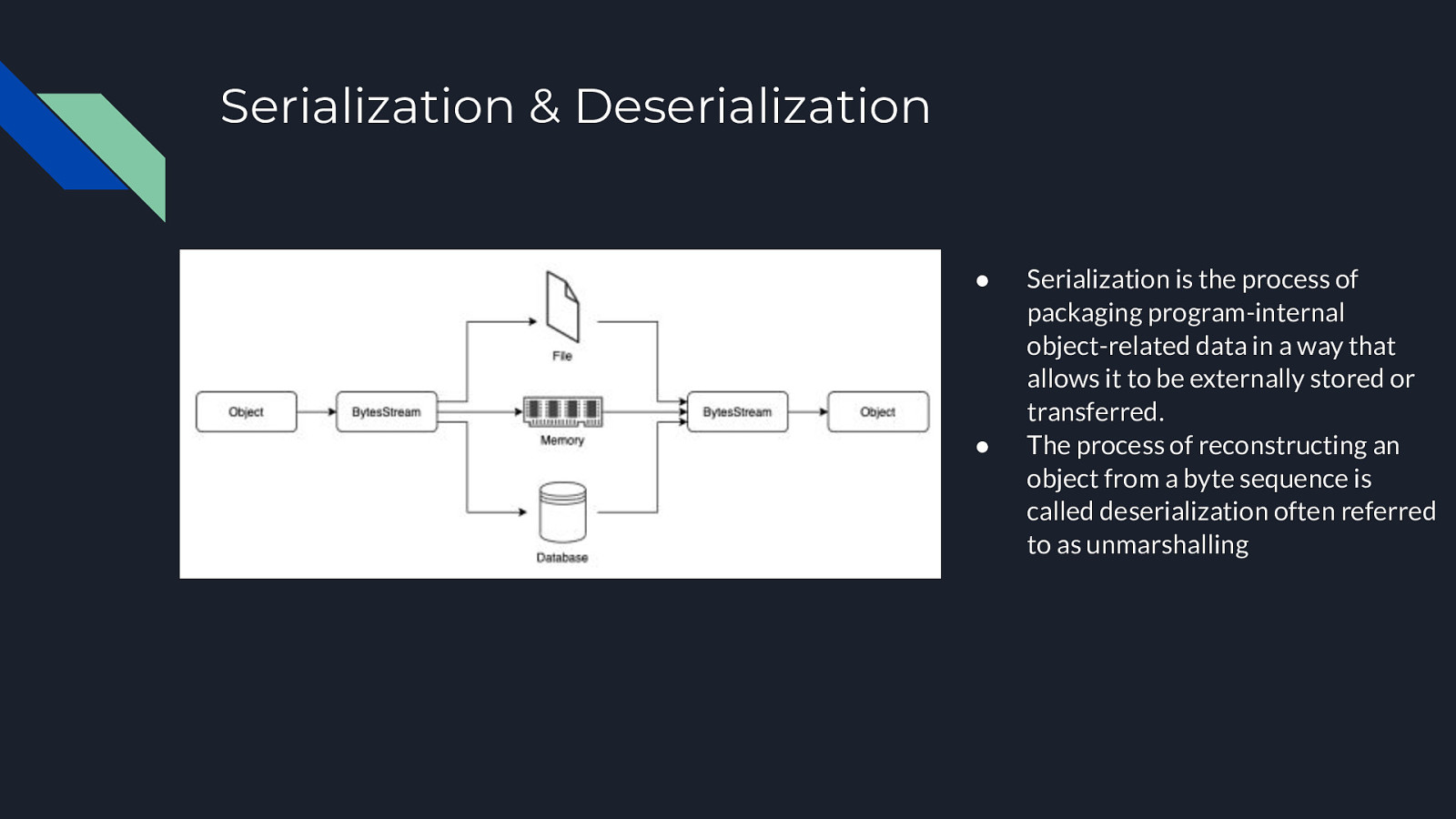
Serialization & Deserialization ● ● Serialization is the process of packaging program-internal object-related data in a way that allows it to be externally stored or transferred. The process of reconstructing an object from a byte sequence is called deserialization often referred to as unmarshalling

Why do We do it Serialization allows services and applications to communicate with each other by sending data that can be processed Serialization is also used for caching frequently used data eg : Used in Sun Java web console, where a vulnerability was found later Serialization in java also allows to preserve objects as different objects have different time spans
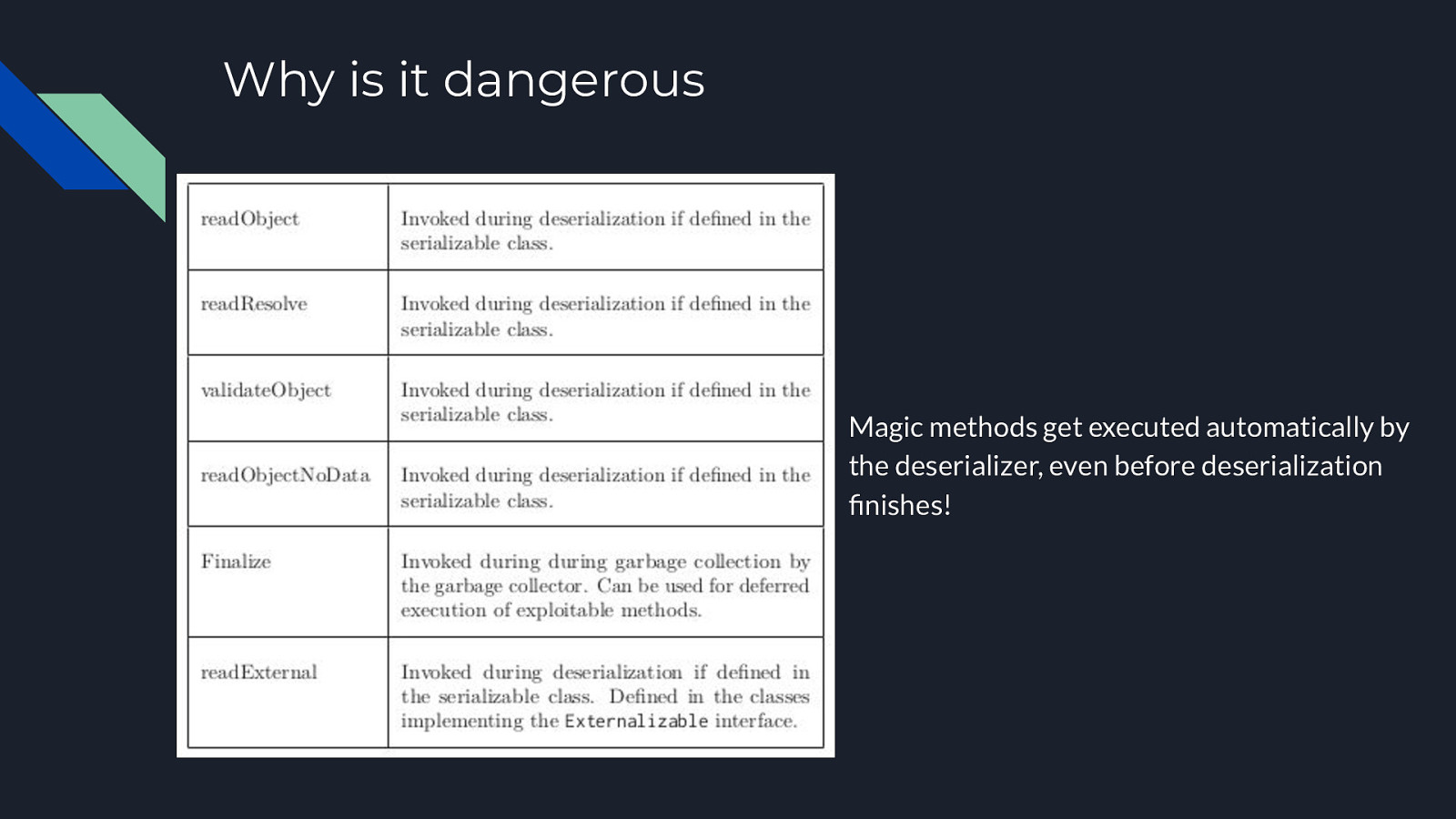
Why is it dangerous Magic methods get executed automatically by the deserializer, even before deserialization finishes!

Many serializable JDK classes implement these magic methods and call other methods, so there’s a lot of additional “known entry points.” HashMap ● ● Object.hashCode() Object.equals() PriorityQueue ● ● Comparator.compare() Comparable.compareTo()

Deserialization vulnerabilities in java For an application to be vulnerable to deserialization attacks it needs to meet two criteria. 1. 2. The application must accept serialized data from a location accessible to an attacker. The vulnerable class must be present on the classpath of the application accepting serialized data

Deserialization Gadgets A deserialization gadget is a class residing within the application code or a library, it must be reachable by the Java class loader, the class can be used to facilitate an attack. Gadget classes that are present in the core Java class libraries are often referred to as a “Golden Gadget”
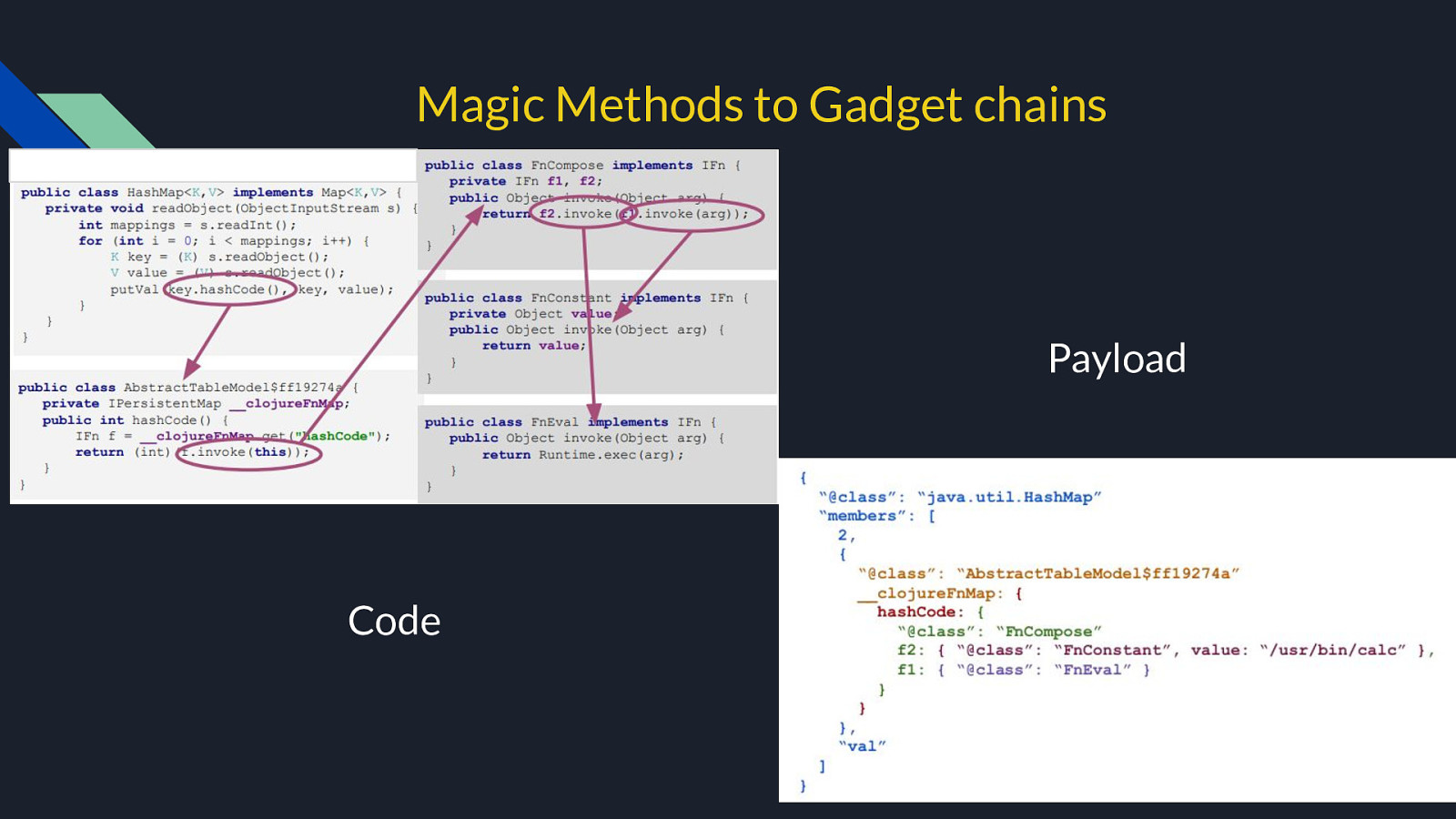
Magic Methods to Gadget chains Payload Code
How to find it To find deserialization vulnerabilities Look whether any serialization functions are used and check whether we can control the data to these functions Also if we don’t have code we can check for magic bytes 0xAc 0xEd or rO0 in the network traffic. When we find that we can deserialize data of our like, we search for gadget chains
Tools Locating the gadget chains is the complex part. For that we can use tools ● Ysoserial It is a collection of known gadget chains and exploits ● Gadget inspector It is a Java bytecode analysis tool for finding gadget chains in Java applications or packages. ● Joogle Programmatically query about types/methods of the classpath ● Marshalsec Deserialization payload generator for numerous libraries and gadget chains

Variable modification attack It is a type of modification attack where we modifies a variable in a serialized byte stream. We can do that using tools like serialization dumper which converts byte streams into more human readable form and back to byte streams. Deferred Execution Attack It’s a type of attack where the execution of the payload is deferred, until after the deserialization process has returned the object. So the payload is only executed after the object is destroyed by garbage collector. For that we can use the magic methods like finalize which is executed during garbage collection.
Polymorphism attack It is a type of attack where polymorphism is exploited in order to have methods in unintended objects invoked. So if there is 2 classes User and AdminUser and AdminUser class extends User class. Then if the attacker knows about the AdminUser class, then the he can create an Adminuser class byte stream and pass it to deserialize and then whatever is executed as user will be executed as AdminUser instead.
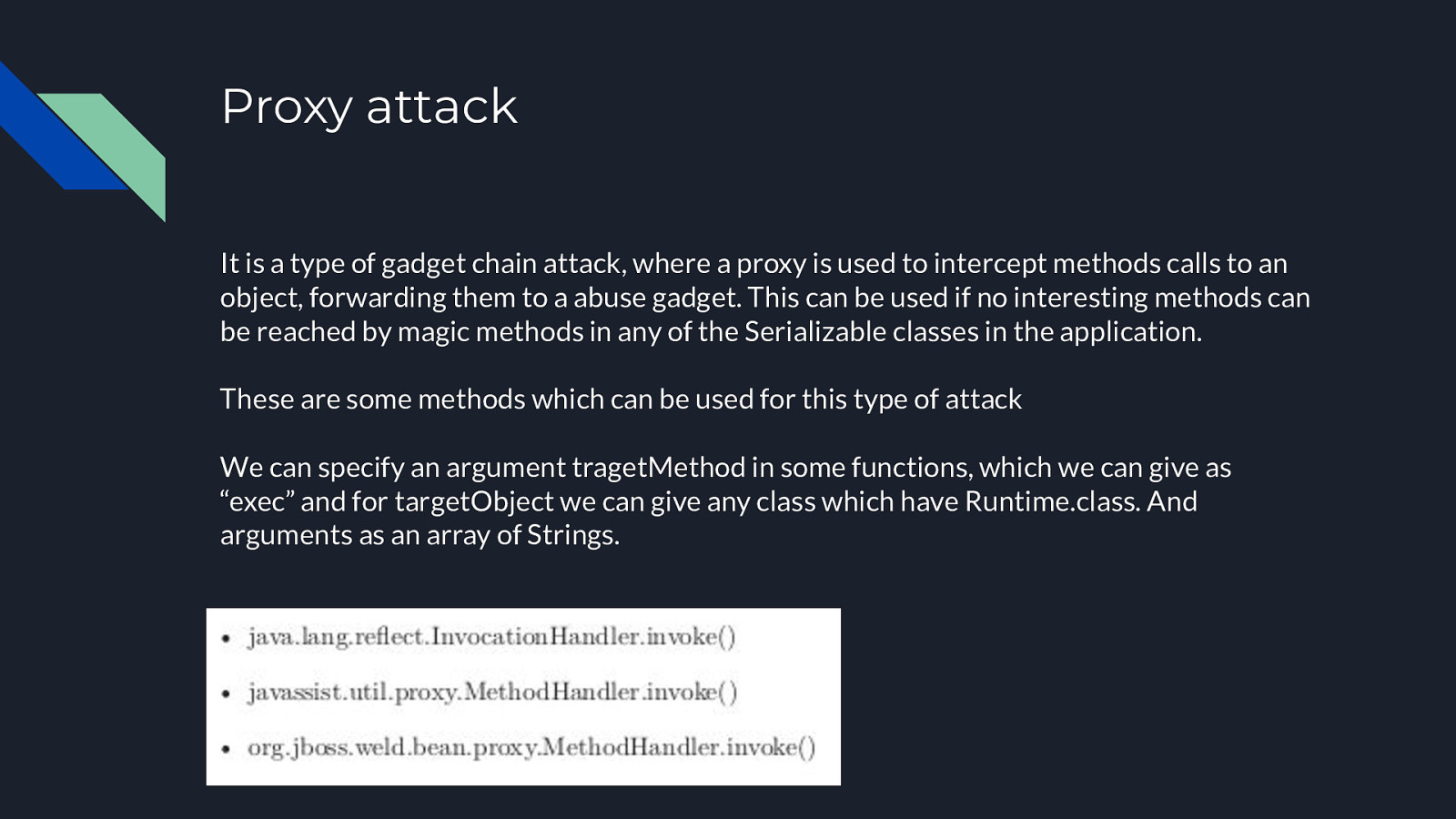
Proxy attack It is a type of gadget chain attack, where a proxy is used to intercept methods calls to an object, forwarding them to a abuse gadget. This can be used if no interesting methods can be reached by magic methods in any of the Serializable classes in the application. These are some methods which can be used for this type of attack We can specify an argument tragetMethod in some functions, which we can give as “exec” and for targetObject we can give any class which have Runtime.class. And arguments as an array of Strings.
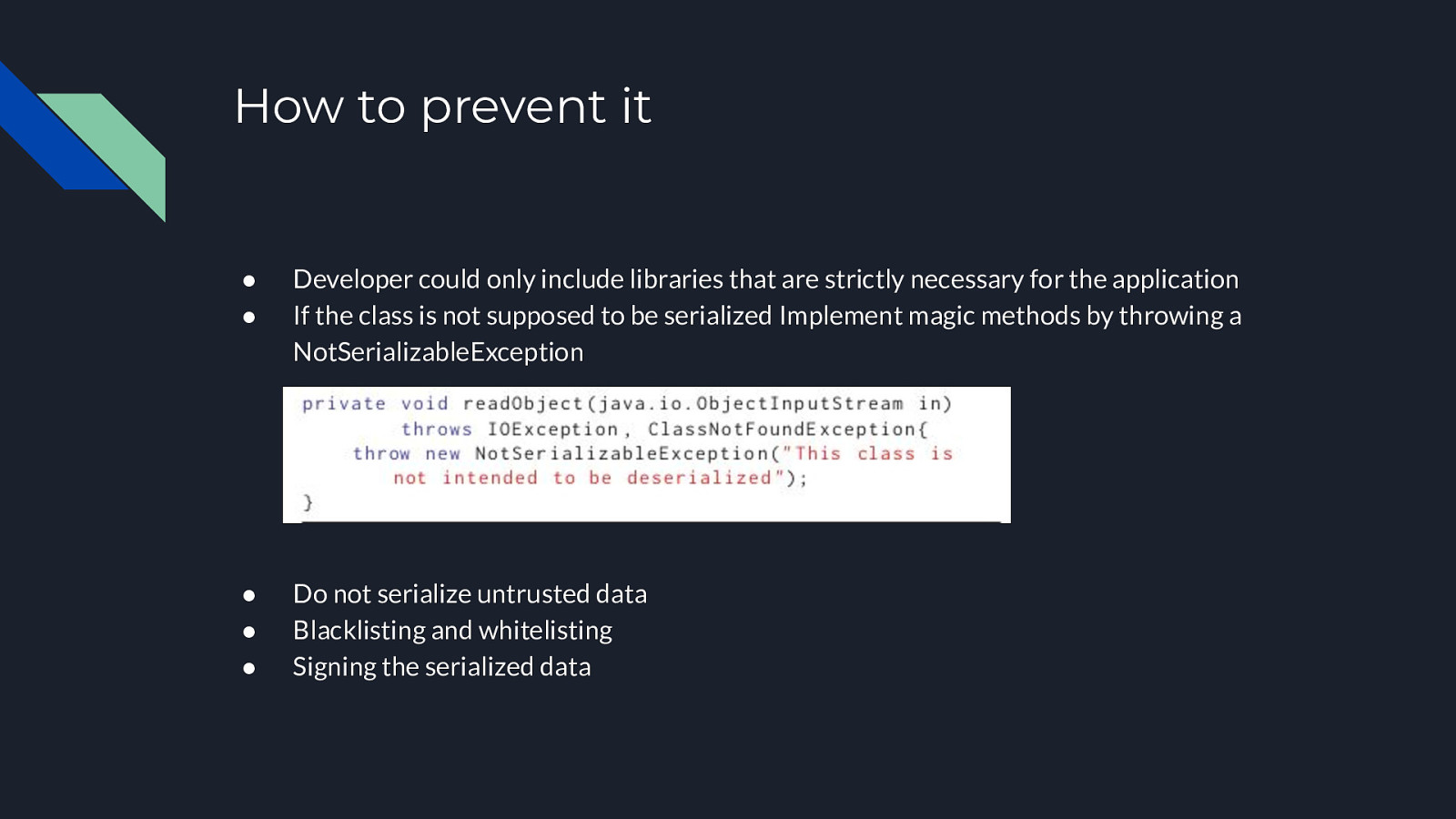
How to prevent it ● ● Developer could only include libraries that are strictly necessary for the application If the class is not supposed to be serialized Implement magic methods by throwing a NotSerializableException ● ● ● Do not serialize untrusted data Blacklisting and whitelisting Signing the serialized data
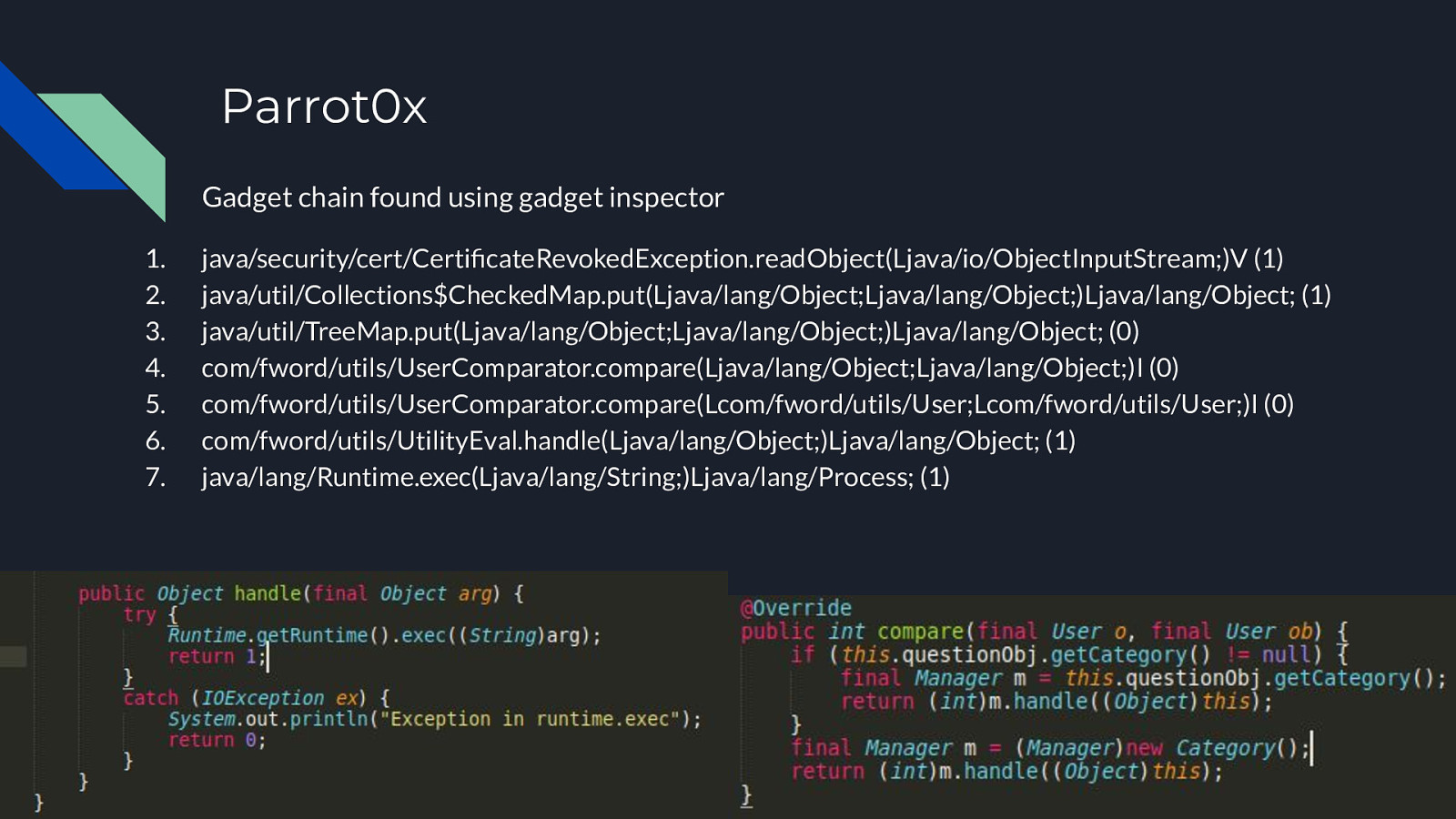
Parrot0x Gadget chain found using gadget inspector 1. 2. 3. 4. 5. 6. 7. java/security/cert/CertificateRevokedException.readObject(Ljava/io/ObjectInputStream;)V (1) java/util/Collections$CheckedMap.put(Ljava/lang/Object;Ljava/lang/Object;)Ljava/lang/Object; (1) java/util/TreeMap.put(Ljava/lang/Object;Ljava/lang/Object;)Ljava/lang/Object; (0) com/fword/utils/UserComparator.compare(Ljava/lang/Object;Ljava/lang/Object;)I (0) com/fword/utils/UserComparator.compare(Lcom/fword/utils/User;Lcom/fword/utils/User;)I (0) com/fword/utils/UtilityEval.handle(Ljava/lang/Object;)Ljava/lang/Object; (1) java/lang/Runtime.exec(Ljava/lang/String;)Ljava/lang/Process; (1)
Tools ● ● ● ● ● ● https://github.com/frohoff/ysoserial https://github.com/Contrast-Security-OSS/joogle https://github.com/mbechler/marshalsec https://github.com/JackOfMostTrades/gadgetinspector https://github.com/ikkisoft/SerialKiller https://github.com/NickstaDB/SerializationDumper
References ● ● ● ● ● https://www.blackhat.com/us-18/briefings/schedule/#automated-discovery-of-deseriali zation-gadget-chains-10668 https://www.youtube.com/watch?v=MTfE2OgUlKc http://www.blackhat.com/presentations/bh-federal-06/BH-Fed-06-Schoenefeld-up.pdf https://frohoff.github.io/appseccali-marshalling-pickles/ https://appsecus2018.sched.com/event/F04J