Creating Secure Software Daniel Sawano Kraków, 9-11 May 2018 Benefits from Cloud Thinking
A presentation at GeeCON Kraków 2018 in May 2018 in Kraków, Poland by Daniel Sawano

Creating Secure Software Daniel Sawano Kraków, 9-11 May 2018 Benefits from Cloud Thinking

Daniel Sawano

@DanielSawano #SecureByDesign #GeeCON Security benefits from cloud thinking?
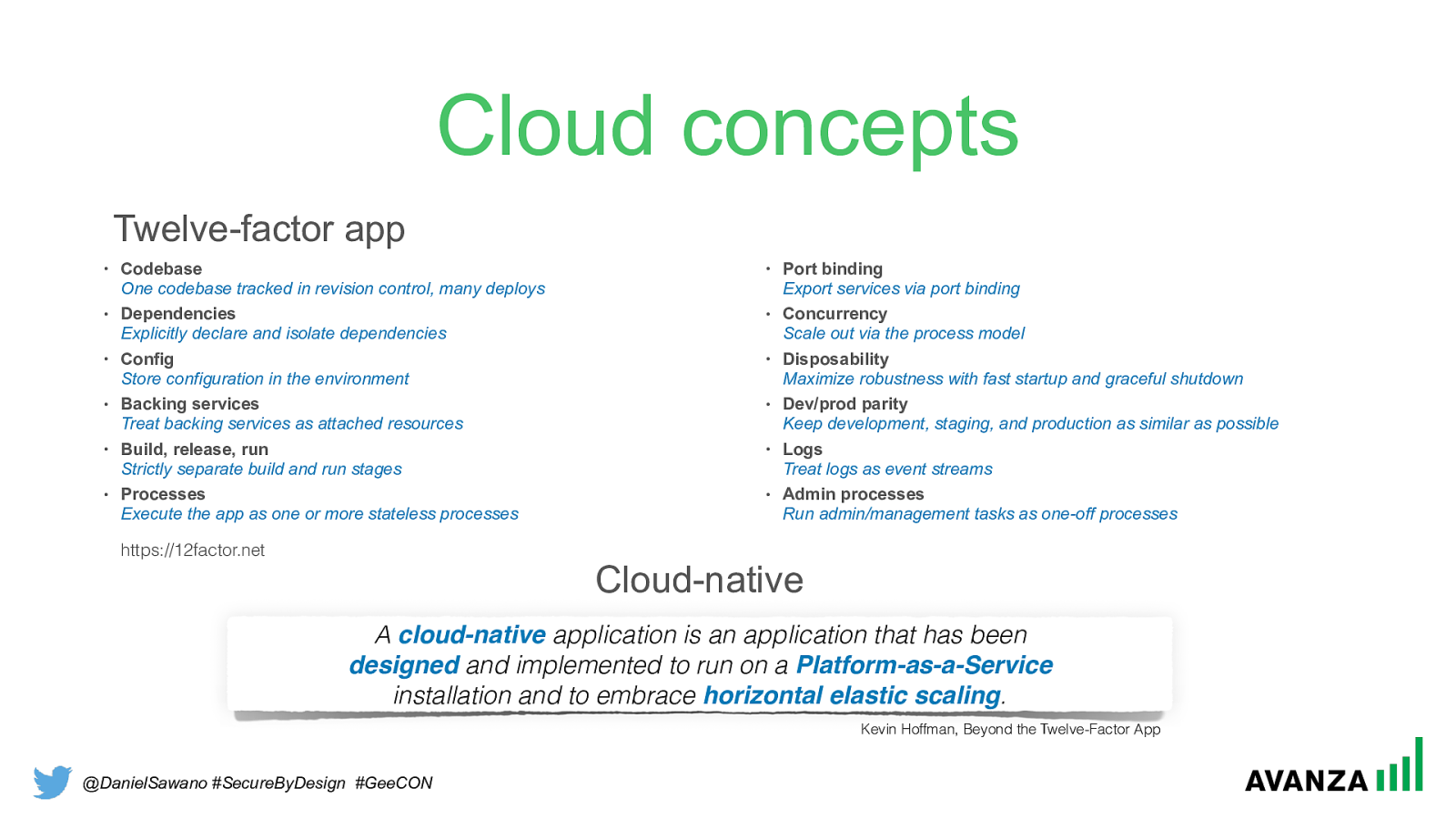
@DanielSawano #SecureByDesign #GeeCON Cloud concepts • Codebase One codebase tracked in revision control, many deploys
• Dependencies Explicitly declare and isolate dependencies
• Config Store configuration in the environment
• Backing services Treat backing services as attached resources
• Build, release, run Strictly separate build and run stages
• Processes Execute the app as one or more stateless processes
• Port binding Export services via port binding
• Concurrency Scale out via the process model
• Disposability Maximize robustness with fast startup and graceful shutdown
• Dev/prod parity Keep development, staging, and production as similar as possible
• Logs Treat logs as event streams
• Admin processes Run admin/management tasks as one-off processes Twelve-factor app https://12factor.net A cloud-native application is an application that has been designed and implemented to run on a Platform-as-a-Service
installation and to embrace horizontal elastic scaling . Cloud-native Kevin Hoffman, Beyond the Twelve-Factor App

@DanielSawano #SecureByDesign #GeeCON What we’ll cover today • Configuration • Separate processes • Logging • The three R’s of enterprise security

@DanielSawano #SecureByDesign #GeeCON Configuration “Store configuration in the environment”
@DanielSawano #SecureByDesign #GeeCON Configuration Configuration in code
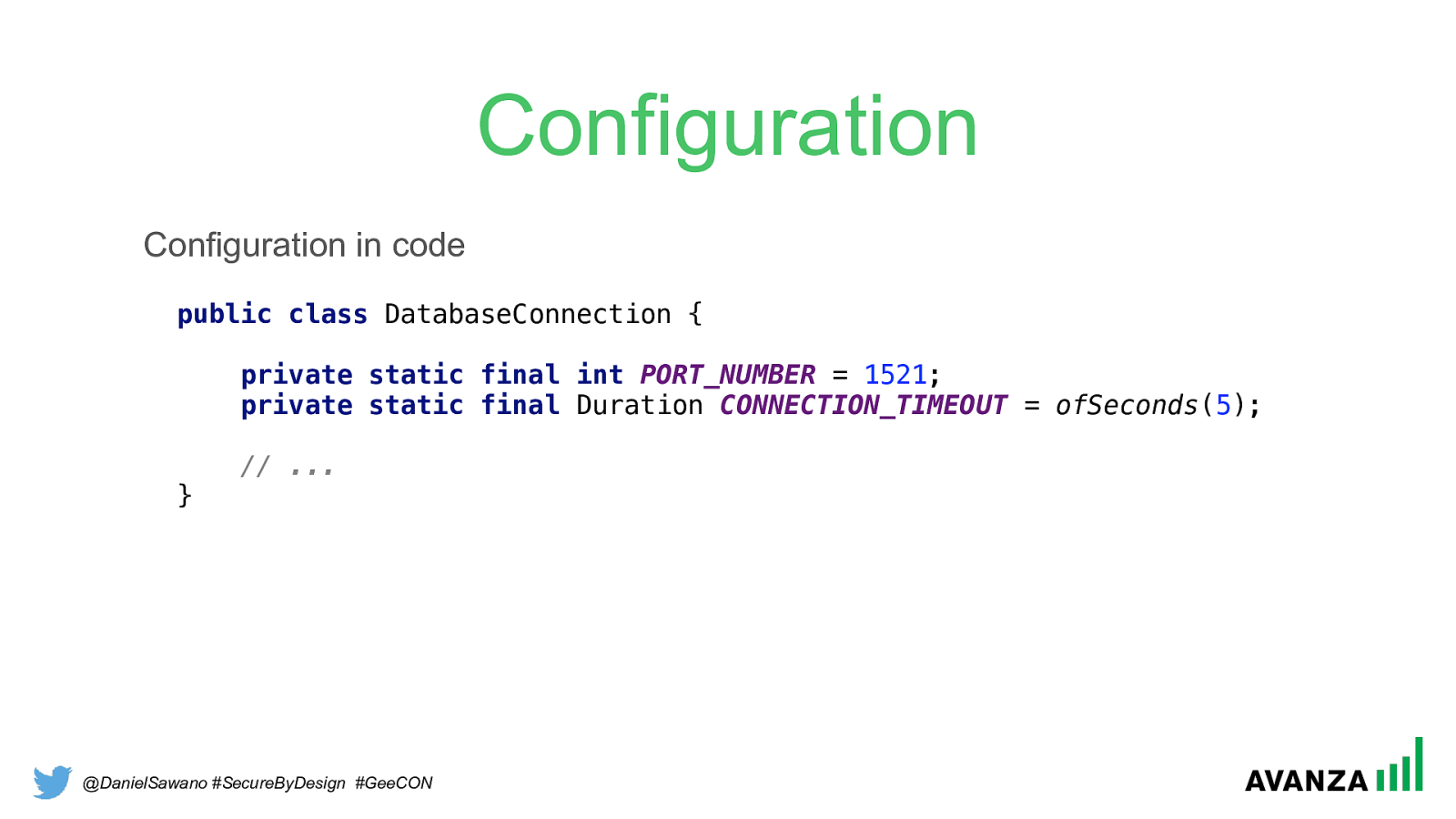
@DanielSawano #SecureByDesign #GeeCON Configuration public class DatabaseConnection {
1521 ;
ofSeconds ( 5 );
// ... } Configuration in code
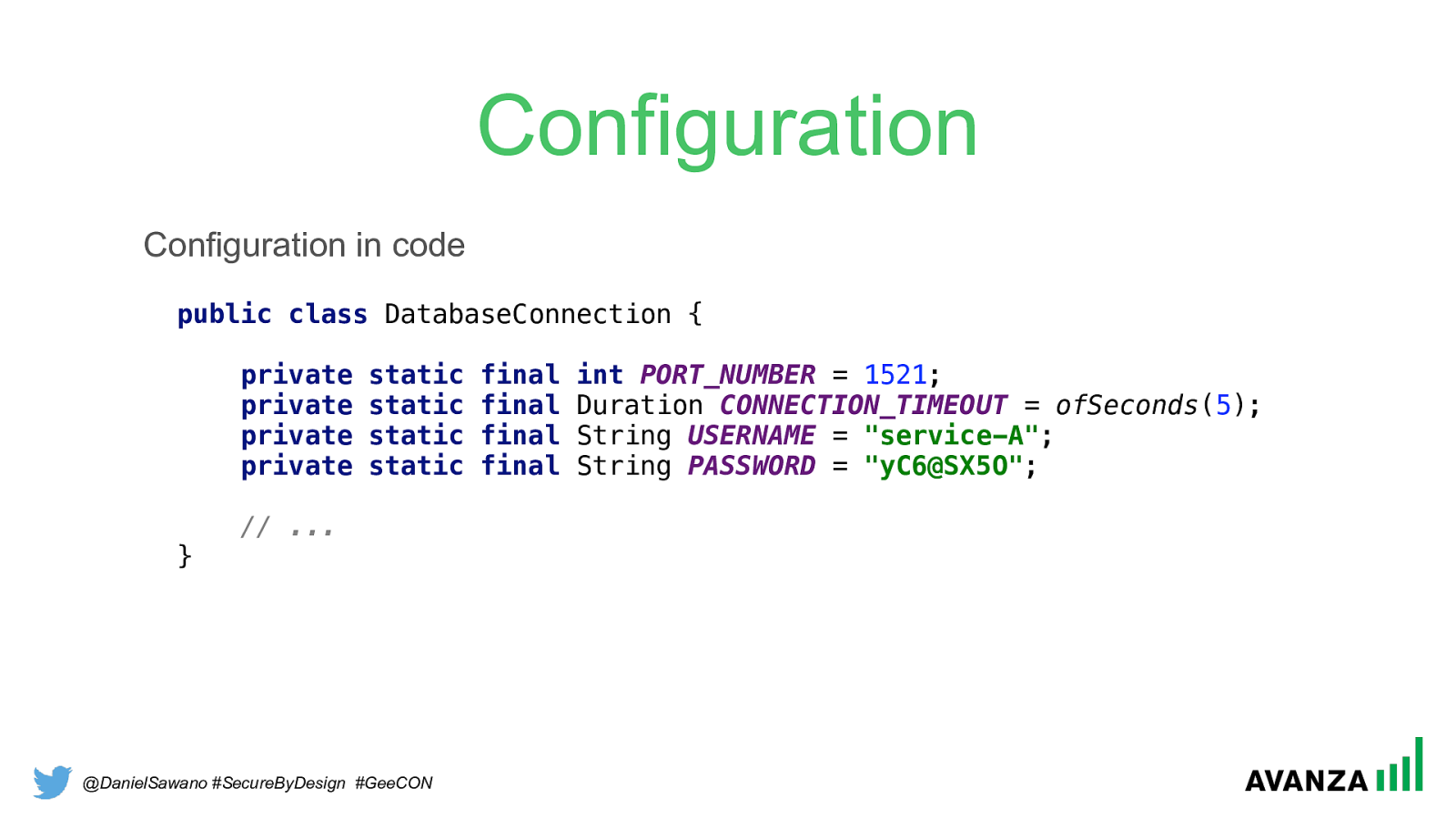
@DanielSawano #SecureByDesign #GeeCON Configuration public class DatabaseConnection {
1521 ;
ofSeconds ( 5 );
"service-A" ;
"yC6@SX5O" ;
// ... } Configuration in code

@DanielSawano #SecureByDesign #GeeCON Configuration Configuration in code — challenges
• Anyone with access to the code can read the secrets • No audit trail
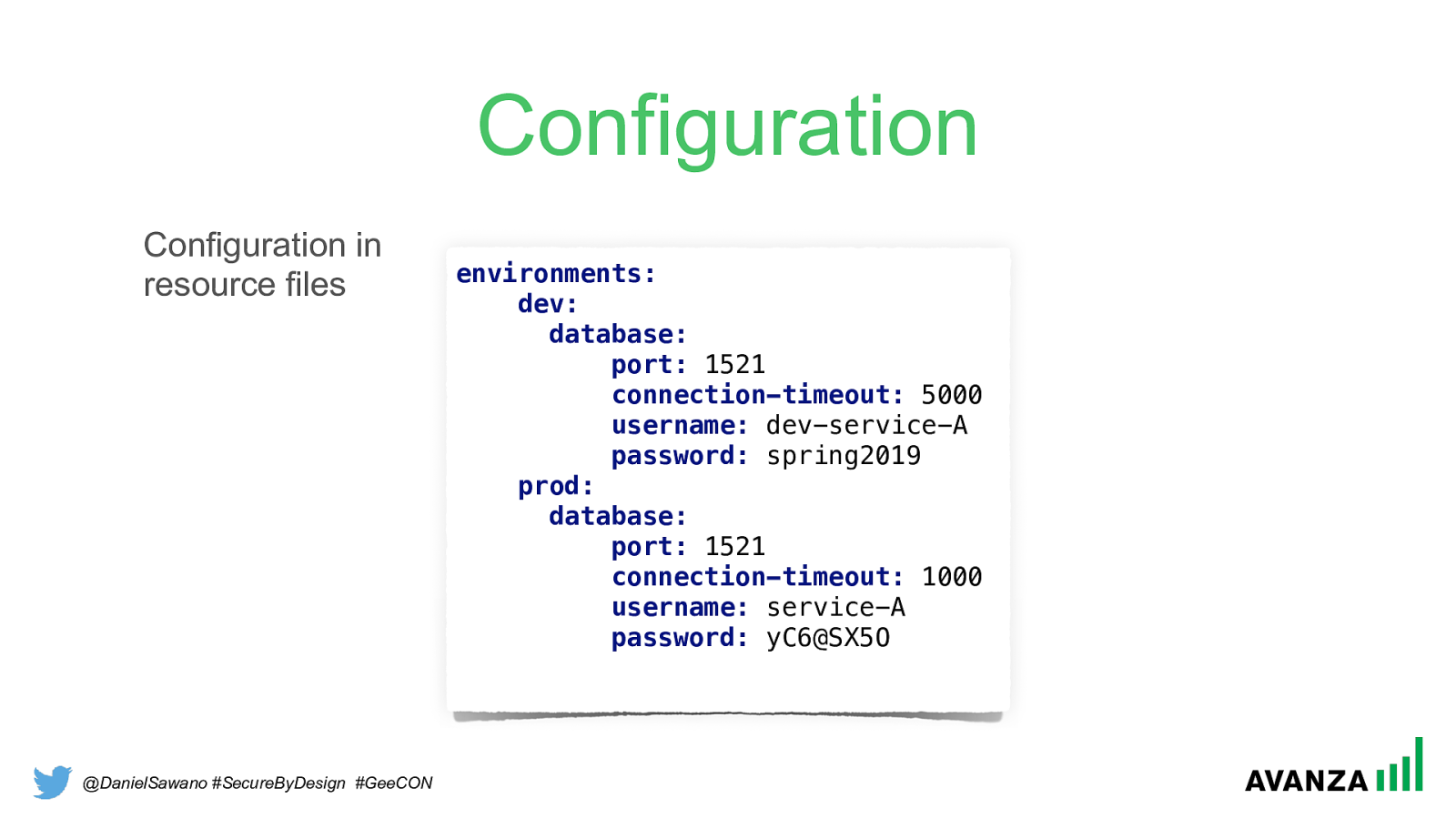
@DanielSawano #SecureByDesign #GeeCON Configuration environments: dev: database: port: 1521
connection-timeout: 5000
username: dev-service-A
password: spring2019
prod: database: port: 1521
connection-timeout: 1000
username: service-A
password: yC6@SX5O Configuration in resource files

@DanielSawano #SecureByDesign #GeeCON Configuration Configuration in resource files — challenges
• Anyone with access to the conf can read the secrets • No, or very limited, audit trail • Encrypting values creates new problems
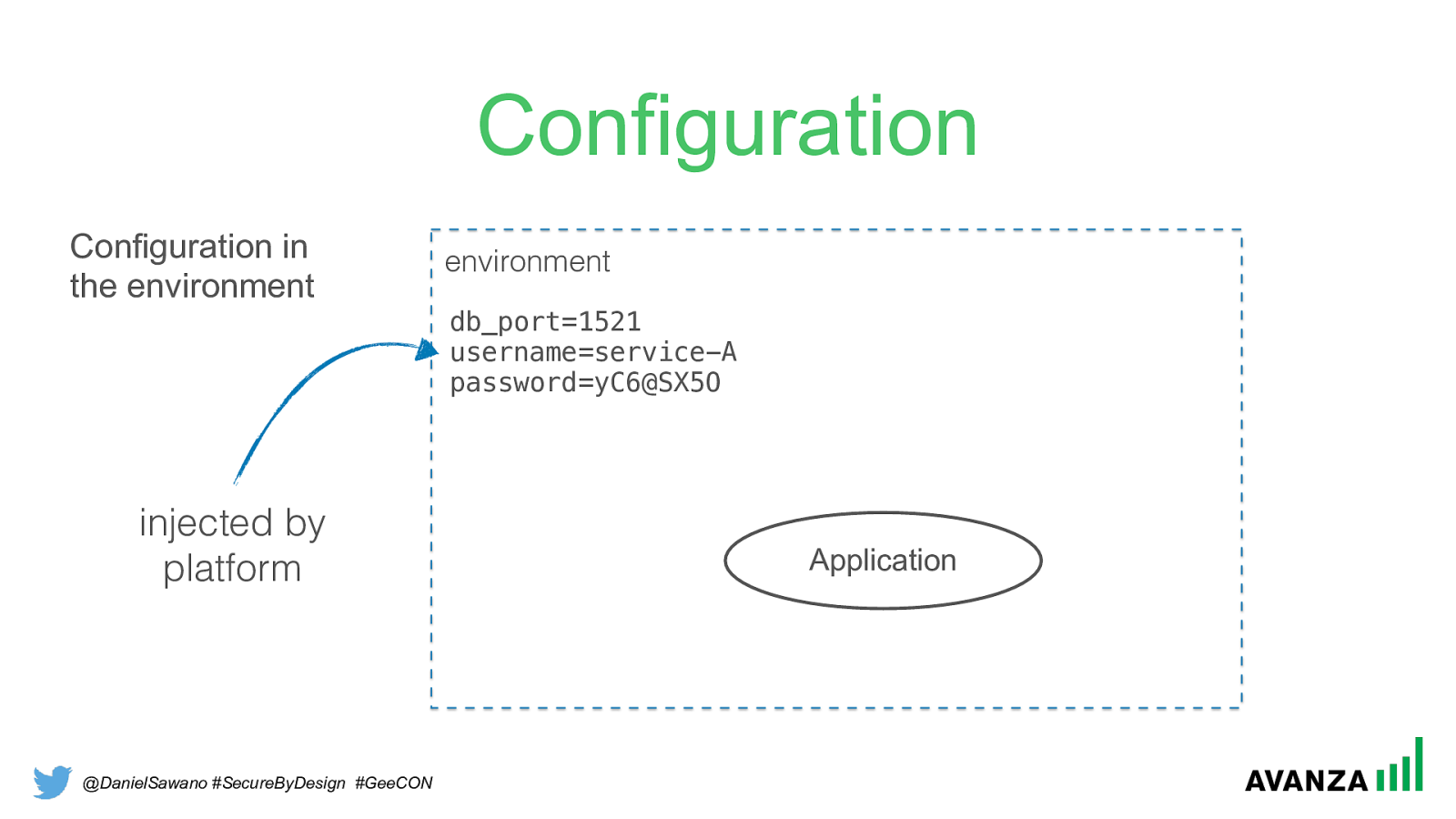
@DanielSawano #SecureByDesign #GeeCON Configuration environment db_port=1521 username=service-A password=yC6@SX5O Application injected by platform Configuration in the environment
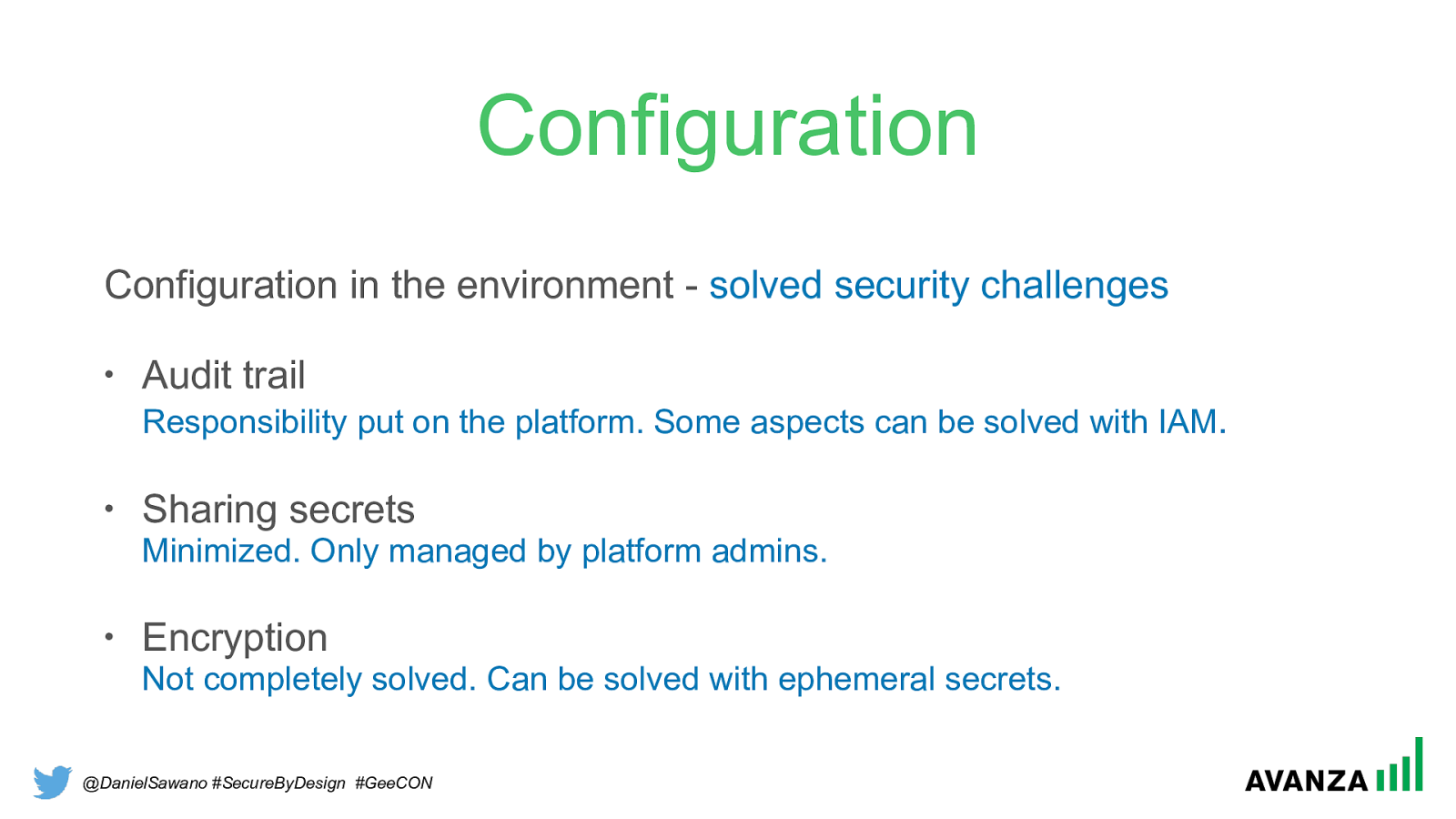
@DanielSawano #SecureByDesign #GeeCON Configuration Configuration in the environment - solved security challenges
• Audit trail Responsibility put on the platform. Some aspects can be solved with IAM .
• Sharing secrets Minimized. Only managed by platform admins.
• Encryption Not completely solved. Can be solved with ephemeral secrets.

@DanielSawano #SecureByDesign #GeeCON What we’ll cover today ✓ Configuration • Separate processes • Logging • The three R’s of enterprise security
@DanielSawano #SecureByDesign #GeeCON Separate processes Run apps as separate stateless processes
@DanielSawano #SecureByDesign #GeeCON Separate processes • Run the app as multiple stateless processes
• Separate the deployment and running of the application • Only communicate via backing services
@DanielSawano #SecureByDesign #GeeCON Separate processes Run the app as multiple stateless processes • Security benefit: increased availability and integrity

@DanielSawano #SecureByDesign #GeeCON CIA • Confidentiality — data must only be disclosed to authorized users
• Integrity — data modification is only allowed in an authorized manner
• Availability — data must be available when needed
@DanielSawano #SecureByDesign #GeeCON Separate processes Run the app as multiple stateless processes • Security benefit: increased availability and integrity
@DanielSawano #SecureByDesign #GeeCON Separate processes Separate the deployment and running of the application • Security benefit: principle of least privilege
@DanielSawano #SecureByDesign #GeeCON Separate processes Only communicate via backing services • Security benefit: improves availability and integrity by allowing apps to be stateless

@DanielSawano #SecureByDesign #GeeCON What we’ll cover today ✓ Configuration ✓ Separate processes • Logging • The three R’s of enterprise security
@DanielSawano #SecureByDesign #GeeCON Logging Use logging as a service
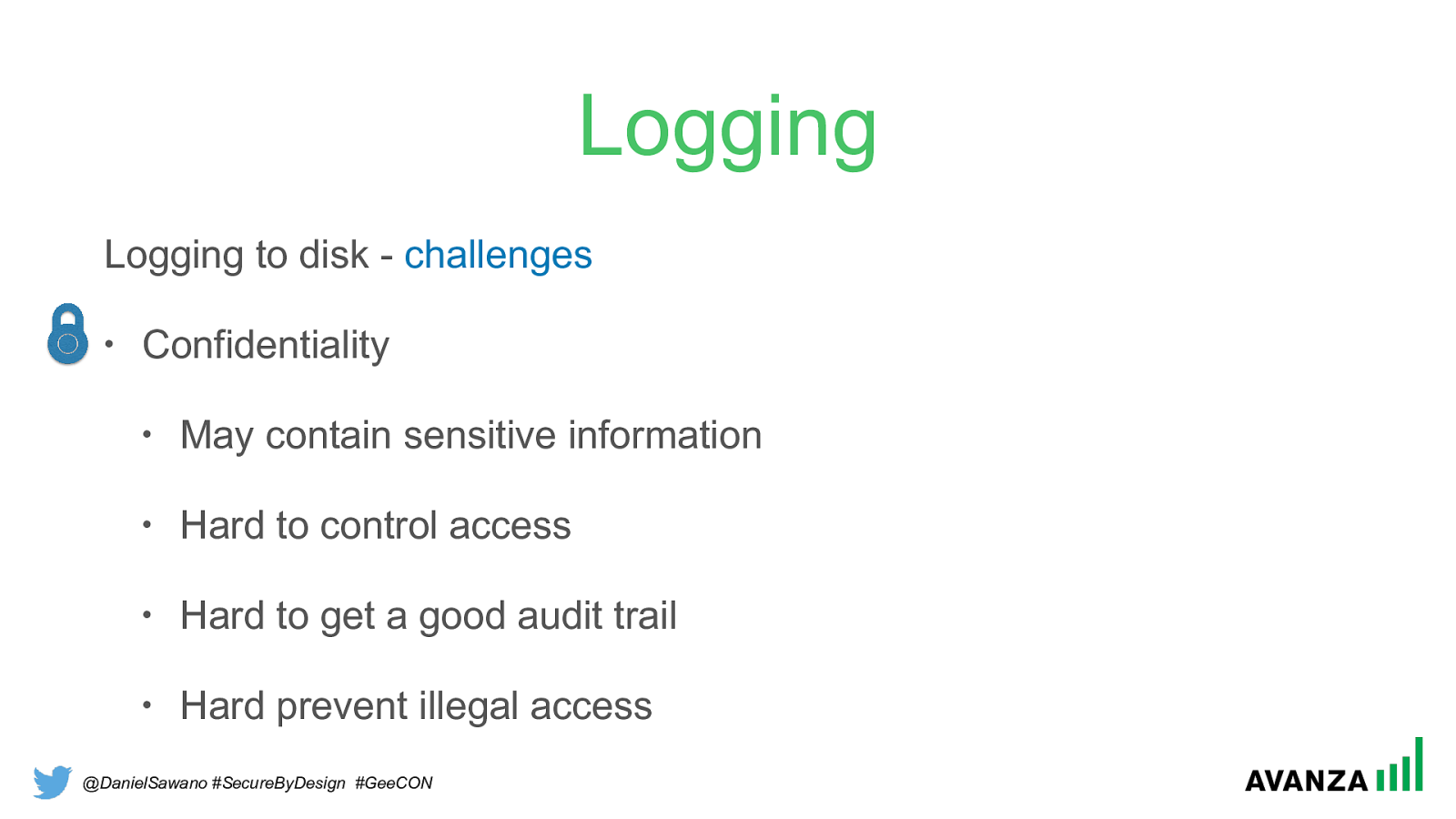
@DanielSawano #SecureByDesign #GeeCON Logging Logging to disk - challenges
• Confidentiality • May contain sensitive information • Hard to control access • Hard to get a good audit trail • Hard prevent illegal access

@DanielSawano #SecureByDesign #GeeCON Logging Logging to disk - challenges
• Integrity • Maintaining integrity often overlooked • Write access to log files usually not restricted or audited

@DanielSawano #SecureByDesign #GeeCON Logging Logging to disk - challenges
• Availability • Log files are lost when servers are replaced • Disk space runs out
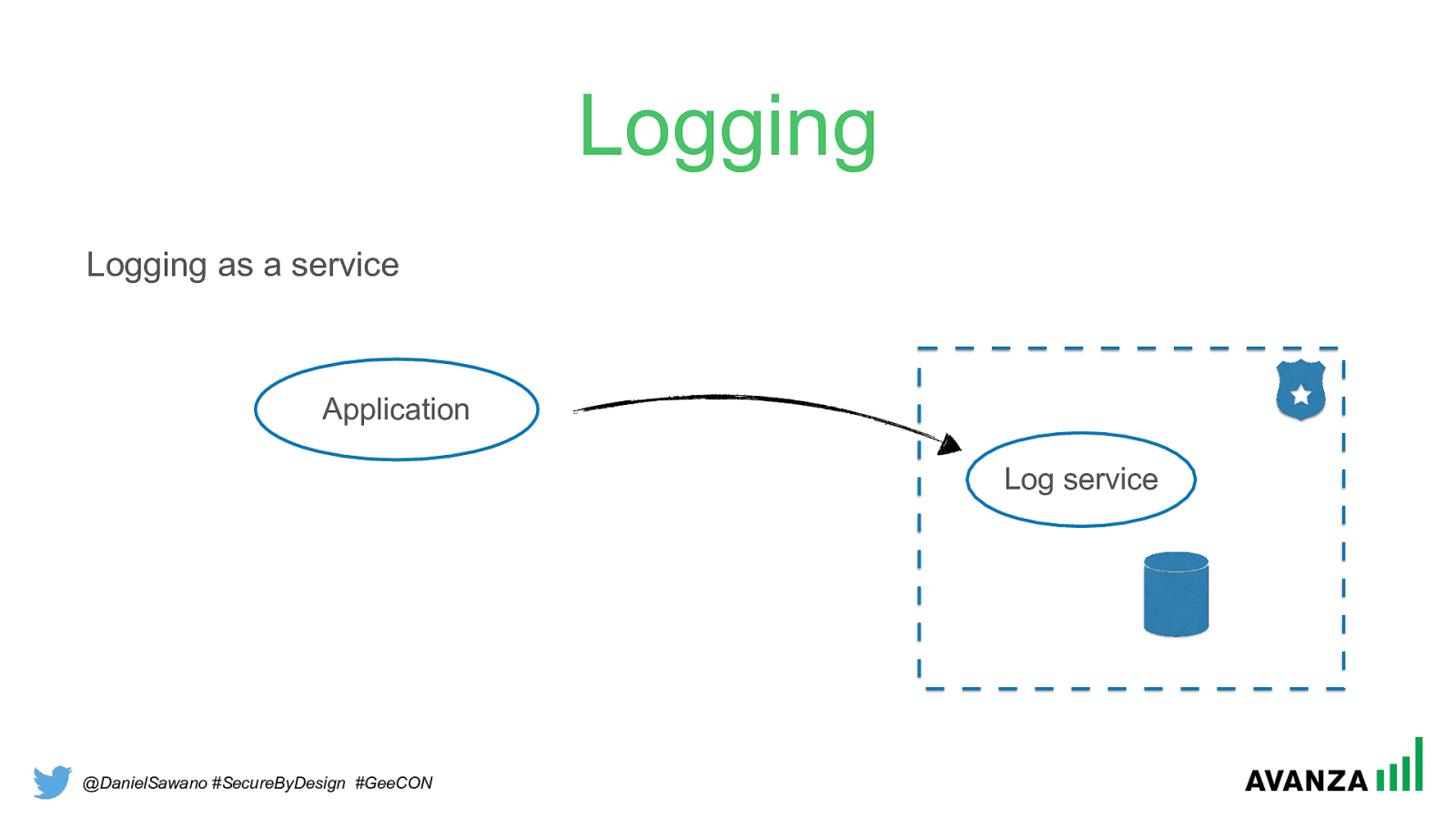
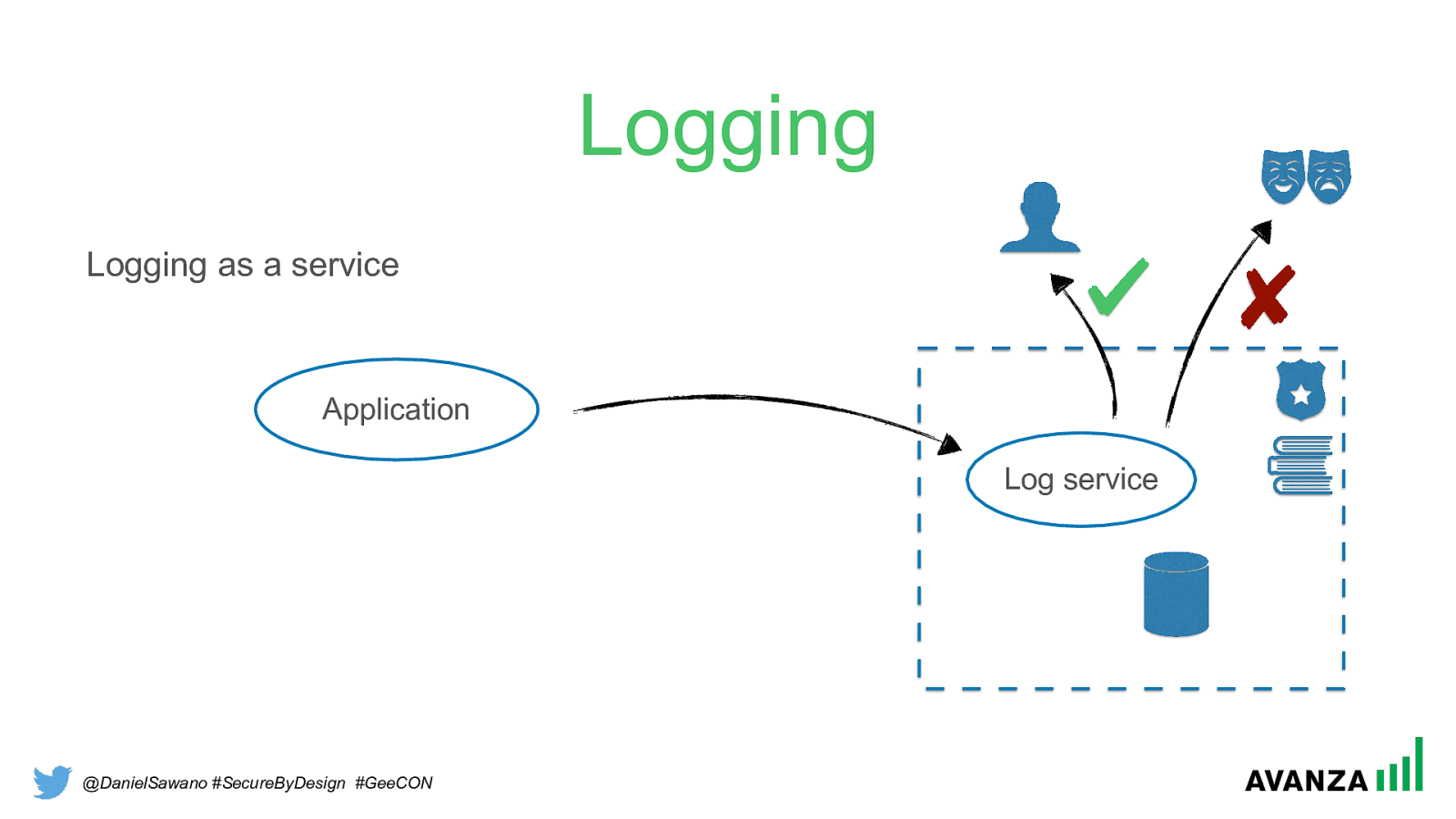
@DanielSawano #SecureByDesign #GeeCON Logging Logging as a service Application Log service
@DanielSawano #SecureByDesign #GeeCON Logging Logging as a service Application Log service

@DanielSawano #SecureByDesign #GeeCON Logging Logging as a service - solved security challenges
• Confidentiality Easy to restrict access and prevent illegal access. Audit trail.
• Integrity Mutating operations not exposed/implemented. Can even digitally sign log events
• Availability Log storage is handled explicitly so no log files can go missing Storage is a primary concern so no accidental shortage of disk space.

@DanielSawano #SecureByDesign #GeeCON What we’ll cover today ✓ Configuration ✓ Separate processes ✓ Logging • The three R’s of enterprise security

@DanielSawano #SecureByDesign #GeeCON The three R’s The three R’s of enterprise security Justin Smith, 2016
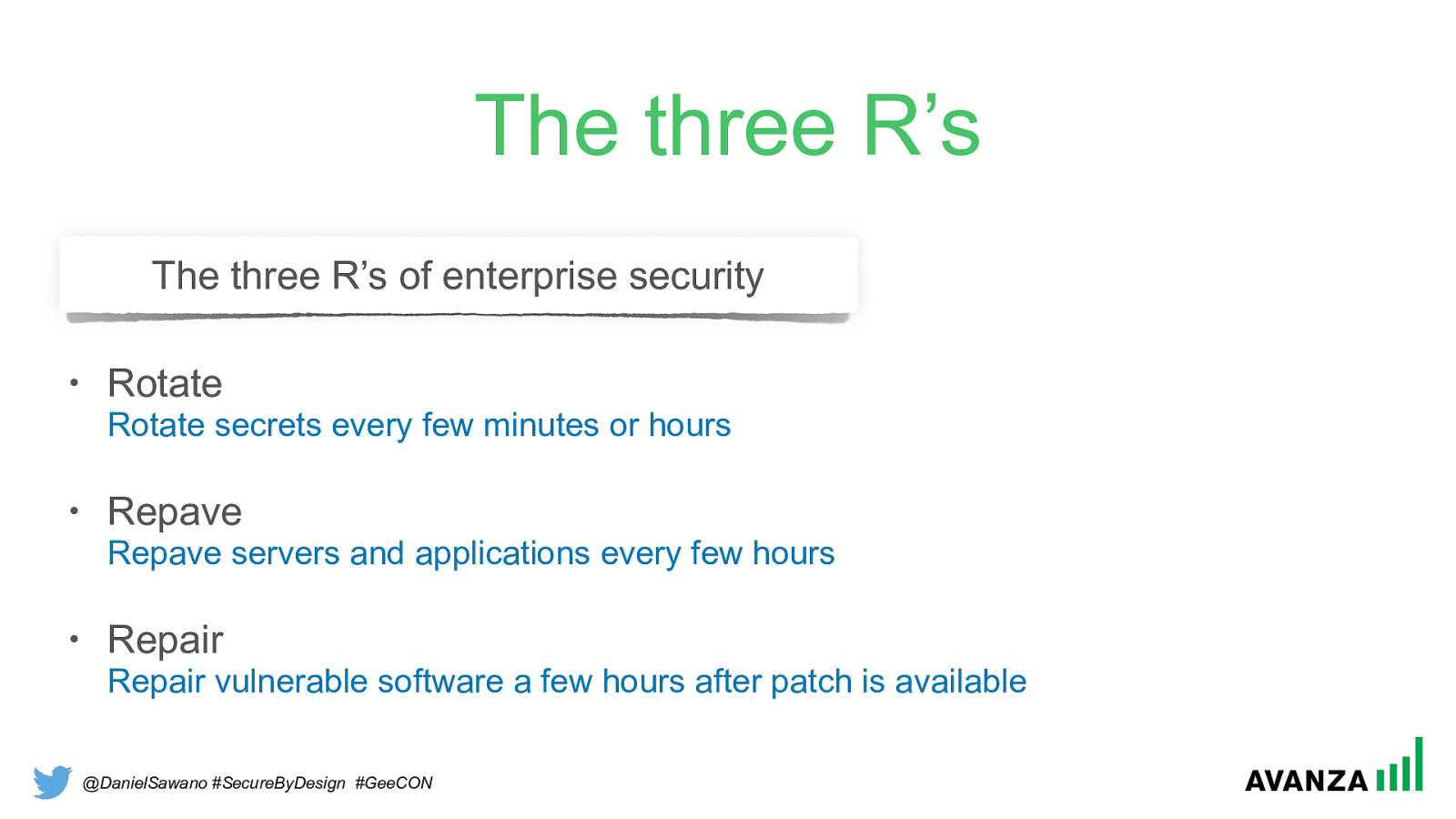
@DanielSawano #SecureByDesign #GeeCON The three R’s The three R’s of enterprise security • Rotate Rotate secrets every few minutes or hours
• Repave Repave servers and applications every few hours
• Repair Repair vulnerable software a few hours after patch is available

@DanielSawano #SecureByDesign #GeeCON The three R’s Increase change to reduce risk
@DanielSawano #SecureByDesign #GeeCON
The three R’s
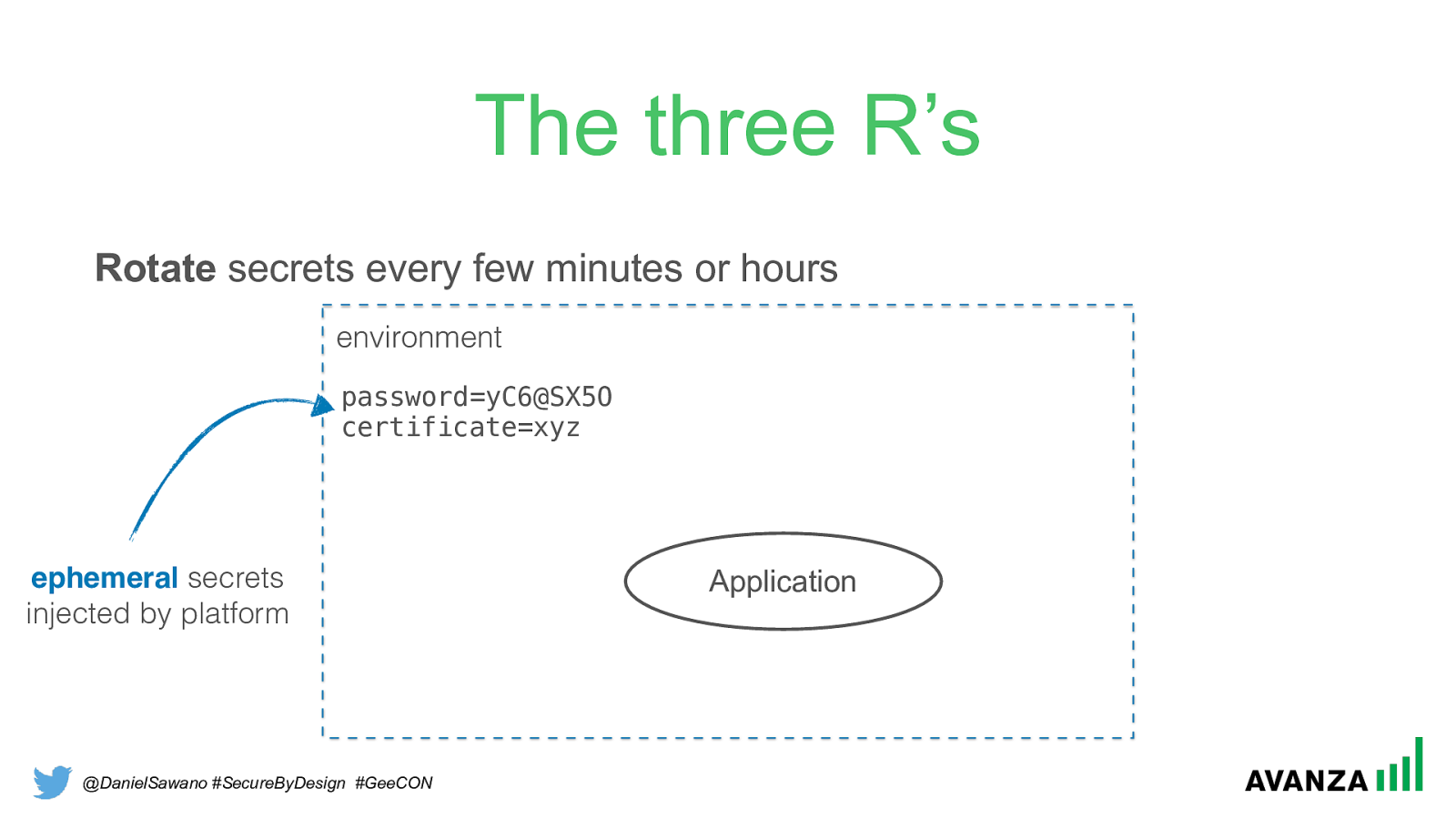
Rotate
secrets every few minutes or hours
environment
password=yC6@SX5O
certificate=xyz
Application
ephemeral
secrets
injected by platform
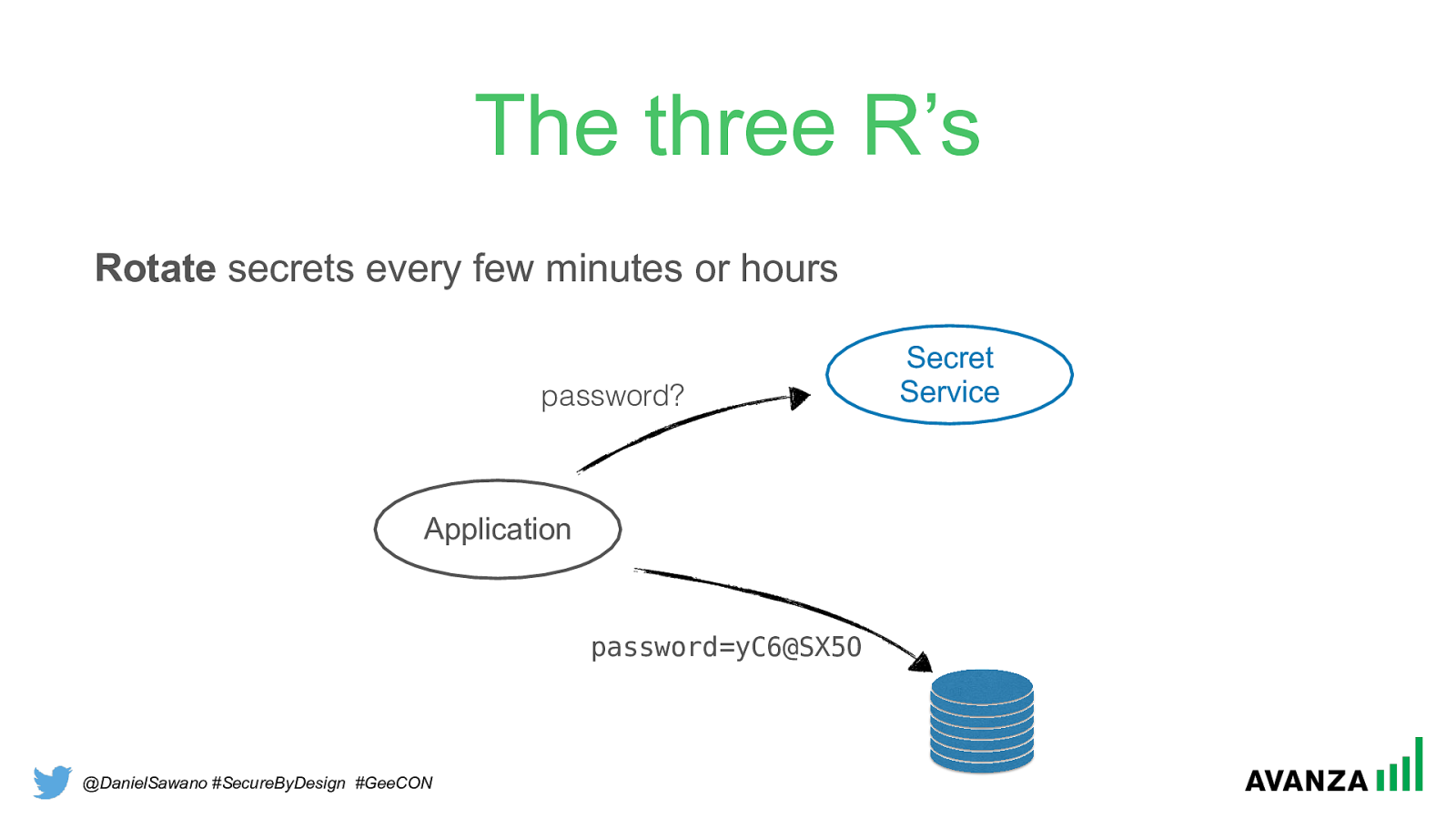
@DanielSawano #SecureByDesign #GeeCON The three R’s Rotate secrets every few minutes or hours password=yC6@SX5O Application password? Secret Service

@DanielSawano #SecureByDesign #GeeCON The three R’s • Passwords • Certificates • Access tokens • … Rotate secrets every few minutes or hours
@DanielSawano #SecureByDesign #GeeCON The three R’s Repave servers and applications every few hours • Recreate servers and apps from a know good state • Use rolling deployments to eliminate downtime • Burn old instances to the ground • If running containers, consider also repaving the host
@DanielSawano #SecureByDesign #GeeCON The three R’s • Applies to both operating systems and applications • No incremental updates, repave instead Repair vulnerable software a few hours after patch is available

@DanielSawano #SecureByDesign #GeeCON The three R’s Repair vulnerable software a few hours after patch is available
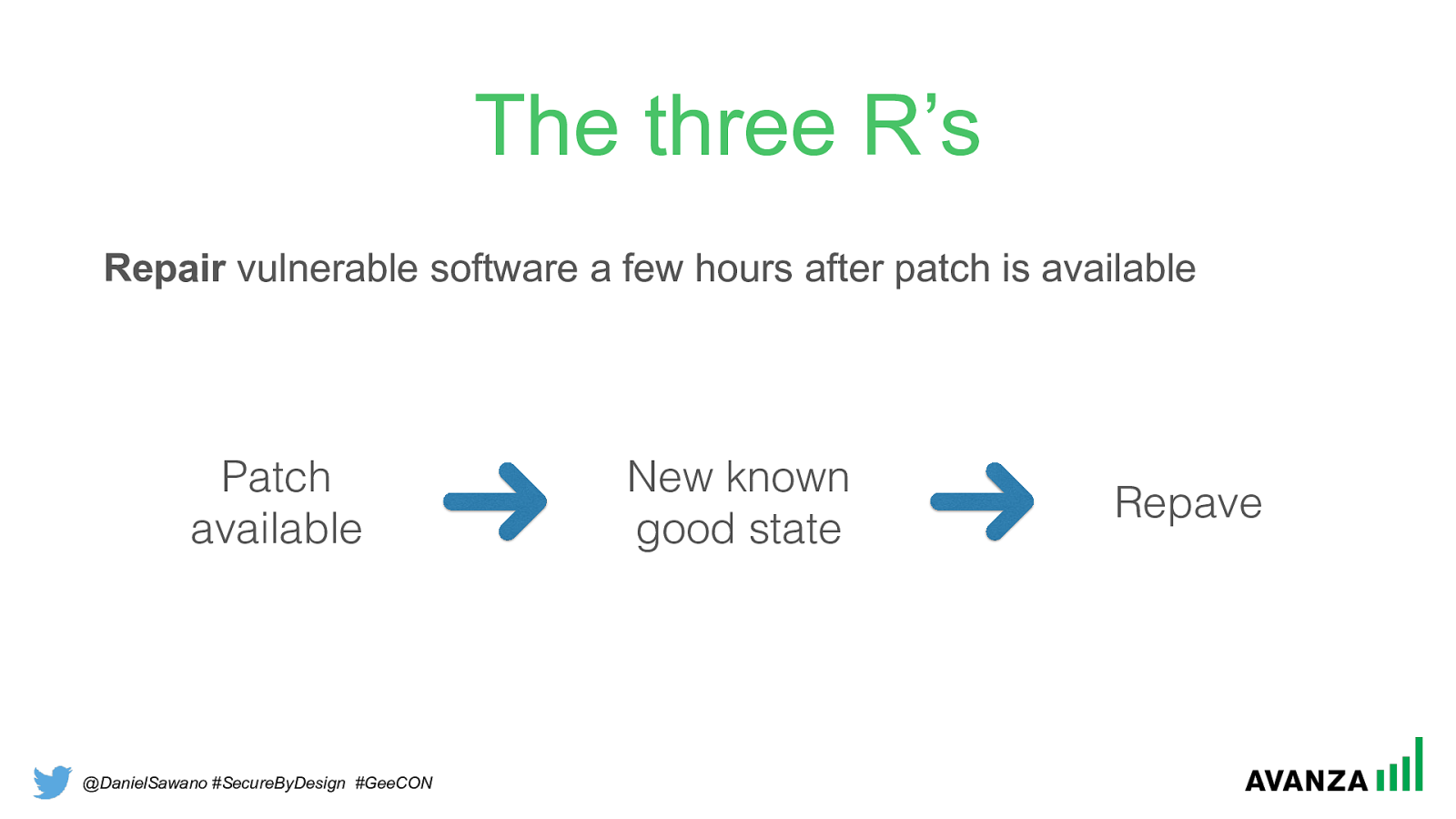
@DanielSawano #SecureByDesign #GeeCON The three R’s Repair vulnerable software a few hours after patch is available Patch available New known good state Repave
@DanielSawano #SecureByDesign #GeeCON The three R’s • Applies to both operating systems and yo ur o w n applications • No incremental updates, repave instead • CI/CD enables you to repair your own applications • Don’t forget 3rd party dependencies Repair vulnerable software a few hours after patch is available

@DanielSawano #SecureByDesign #GeeCON The three R’s Ever-changing software is the nemesis of persistent threats
@DanielSawano #SecureByDesign #GeeCON Summary ✓ Configuration ✓ Separate processes ✓ Logging ✓ The three R’s of enterprise security

bit.ly/secure-by-design Manning Publication

@DanielSawano #SecureByDesign #GeeCON Q&A [2]

Daniel Sawano Kraków, 9-11 May 2018 Thanks!